Cybersecurity scientists have taken the wraps off a new botnet hijacking Internet-linked intelligent devices in the wild to accomplish nefarious tasks, generally DDoS attacks, and illicit cryptocurrency coin mining.
Found by Qihoo 360’s Netlab security staff, the HEH Botnet — created in Go language and armed with a proprietary peer-to-peer (P2P) protocol, spreads by way of a brute-force attack of the Telnet assistance on ports 23/2323 and can execute arbitrary shell instructions.
The researchers explained the HEH botnet samples found out so far help a vast wide variety of CPU architectures, including x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III), and PowerPC (PPC).

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The botnet, regardless of getting in its early phases of improvement, comes with three purposeful modules: a propagation module, a neighborhood HTTP support module, and a P2P module.
Initially downloaded and executed by a malicious Shell script named “wpqnbw.txt,” the HEH sample then works by using the Shell script to obtain rogue applications for all distinct CPU architectures from a website (“pomf.cat”), ahead of at some point terminating a range of assistance procedures based on their port figures.
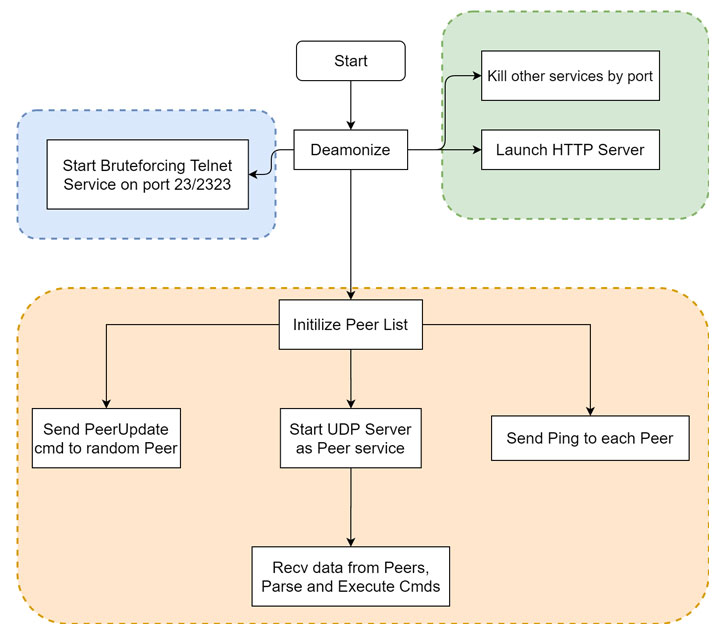
The second section commences with the HEH sample starting an HTTP server that displays the Common Declaration of Human Rights in 8 diverse languages and subsequently initializing a P2P module that retains observe of the contaminated friends and enables the attacker to operate arbitrary shell instructions, which includes the ability to wipe all facts from the compromised gadget by triggering a self-destruct command.
Other instructions make it probable to restart a bot, update the listing of friends, and exit the current jogging bot, despite the fact that an “Attack” command is but to be implemented by the botnet authors.
“Following the Bot runs the P2P module, it will execute the brute-force activity in opposition to the Telnet services for the two ports 23 and 2323 in a parallel fashion, and then finish its very own propagation,” the researchers stated.
In other phrases, if the Telnet company is opened on port 23 or 2323, it attempts a brute-power attack applying a password dictionary consisting of 171 usernames and 504 passwords. On a thriving break-in, the freshly contaminated victim is additional to the botnet, therefore amplifying it.
“The working mechanism of this botnet is not nevertheless mature, [and] some crucial features these types of as the attack module have not still been executed,” the researchers concluded.
“With that becoming claimed, the new and acquiring P2P composition, the numerous CPU architecture assistance, the embedded self-destruction characteristic, all make this botnet likely hazardous.”
Located this post fascinating? Stick to THN on Facebook, Twitter and LinkedIn to study a lot more exceptional material we article.
Some pieces of this short article are sourced from:
thehackernews.com


 Data: A resource much too valuable to leave unprotected
Data: A resource much too valuable to leave unprotected