Enterprises are embracing on-demand from customers freelance help — but the observe, while developing, opens up solely new avenues of cyber-risk.
As organizations attempt to go faster and speedier, many are adopting a “just-in-time” technique of spinning up human sources on desire – a phenomenon acknowledged as the gig economy, familiar to most by way of Uber, Instacart or DoorDash. But it’s a thought that enterprises are embracing also – inadvertently building a brand-new insider-danger attack vector that can have dire consequences for information security.
“Your attack surface area is changing,” explained James Christiansen, vice president of information risk management at Netskope. “Gig-economic climate staff are normally incredibly brief-expression employees, they are coming in and they are heading out, and they are carrying out specialty varieties of activities – so they’re diverse than deal workers. They are most generally heading to be making use of their individual laptops and their individual collaboration instruments, and they’re likely to take your details, and most likely set it in their storage.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Speaking from the phase this 7 days at the RSA Conference 2021, he encapsulated the problem with the accurate story of “Bob,” a freelancer who outsourced his personal gig.
A Gig Risk Profile: Outsourcing the Outsourced
Bob, an software programmer, was “on call” for many corporations to punch up their code when required. He was undertaking really effectively for himself, much too, earning a 6-figure earnings across the several firms he assisted. In actuality, he was doing so properly that he imagined it was completely sensible to just take some of that revenue and use it to outsource his personal programming job to an group in China.
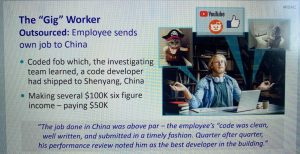
Bob outsourced his personal outsourced work. Click on to enlarge. Supply: Netskope.
“The organization experienced place in two-factor authentication,” Christiansen defined. “So he mailed them his vital fob. And they were actually logging in every single working day, doing his coding. The do the job was cleanse and well-created and submitted in a timely trend and then all-around that five o’clock he’d email his update to his administration workforce, and that would be it.”
Obviously, Bob was scamming the process but not intentionally seeking to purloin enterprise data. But sharing that code, which could have been proprietary, with an outdoors entity offers a handful of different problems. For 1, it could be stolen and marketed to a competitor two, sub-freelancer business could introduce destructive backdoors into the code, unbeknownst to any individual and three, the absence of visibility into who can entry the code signifies it could conclusion up in an open-resource repository somewhere, disallowing a firm to recoup its financial investment and killing a opportunity aggressive benefit.
“If you put in possibly $100,000 in building a new regimen, and a person uploads it to GitHub, it may perhaps be used as an open up-system resource the really next working day,” Christiansen explained. “So feel about the reduction of that investment in your R&D, most likely enabling your competition to go faster.”
The identical risks can be illustrated with other types of organization details, far too. For instance, aggressive sector examination is a variety of research which is often performed by gig workers, Christiansen pointed out. It is occupied function on some levels, but it requires the compilation of delicate company info, this sort of as pricing schedules, discount rates, data on channel and supplier relationships, compensation and fee rates, lists of the best salespeople, prospective clients and clients, request for proposal terms, earnings margins and much more.
Apart from the probable for breaking the chain of data custody with unauthorized knowledge sharing, other knowledge-security risks related with gig employees involve the skill for them to tumble prey to cyberattacks, given that they are normally operating outside the house of the business security footprint, he included.
Controlling Knowledge Risk in the Gig Financial state
The initial action in taking care of gig-economic system risk is performing a secondary risk assessment, in accordance to Christiansen.

Click to enlarge. Source: Netskope.
“You’ve most likely now finished a ‘crown-jewels’ evaluation, so you know in which the important things is,” he stated. “But you need to have to reassess what would seriously be critical to the firm in these instances where by we may well be applying freelance support. What can these employees do? Can they copy that code, entry pricing information, entry promoting info? We want to understand the impression of that facts must it leak out, if it’s utilized for a single of our competition or if it results in being community expertise.”
Once that risk assessment is completed, companies can use it to tell the controls they put in spot and to build a security plan, he included, which must consist of administrative controls, course of action controls and tech controls:
- Administrative Controls:
- Contractual Methods
- Have a Gig-Worker Exit Strategy
- Procedure Controls: Checking
- Tech Controls: Zero-Belief Tactics
Administrative Controls: Contractual Ways
Businesses must have crystal clear demands for gig employees, which can and must be put into a agreement. These should really go over how staff guard the methods they use to execute the get the job done, any opportunity liabilities and costs associated with that, limits on Bob-like outsourcing, breach-notification necessities, a consent to be monitored – and fiscal penalties for not adhering to the agreement.
“You can require them to have encryption on their laptops and antivirus application and all those typical issues, and you will need to feel about who’s heading to make confident that receives finished,” Christiansen explained. “Include any security safeguards you want in position, and specify how they use applications. Can they outsource the operate you have offered to them? It all requires to be specified.”
The deal really should also include implications if gig employees really don’t fulfill security controls. For occasion, corporations could reserve the right to withhold 10 to 20 percent of their payment – or not spend at all – if the demands aren’t in position and carried through.
Christiansen reported that breach notification is frequently a contractual time period that will get ignored, but he famous that it’s critical.
“If for some reason, the delicate data you have supplied them is then compromised or shared inappropriately, you will need to make positive that they notify you in a well timed way mainly because you have an obligation you to the firm, prospects and some others,” he observed.
Administrative Controls: Have a Gig-Employee Exit Tactic
The other component of the administrative equation is the exit approach – what happens when a gig worker wraps a two-day or two-7 days extensive engagement?
“Just like a very good relationship, you have to assume about how you are going to split up,” Christiansen described. “What are your expectations all-around deleting info, returning knowledge, archiving facts and so on? Make positive that exit approach has been thought by means of, and they’ve agreed to it, and make sure you stick to by on it at the conclusion.”
This also incorporates of course shifting any qualifications, switching off profiles for collaboration equipment and eradicating entry to any again-conclusion methods.
Method Controls: Monitoring
Contracts are wonderful for legal legal responsibility uses, but the challenging part is locating out if the conditions have been adopted.
The distinct respond to to this conundrum, in accordance to Christiansen, is monitoring (with the worker’s consent, of course). It is a typical practice within just the enterprise footprint for whole-time personnel, but it turns into a little bit trickier for freelance personnel.
“The plan is to glance at behavioral activity and record any anomalies,” he described. “If you see that generally they’re doing work on sure files, and it’s intense in which because a gig employee is pretty focused, but all of a sudden they’re likely on- and offline repetitively, that can be simply because they’re doing the job one more gig on their pc and they have to signal off our technique. So consider about the designs.”
Checking can also be utilized to enjoy for software risk – a widespread issue with gig-economic system employees, who may well be mixing personalized and function actions.
“Are they using purposes that may well be resulting in risk? Are they storing data in a area they should not be storing it? Application instance awareness is absolutely important,” in accordance to Christiansen. “If you have acquired Business office 365 or G Suite, you require to be equipped to see if personnel are accessing a small business variation or personal model. Typical secure web gateways just cannot notify the distinction. We require to preserve it limited to only corporate-accepted web sites.”
It’s feasible far too to pop up alerts when a user goes to a rogue spot software, he added – a method he claimed is an option for coaching.
“I can say, ‘what you’re about to do is superior risk,’” he stated. “‘Please enter a justification for doing this.’ And 95 per cent of the time, they’ll back again out, for the reason that they know you are looking at them, and you just educated them on in which should be heading.”
Technological Controls: Zero-Have confidence in Tactics
The remaining piece of the puzzle, which can be used in tandem or in place of monitoring endeavours, is the software of technology that will make it impossible for data to be shared inappropriately.
“Data security now need to be performed in a zero-belief planet,” Christiansen reported. “We never have faith in wherever computer systems are coming from because they are BYOD we never belief the network because it’s not just one we control necessarily we’re working with cloud and it’s managing on machines that we do not individual. We’re working with SaaS purposes. But there are some tactical things we can do for the gig employee or the freelancer.”
For occasion, virtual desktop infrastructure (VDI), pioneered by Citrix but now readily available from a selection of distributors, centralizes applications and details on a shared server, which is accessed by thin (or “dumb”) shopper workstations that aren’t on their own connected to the internet or other means. There’s no capability to obtain files or save just about anything exterior of the company-owned central repository, so personnel just cannot share info exterior of the organization.
“None of the details truly ever goes to that desktop,” Christiansen explained. “So thus, all of these threats about details staying copied off or reused or screenprinted, and so on., go absent.”
Yet another choice is remote browser isolation RBI), which is a related thought that applies only to steps that just take area by means of a browser.
“It can make a great deal of perception simply because you do not have to virtualize the entire equipment, simply because they are functioning remotely – but I can make certain they can not consider anything at all out of my G Travel or my SharePoint. I can consist of knowledge there, and protect against it from acquiring outside the house of that browser to a worker’s fundamental desktop.”
A third alternative to bolster data risk administration or details legal rights management in is to use encrypted information.
“These documents require authorization at time of use,” he discussed. “I can email it to anyone and they can open it if they have the ideal credentials, but if they email it to anyone else, that man or woman just can’t open up it. So, it’s not like a file that can be leaked out and get into the incorrect palms.”
Overall, the strategy is to embrace the bold new gig-financial system way of doing the job – but it is vital to recognize the info threats and danger that will come with the territory.
“The gig economy is below to continue to be, so lean into it, it is not a fad,” Christiansen concluded. “But that gig-worker route represents a significant risk. So, believe about your out there security techniques and your general system, and recall that essential to any productive security software is knowledge your tradition, what is satisfactory what isn’t suitable. And remember that we have received additional information likely outside the house of our corporations these days than what is getting despatched close to inside.”
Download our special Cost-free Threatpost Insider E book, “2021: The Evolution of Ransomware,” to aid hone your cyber-protection tactics against this expanding scourge. We go over and above the status quo to uncover what is upcoming for ransomware and the similar emerging risks. Get the whole story and Download the E book now – on us!

Some parts of this article are sourced from:
threatpost.com


 #RSAC: What Makes a Security Program Measurably More Successful?
#RSAC: What Makes a Security Program Measurably More Successful?