The menace actor guiding the BlackRock and ERMAC Android banking trojans has unleashed nonetheless one more malware for hire called Hook that introduces new abilities to access information stored in the gadgets and develop a distant interactive session.
ThreatFabric, in a report shared with The Hacker News, characterized Hook as a novel ERMAC fork that is marketed for sale for $7,000 for every thirty day period although featuring “all the abilities of its predecessor.”
“In addition, it also provides to its arsenal Remote Access Tooling (RAT) capabilities, joining the ranks of family members such as Octo and Hydra, which are able performing a entire Product Take More than (DTO), and entire a whole fraud chain, from PII exfiltration to transaction, with all the intermediate steps, with no the need of added channels,” the Dutch cybersecurity agency stated.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
A bulk of the monetary applications specific by the malware are found in the U.S., Spain, Australia, Poland, Canada, Turkey, the U.K., France, Italy, and Portugal.
Hook is the handiwork of a danger actor regarded as DukeEugene and signifies the newest evolution of ERMAC, which was 1st disclosed in September 2021 and is centered on a different trojan named Cerberus that had its supply code leaked in 2020.
“Ermac has usually been powering Hydra and Octo in terms of abilities and capabilities,” ThreatFabric researcher Dario Durando told The Hacker Information by way of email. “This is also recognized amid danger actors, who prefer these two households above Ermac.”
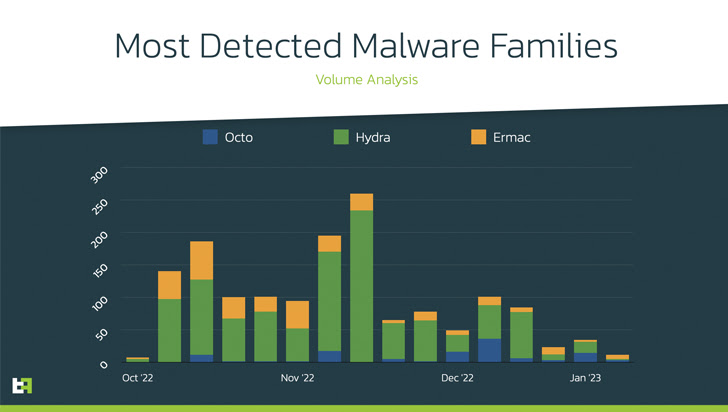
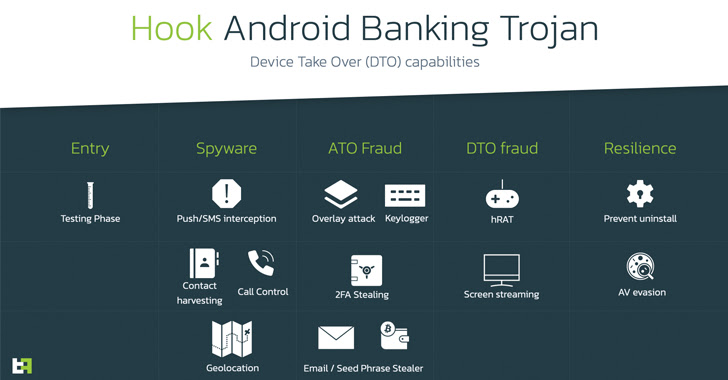
“The deficiency of some type of RAT abilities is a big issue for a contemporary Android Banker, as it does not offer the possibility to execute Product Consider More than (DTO), which is the fraud methodology that is most very likely to be prosperous and not detected by fraud scoring engines or fraud analysts. This is most very likely what brought on the improvement of this new malware variant.”
Like other Android malware of its ilk, the malware abuses Android’s accessibility expert services APIs to perform overlay attacks and harvest all types of delicate facts these kinds of as contacts, get in touch with logs, keystrokes, two-factor authentication (2FA) tokens, and even WhatsApp messages.
It also sporting activities an expanded listing of apps to include ABN AMRO and Barclays, while the destructive samples themselves masquerade as the Google Chrome web browser to dupe unsuspecting users into downloading the malware:
- com.lojibiwawajinu.guna
- com.damariwonomiwi.docebi
- com.yecomevusaso.pisifo
Amid the other big functions to be included to Hook is the capacity to remotely look at and interact with the monitor of the contaminated unit, attain data files, extract seed phrases from crypto wallets, and observe the phone’s area, blurring the line between spyware and banking malware.
ThreatFabric claimed the Hook artifacts noticed so considerably in a screening section, but noted it could be sent by means of phishing strategies, Telegram channels, or in the form of Google Perform Shop dropper apps.
“The primary downside of building a new malware is generally attaining sufficient believe in by other actors, but with the position of DukeEugene amid criminals, it is very probably that this will not be an issue for Hook,” Durando explained.
Uncovered this posting intriguing? Comply with us on Twitter and LinkedIn to read much more exceptional content we write-up.
Some components of this report are sourced from:
thehackernews.com

 New Research Delves into the World of Malicious LNK Files and Hackers Behind Them
New Research Delves into the World of Malicious LNK Files and Hackers Behind Them