A high-severity vulnerability has been disclosed in the SQLite databases library, which was introduced as part of a code modify dating all the way back again to Oct 2000 and could allow attackers to crash or control programs.
Tracked as CVE-2022-35737 (CVSS score: 7.5), the 22-12 months-previous issue affects SQLite versions 1..12 as a result of 3.39.1, and has been dealt with in edition 3.39.2 produced on July 21, 2022.
“CVE-2022-35737 is exploitable on 64-little bit units, and exploitability is dependent on how the program is compiled,” Trail of Bits researcher Andreas Kellas explained in a specialized produce-up posted now.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Arbitrary code execution is verified when the library is compiled devoid of stack canaries, but unconfirmed when stack canaries are current, and denial-of-company is verified in all instances.”
Programmed in C, SQLite is the most commonly employed databases engine, included by default in Android, iOS, Windows, and macOS, as nicely as well-known web browsers this sort of as Google Chrome, Mozilla Firefox, and Apple Safari.
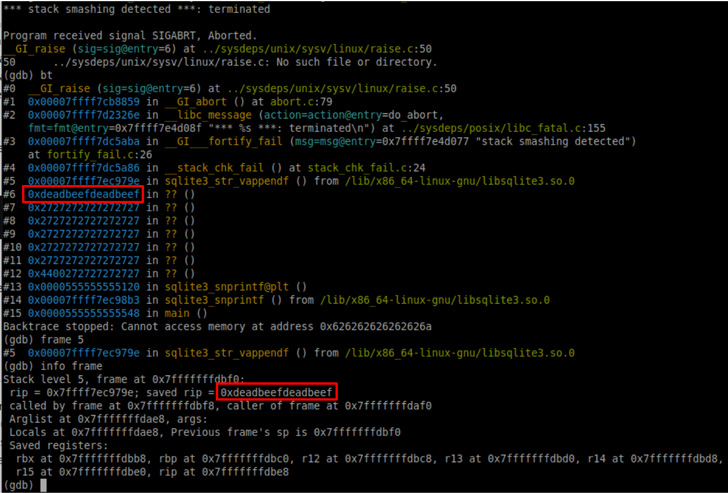
The vulnerability uncovered by Path of Bits considerations an integer overflow bug that happens when incredibly significant string inputs are passed as parameters to the SQLite implementations of the printf capabilities, which, in turn, make use of one more function to take care of the string formatting (“sqlite3_str_vappendf”).

Nonetheless, a productive weaponization of the flaw banks on the prerequisite that the string contains the %Q, %q, or %w structure substitution styles, possibly primary to a software crash when person-controlled facts is written past the bounds of a stack-allotted buffer.
“If the format string has the ‘!’ special character to empower unicode character scanning, then it is achievable to achieve arbitrary code execution in the worst situation, or to induce the application to hold and loop (approximately) indefinitely,” Kellas stated.
The vulnerability is also an illustration of a state of affairs that was after considered impractical many years in the past — allocating 1GB strings as input — rendered possible with the advent of 64-bit computing devices.
“It is really a bug that may not have seemed like an mistake at the time that it was published (courting again to 2000 in the SQLite supply code) when systems have been mainly 32-bit architectures,” Kellas reported.
Found this posting attention-grabbing? Stick to THN on Facebook, Twitter and LinkedIn to go through additional distinctive information we article.
Some parts of this short article are sourced from:
thehackernews.com


 Database and big data security
Database and big data security