The Amadey malware is being made use of to deploy LockBit 3. ransomware on compromised programs, researchers have warned.
“Amadey bot, the malware that is used to put in LockBit, is being dispersed through two solutions: just one working with a malicious Word doc file, and the other utilizing an executable that takes the disguise of the Phrase file icon,” AhnLab Security Emergency Reaction Middle (ASEC) claimed in a new report published nowadays.
Amadey, first found out in 2018, is a “prison-to-prison (C2C) botnet infostealer challenge,” as described by the BlackBerry Investigate and Intelligence Group, and is made available for obtain on the prison underground for as substantially as $600.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Though its main functionality is to harvest delicate facts from the infected hosts, it additional doubles up as a channel to provide upcoming-phase artifacts. Before this July, it was distribute applying SmokeLoader, a malware with not-so-different features like by itself.
Just last month, ASEC also identified the malware distributed less than the disguise of KakaoTalk, an immediate messaging provider well-liked in South Korea, as portion of a phishing campaign.
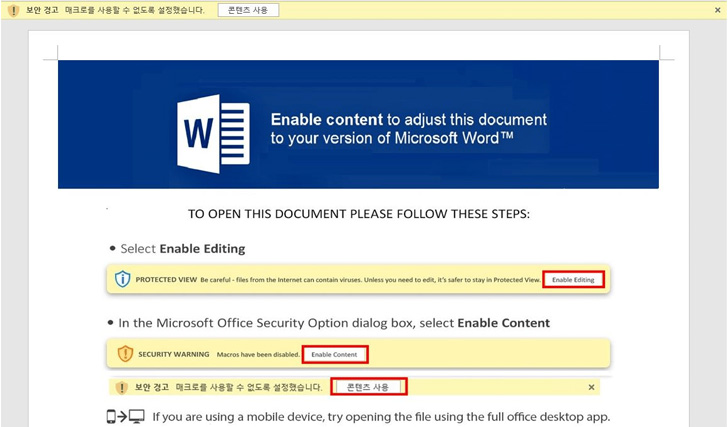
The cybersecurity firm’s most current examination is based mostly on a Microsoft Phrase file (“심시아.docx”) that was uploaded to VirusTotal on Oct 28, 2022. The doc incorporates a malicious VBA macro that, when enabled by the target, operates a PowerShell command to down load and run Amadey.
In an choice attack chain, Amadey is disguised as a seemingly harmless file bearing a Phrase icon but is essentially an executable (“Resume.exe”) which is propagated by means of a phishing information. ASEC reported it was not ready to establish the email utilized as a lure.

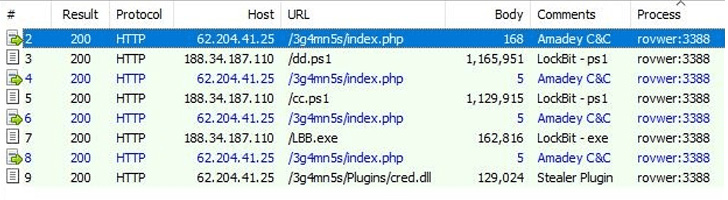
Succeeding in the execution of Amadey, the malware fetches and launches more instructions from a remote server, which includes the LockBit ransomware either in PowerShell (.ps1) or binary (.exe) formats.
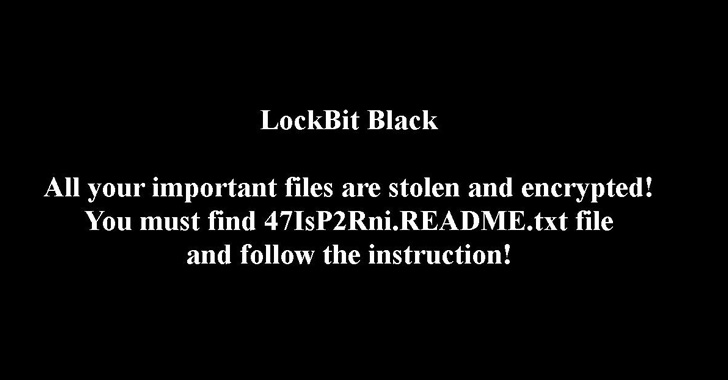
LockBit 3., also known as LockBit Black, released in June 2022, alongside a new dark web portal and the very initial bug bounty system for a ransomware procedure, promising rewards of up to $1 million for obtaining bugs in its web-site and computer software.
“As LockBit ransomware is remaining distributed via numerous methods, person caution is suggested,” the scientists concluded.
Found this short article fascinating? Abide by THN on Fb, Twitter and LinkedIn to go through a lot more special material we publish.
Some elements of this write-up are sourced from:
thehackernews.com

 New Laplas Clipper Malware Targeting Cryptocurrency Users via SmokeLoader
New Laplas Clipper Malware Targeting Cryptocurrency Users via SmokeLoader