A security flaw has been unearthed in Microsoft’s Azure Application Service that resulted in the publicity of supply code of shopper applications penned in Java, Node, PHP, Python, and Ruby for at minimum 4 yrs given that September 2017.
The vulnerability, codenamed “NotLegit,” was described to the tech large by Wiz scientists on Oct 7, 2021, following which mitigations have been carried out to deal with the information and facts disclosure bug in November. Microsoft stated a “constrained subset of prospects,” adding “Clients who deployed code to Application Company Linux by using Regional Git right after information ended up currently designed in the application were being the only impacted prospects.”


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The Azure Application Provider (aka Azure Web Apps) is a cloud computing-based mostly system for developing and hosting web applications. It makes it possible for consumers to deploy resource code and artifacts to the company utilizing a nearby Git repository, or by using repositories hosted on GitHub and Bitbucket.
The insecure default actions occurs when the Community Git approach is used to deploy to Azure App Assistance, ensuing in a scenario where the Git repository is produced inside a publicly obtainable listing (property/website/wwwroot).
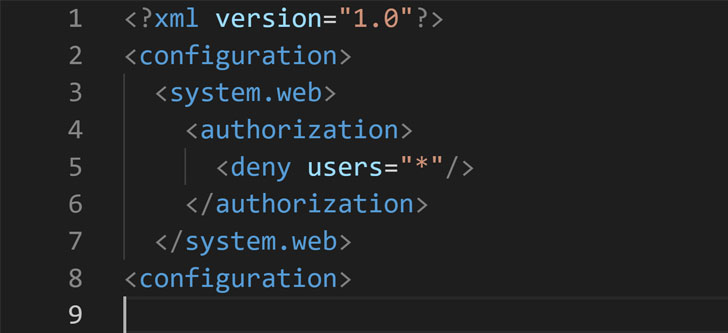
Whilst Microsoft does incorporate a “web.config” file to the .git folder — which is made up of the point out and background of the repository — to limit public obtain, the configuration files are only made use of with C# or ASP.NET apps that depend on Microsoft’s very own IIS web servers, leaving out apps coded in other programming languages like PHP, Ruby, Python, or Node that are deployed with various web servers like Apache, Nginx, and Flask.
“In essence, all a malicious actor had to do was to fetch the ‘/.git’ listing from the focus on application, and retrieve its supply code,” Wiz researcher Shir Tamari stated. “Destructive actors are continuously scanning the internet for exposed Git folders from which they can obtain tricks and mental home. Apart from the risk that the supply incorporates secrets and techniques like passwords and access tokens, leaked resource code is generally used for even more subtle attacks.”
“Locating vulnerabilities in program is a great deal much easier when the source code is readily available,” Tamari extra.
Found this posting attention-grabbing? Adhere to THN on Fb, Twitter and LinkedIn to read through far more exclusive content we article.
Some sections of this short article are sourced from:
thehackernews.com


 Researchers Disclose Unpatched Vulnerabilities in Microsoft Teams Software
Researchers Disclose Unpatched Vulnerabilities in Microsoft Teams Software