Both cryptocurrency and ransomware are absolutely nothing new in the digital world equally have been there for a extremely long time, which was ample for them to uncover prevalent parts for commencing their marriage.
Ransomware can be like a virtual vehicle that performs on all forms of fuels, and crypto is the one that is at present most suggested. No a single can argue that 2020 was the 12 months of ransomware in the cyber planet, but it was not because of to the point that cybercriminals selected ransomware just since they knew how to attack properly. It is due to the fact of the fact that crypto rose mainly this 12 months, along with the new standard of the digital entire world. It gave them a new lead to to adhere to ransomware, many thanks to the nameless payments that can be manufactured working with a cryptocurrency.
How does ransomware work?
Ransomware is a malware kind that encrypts the victim’s files, regardless of whether it is a random person or an firm, leading to denying them access to people documents on their particular equipment.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
And the critical to getting access is to pay out the ransom to the attacker.
How is cryptocurrency helping spread ransomware?
Now we all know that all crypto transactions are untraceable for both receiver and sender, which we call a full anonymous transaction. The increased desire for crypto in new decades built it less complicated to get and offer all those virtual cash and get genuine income.
With that getting claimed, cryptocurrency grew to become the most most well-liked way (if not the finest) for cybercriminals to get their ransom with out being traced and give those corporations obtain to their documents.
How to stay clear of participating in ransomware parties?
Most posts on the internet instruct you the actions on how to give the ransom to the criminals with the minimum amount losses and with no building problems to make absolutely sure you get your information again. But the concern is, why do you have to have to discover how to make payments to a prison when you can keep away from assembly them and their viruses in the very first position?
There are a number of methods where each provides you a generous percentage of security.
Starting with using cybersecurity recognition coaching programs which we get in touch with the best layer of safety, adopted by multilayers these kinds of as the initially and most precious layer that works on the DNS degree, which is the initial gate between you and the cybercriminal.
A Robust DNS security would just transform your wheel each individual time you try out to operate by a web page that incorporates viruses. It would also block all crypto and mining internet sites at which most hackers party at.
Any examples?
Certainly.
DarkSide ransomware. Its lively operations took put in 2020. Its key attribute was that it not only encrypted the victim’s facts but also deleted it from the affected servers. This is 1 of the characteristic characteristics of this sort of threats.
In significantly less than a 12 months of perform, about $ 100 million were paid in bitcoins. The extortionists acquired about $10 million by attacking only two organizations.
The Brenntag company distributes chemicals. In this scenario, the DarkSide partners in criminal offense explained they had received access to the network after acquiring stolen information and facts but did not know how the credentials ended up acquired to commence with. The enterprise paid out a $4.4 million ransom in cryptocurrency. Pursuing the ransom payment, Brenntag obtained a decryptor for encrypted data files and properly stopped the cybercriminals from building the firm’s stolen data public.
The 2nd enterprise is Colonial Pipeline. The Colonial Pipeline is the premier pipeline procedure for refined oil goods in the U.S. Just after understanding it was “the victim of a cybersecurity attack,” the pipeline operator took some methods offline, quickly halting pipeline functions and many IT techniques. It also contacted an outside cybersecurity agency to conduct an investigation. At last, they paid out the hackers nearly $5 million in cryptocurrency in return for a decryption critical to restore its systems.
Conti Ransomware. The main victims of this extortion were being healthcare establishments. Its common methods use phishing attacks to obtain remote access to a laptop and even more unfold on the network while at the same time stealing qualifications and collecting unencrypted data. And the most renowned attack was the attack on Ireland’s Health and fitness Assistance Govt, in the course of which the gang ransomed about $ 20 million in cryptocurrency for non-disclosure of the info acquired.
How to acquire safety?
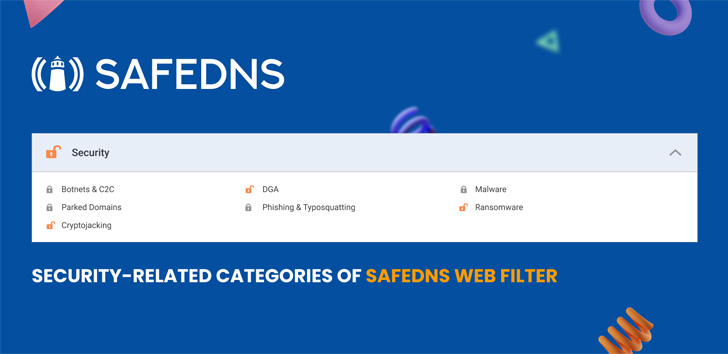
SafeDNS has up-to-date types owning DGA, Cryptojacking and some others as part of the Security team, and we undoubtedly advise hoping out risk protection & providing a totally free 15-working day demo of web filtering a go. Keep secure!
Identified this post appealing? Adhere to THN on Fb, Twitter and LinkedIn to go through a lot more special written content we article.
Some pieces of this report are sourced from:
thehackernews.com


 Wine Merchant Among Aussie Firms Breached, Exposing Millions
Wine Merchant Among Aussie Firms Breached, Exposing Millions