Cybersecurity now matters so a great deal since of everyone’s dependence on technology, from collaboration, conversation and amassing data to e-commerce and entertainment. Every organisation that requirements to provide expert services to their shoppers and workforce must secure their IT ‘network’ – all the apps and related gadgets from laptops and desktops to servers and smartphones.
While usually, these would all reside on 1 “company network,” – networks now are frequently just produced up of the equipment them selves, and how they’re connected: across the internet, at times by means of VPNs, to the houses and cafes people operate from, to the cloud and details centres the place products and services live. So what threats does this present day network encounter?
Let’s look at them in far more depth.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
#1 Misconfiguration
In accordance to modern analysis by Verizon, misconfiguration glitches and misuse now make up 14% of breaches. Misconfiguration problems arise when configuring a technique or application so that it is really a lot less protected. This can come about when you alter a location with no completely being familiar with the implications, or when an incorrect worth is entered. Possibly can develop a critical vulnerability – for instance, a misconfigured firewall can let unauthorized access to an internal network, or a wrongly configured web server could leak sensitive information.
#2 Out-of-date software package
Software and application developers frequently launch updates with patches to cover vulnerabilities that have been identified in their code. Implementing patches to fix these vulnerabilities across an organisation’s full network of units can be time-consuming and sophisticated to put into practice – but it is necessary. If you you should not update your application, firmware and operating methods to the most up-to-date variations as they’re introduced, you are leaving your network exposed. A vulnerability scanner will give you a true-time stock of all the computer software which demands updating, as properly as detect misconfigurations that decrease your security, so you can continue to be as protected as attainable.
#3 DoS attack
The former two threats are commonly exploited to breach networks and steal data, but a Denial-of-Services (DoS) attack is meant to shut down your network and make it inaccessible.
This can be done by many means, both with malware, or by flooding the concentrate on network with website traffic, or sending information that triggers a crash these kinds of as requesting overly complex queries that lock up a databases. In each case, the DoS attack prevents prospects or staff members from using the provider or methods they count on.
DoS attacks normally concentrate on internet websites of significant-profile organisations this sort of as banking companies, media providers and governments. Though DoS attacks you should not normally consequence in the theft or reduction of facts, they can value you a wonderful offer of time and cash to handle. A correctly configured articles delivery network (CDN) can support safeguard internet websites in opposition to DoS attacks and other prevalent destructive attacks.
#4 Software bugs
A program bug is an error, flaw or fault in an application or technique that triggers it to make an incorrect or surprising end result. Bugs exist in each and every piece of code for all kinds of factors, from inappropriate screening or messy code to a lack of interaction or inadequate requirements files.
Not all bugs are cyber security issues or vulnerable to exploitation exactly where an attacker can use the fault to accessibility the network and run code remotely. Having said that, some bugs like SQL injection can be very serious, and enable the attackers to compromise your website or steal information. Not only do SQL injections leave delicate information exposed, but they can also empower remote accessibility and handle of influenced units. This is just just one example of a variety of application bug, but there are many some others.
Injections are popular if builders have not had adequate security coaching, or wherever faults are produced and not code reviewed – or when blended with inadequate continual security tests. On the other hand, even when all these issues are done – problems can even now occur, which is why it is really nonetheless ranked as the #1 danger in the OWASP Prime 10 Web Application Security Challenges. Luckily, quite a few forms of injection vulnerabilities (and other application stage security bugs) can be detected with an authenticated web vulnerability scanner, and penetration testing for much more sensitive purposes.
#5 Attack surface area management
Can you safe your organization if you don’t know what internet-dealing with belongings you individual? Not correctly. Devoid of a entire and up-to-date stock of internet-going through assets, you really don’t know what expert services are offered and how attackers can try to get in. But keeping on top rated of them and guaranteeing that they are remaining monitored for weaknesses isn’t just a walk in the park as IT estates increase and evolve pretty much each day.
When businesses consider to doc their techniques, they typically rely on manually updating a very simple spreadsheet, but among configuration variations, new technologies, and shadow IT, they rarely know accurately what assets they individual or where by. But finding, monitoring, and safeguarding all these property is a critical element of powerful security for every business.
A vulnerability scanner is a dynamic, automatic tool that can preserve track of what is actually exposed to the internet, and limit just about anything that isn’t going to require to be there – like that previous Windows 2003 box everyone’s overlooked about, or a web server that a developer spun up for a rapid exam right before leaving the business…
It can also preserve a continuous view around your cloud accounts and mechanically include any new external IP addresses or hostnames as targets. And it can enable with ‘asset discovery’ when organizations will need help finding their IP addresses and domains that they will not even know about.
What does this mean for you?
Attackers use automated equipment to determine and exploit vulnerabilities and entry unsecured units, networks or knowledge – nonetheless large or little your organisation. Discovering and exploiting vulnerabilities with automatic equipment is easy: the attacks shown higher than are inexpensive, quick to perform and frequently indiscriminate, so every organisation is at risk. All it requires is just one vulnerability for an attacker to access your network.
Recognizing exactly where your vulnerabilities and weak points are is the initially and most critical move. If you spot your vulnerabilities early, you can handle them prior to an attacker can exploit them. A vulnerability scanner is a cloud-based mostly services that identifies security vulnerabilities in computer system devices, networks and software program. Vulnerability scanners deliver a continual provider that queries for network threats and vulnerabilities – every thing from weak passwords to configuration blunders or unpatched computer software – so you can handle them before attackers exploit them.
Vulnerability management built straightforward
Intruder’s network vulnerability scanner is run by field-foremost scanning engines employed by financial institutions and governments throughout the world. It really is capable of finding above 11,000+ vulnerabilities and focuses on what matters, conserving time with contextually-prioritised effects. Employing sound reduction, it only experiences actionable issues that have a legitimate effects on your security.
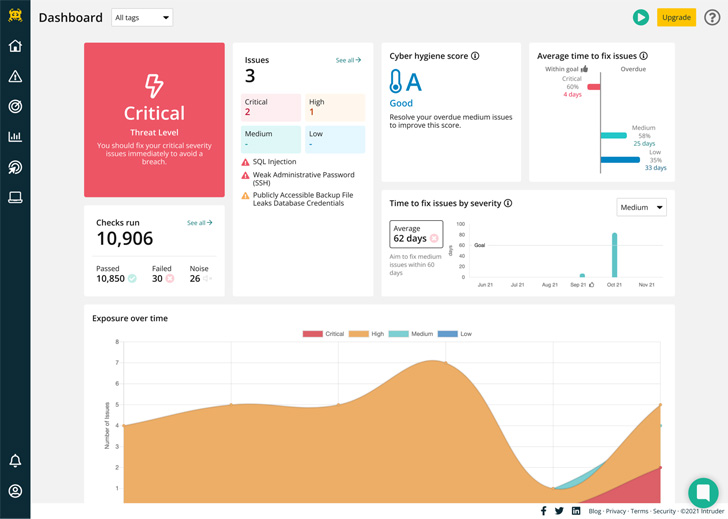 Intruder offers a 30-working day absolutely free trial of their vulnerability scanner
Intruder offers a 30-working day absolutely free trial of their vulnerability scanner
By scanning both your inner and exterior attack floor, Intruder screens your publicly and privately obtainable servers, cloud techniques, internet sites and endpoint devices. Much less targets for hackers imply much less vulnerabilities for you to fear about.
Organisations around the environment rely on Intruder’s vulnerability scanner to guard their networks with ongoing security checking and thorough scanning.
Located this posting interesting? Observe THN on Fb, Twitter and LinkedIn to examine a lot more unique content we put up.
Some pieces of this posting are sourced from:
thehackernews.com


 Google to Make Account Login Mandatory for Fitbit Users in 2023
Google to Make Account Login Mandatory for Fitbit Users in 2023