Microsoft is urging customers to patch two security vulnerabilities in Active Directory domain controllers that it dealt with in November pursuing the availability of a evidence-of-principle (PoC) device on December 12.
The two vulnerabilities — tracked as CVE-2021-42278 and CVE-2021-42287 — have a severity rating of 7.5 out of a highest of 10 and issue a privilege escalation flaw influencing the Energetic Directory Domain Providers (Ad DS) component. Credited with finding and reporting the two the bugs is Andrew Bartlett of Catalyst IT.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Active Listing is a directory service that runs on Microsoft Windows Server and is applied for identification and accessibility management. Whilst the tech big marked the shortcomings as “exploitation Fewer Probably” in its evaluation, the general public disclosure of the PoC has prompted renewed phone calls for making use of the fixes to mitigate any prospective exploitation by danger actors.
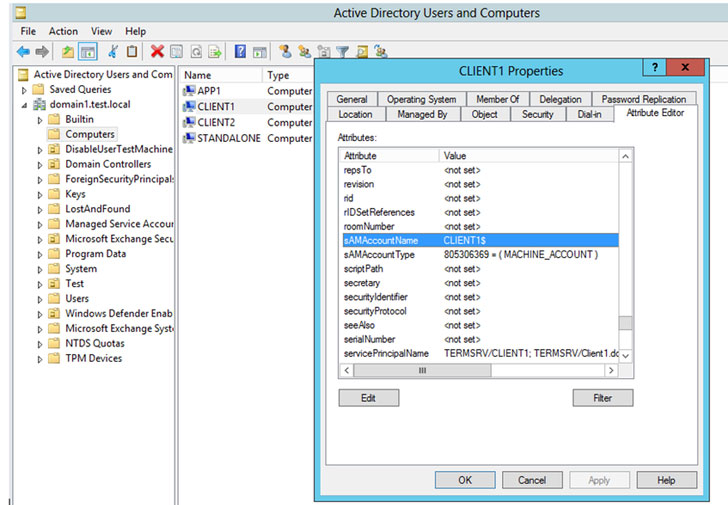
Whilst CVE-2021-42278 allows an attacker to tamper with the SAM-Account-Title attribute — which is utilised to log a user into devices in the Energetic Listing area, CVE-2021-42287 helps make it probable to impersonate the domain controllers. This properly grants a negative actor with domain person qualifications to achieve entry as a area admin consumer.
“When combining these two vulnerabilities, an attacker can make a simple route to a Area Admin consumer in an Energetic Directory environment that hasn’t used these new updates,” Microsoft’s senior product or service supervisor Daniel Naim mentioned. “This escalation attack enables attackers to conveniently elevate their privilege to that of a Domain Admin after they compromise a regular consumer in the domain.”
The Redmond-centered organization has also presented a move-by-action information to help buyers determine if the vulnerabilities could have been exploited in their environments. “As constantly, we strongly recommend deploying the newest patches on the domain controllers as quickly as doable,” Microsoft said.
Found this short article interesting? Follow THN on Fb, Twitter and LinkedIn to study additional exclusive articles we write-up.
Some pieces of this write-up are sourced from:
thehackernews.com



 Time to Ditch Big-Brother Accounts for Network Scanning
Time to Ditch Big-Brother Accounts for Network Scanning