As several as 350,000 open up supply jobs are thought to be potentially susceptible to exploitation as a outcome of a security flaw in a Python module that has remained unpatched for 15 a long time.
The open up source repositories span a number of business verticals, these as software program growth, synthetic intelligence/machine studying, web progress, media, security, IT administration.
The shortcoming, tracked as CVE-2007-4559 (CVSS rating: 6.8), is rooted in the tarfile module, effective exploitation of which could guide to code execution from an arbitrary file produce.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

“The vulnerability is a route traversal attack in the extract and extractall functions in the tarfile module that make it possible for an attacker to overwrite arbitrary documents by introducing the ‘..’ sequence to filenames in a TAR archive,” Trellix security researcher Kasimir Schulz reported in a writeup.
Originally disclosed in August 2007, the bug has to do with how a specially crafted tar archive can be leveraged to overwrite arbitrary information on a target machine only on opening the file.
Place just, a risk actor can exploit the weakness by uploading a malicious tarfile in a manner that makes it achievable to escape the listing that a file is supposed to be extracted to and reach code execution, letting the adversary to potentially seize handle of a target unit.
“Hardly ever extract archives from untrusted resources without having prior inspection,” the Python documentation for tarfile reads. “It is achievable that information are produced outside the house of path, e.g. customers that have complete filenames commencing with “https://thehackernews.com/” or filenames with two dots ‘..’.”

The vulnerability is also reminiscent of a lately disclosed vulnerability in RARlab’s UnRAR utility (CVE-2022-30333) that could lead to distant code execution.
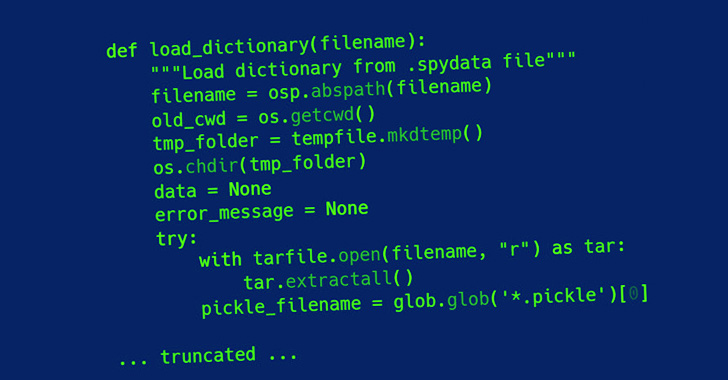
Trellix has more introduced a tailor made utility named Creosote to scan for projects vulnerable to CVE-2007-4559, applying it to uncover the vulnerability in the Spyder Python IDE as nicely as Polemarch.
“Remaining unchecked, this vulnerability has been unintentionally added to hundreds of countless numbers of open up- and shut-source initiatives globally, producing a considerable application provide chain attack surface area,” Douglas McKee noted.
Located this posting intriguing? Adhere to THN on Facebook, Twitter and LinkedIn to study extra exceptional content material we put up.
Some components of this report are sourced from:
thehackernews.com

 Authorized Push Payments Surge to 75% of Banking Fraud
Authorized Push Payments Surge to 75% of Banking Fraud