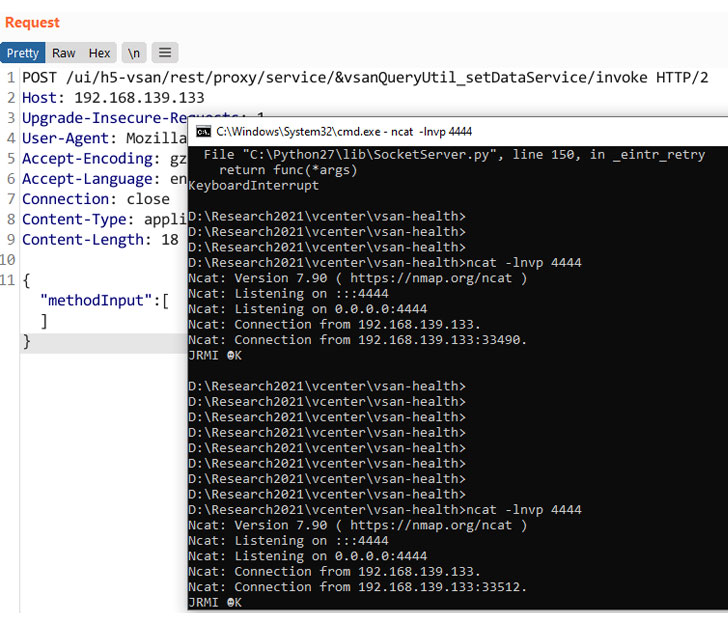
Malicious actors are actively mass scanning the internet for susceptible VMware vCenter servers that are unpatched versus a critical remote code execution flaw, which the enterprise dealt with late very last thirty day period.
The ongoing activity was detected by Lousy Packets on June 3 and corroborated yesterday by security researcher Kevin Beaumont. “Mass scanning action detected from 104.40.252.159 examining for VMware vSphere hosts susceptible to remote code execution,” tweeted Troy Mursch, chief investigate officer at Undesirable Packets.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The development follows the publication of a proof-of-notion (PoC) RCE exploit code concentrating on the VMware vCenter bug.
Tracked as CVE-2021-21985 (CVSS rating 9.8), the issue is a consequence of a lack of enter validation in the Digital SAN (vSAN) Wellness Test plug-in, which could be abused by an attacker to execute commands with unrestricted privileges on the underlying working technique that hosts the vCenter Server.
Even though the flaw was rectified by VMware on May possibly 25, the company strongly urged its prospects to implement the crisis adjust instantly. “In this period of ransomware it is safest to assume that an attacker is previously inside of the network someplace, on a desktop and possibly even in management of a consumer account, which is why we strongly suggest declaring an crisis change and patching as quickly as feasible,” VMware claimed.
This is not the very first time adversaries have opportunistically mass scanned the internet for vulnerable VMware vCenter servers. A very similar remote code execution vulnerability (CVE-2021-21972) that was patched by VMware in February turned the focus on of cyber danger actors trying to exploit and just take regulate of unpatched programs.
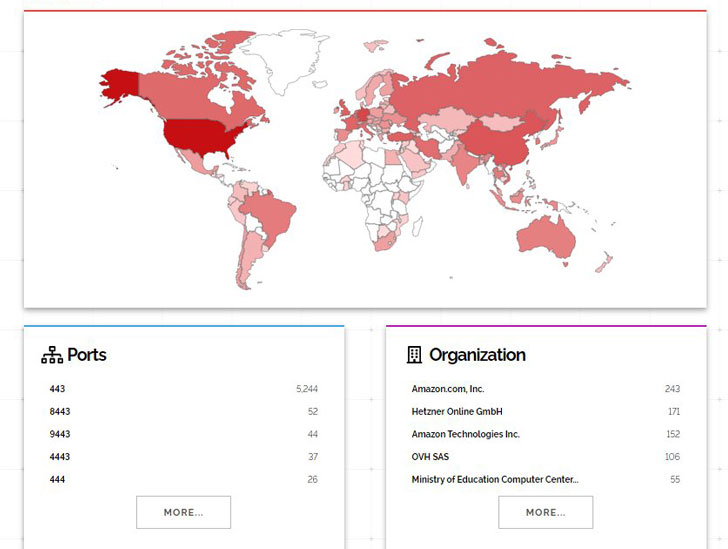
At least 14,858 vCenter servers ended up identified reachable more than the internet, according to Bad Packets and Binary Edge.
What is actually much more, a new study from Cisco Talos before this 7 days located that the threat actor guiding the Python-dependent Necro bot wormed its way into uncovered VMware vCenter servers by abusing the very same security weak spot to improve the malware’s an infection propagation abilities.
Found this short article interesting? Comply with THN on Fb, Twitter and LinkedIn to read through far more distinctive articles we article.
Some sections of this posting are sourced from:
thehackernews.com


 Employees rely too much on threat hunting teams to protect their own inboxes
Employees rely too much on threat hunting teams to protect their own inboxes