A previously undocumented Chinese-talking state-of-the-art persistent danger (APT) actor dubbed Aoqin Dragon has been connected to a string of espionage-oriented attacks aimed at authorities, instruction, and telecom entities mainly in Southeast Asia and Australia courting as far back as 2013.
“Aoqin Dragon seeks preliminary accessibility mostly as a result of document exploits and the use of fake detachable gadgets,” SentinelOne researcher Joey Chen mentioned in a report shared with The Hacker News. “Other methods the attacker has been observed making use of incorporate DLL hijacking, Themida-packed documents, and DNS tunneling to evade submit-compromise detection.”
The team is said to have some level of association with a further threat actor known as Naikon (aka Override Panda), with strategies largely directed against targets in Australia, Cambodia, Hong Kong, Singapore, and Vietnam.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Infections chains mounted by Aoqin Dragon have banked on Asia-Pacific political affairs and pornographic-themed doc lures as nicely as USB shortcut procedures to cause the deployment of a single of two backdoors: Mongall and a modified edition of the open up-resource Heyoka challenge.
This associated leveraging outdated and unpatched security vulnerabilities (CVE-2012-0158 and CVE-2010-3333), with the decoy files attractive targets into opening the information. Around the years, the threat actor also employed executable droppers masquerading as antivirus application to deploy the implant and link to a distant server.
“Despite the fact that executable information with faux file icons have been in use by a range of actors, it remains an efficient device specially for APT targets,” Chen stated. “Put together with ‘interesting’ email articles and a catchy file title, consumers can be socially engineered into clicking on the file.”
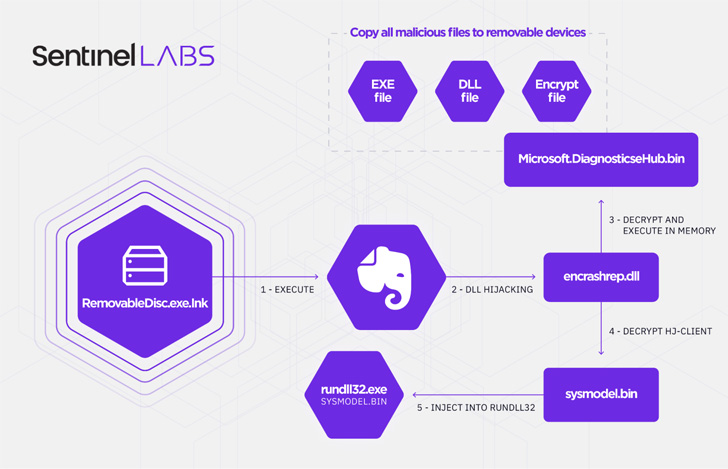
That reported, Aoqin Dragon’s latest original obtain vector of selection since 2018 has been its use of a faux detachable product shortcut file (.LNK), which , when clicked, runs an executable (“RemovableDisc.exe”) that athletics the icon for the preferred observe-getting application Evernote but is engineered to purpose as a loader for two different payloads.
One of the parts in the an infection chain is a spreader that copies all destructive information to other detachable units and the next module is an encrypted backdoor that injects alone into rundll32’s memory, a indigenous Windows procedure applied to load and operate DLL information.

Acknowledged to be used considering the fact that at the very least 2013, Mongall (“HJ-consumer.dll”) is explained as a not-so “especially aspect prosperous” implant but a single that packs plenty of functions to make a remote shell and upload and down load arbitrary documents to and from the attacker-control server.
Also made use of by the adversary is a reworked variant of Heyoka (“srvdll.dll”), a evidence-of-concept (PoC) exfiltration software “which employs spoofed DNS requests to make a bidirectional tunnel.” The modified Heyoka backdoor is much more potent, outfitted with abilities to generate, delete, and lookup for documents, develop and terminate processes, and assemble method data on a compromised host.
“Aoqin Dragon is an lively cyber espionage team that has been running for approximately a ten years,” Chen explained, including, “it is possible they will also go on to advance their tradecraft, locating new methods of evading detection and continue to be longer in their goal network.”
Uncovered this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read through much more exceptional articles we post.
Some pieces of this posting are sourced from:
thehackernews.com


 What is metaverse security?
What is metaverse security?