The maintainers of the Apache Superset open resource information visualization software program have introduced fixes to plug an insecure default configuration that could direct to distant code execution.
The vulnerability, tracked as CVE-2023-27524 (CVSS rating: 8.9), impacts versions up to and which include 2..1 and relates to the use of a default Mystery_Crucial that could be abused by attackers to authenticate and entry unauthorized means on internet-exposed installations.
Naveen Sunkavally, the chief architect at Horizon3.ai, described the issue as “a unsafe default configuration in Apache Superset that makes it possible for an unauth attacker to attain distant code execution, harvest credentials, and compromise info.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
It is really worth noting that the flaw does not have an effect on Superset occasions that have adjusted the default worth for the Key_Critical config to a a lot more cryptographically secure random string.
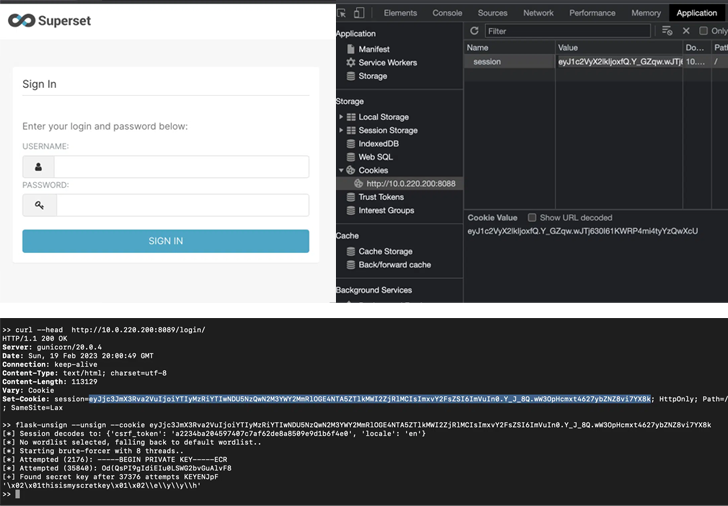
The cybersecurity organization, which discovered that the Key_Critical is defaulted to the price “x02x01thisismyscretkeyx01x02\e\y\y\h” at install time, reported that 918 out of 1,288 publicly-obtainable servers ended up making use of the default configuration in Oct 2021.
An attacker who experienced knowledge of the magic formula key could then indicator in to these servers as an administrator by forging a session cookie and seize control of the units.
On January 11, 2022, the undertaking maintainers attempted to rectify the dilemma by rotating the Key_Key value to “Change_ME_TO_A_Intricate_RANDOM_Magic formula” in the Python code together with consumer directions to override it.
Horizon3.ai mentioned it further uncovered two supplemental Mystery_Important configurations that ended up assigned the default values “USE_YOUR_Own_Protected_RANDOM_Key” and “thisISaSECRET_1234.”
An expanded search done in February 2023 with these 4 keys unearthed 3,176 circumstances, out of which 2,124 had been making use of 1 of the default keys. Some of these influenced consist of significant organizations, little businesses, govt companies, and universities.
Subsequent accountable disclosure to the Apache security staff a second time, a new update (version 2.1) was launched on April 5, 2023, to plug the security gap by avoiding the server from setting up up entirely if it really is configured with the default Top secret_Essential.
Impending WEBINARZero Have confidence in + Deception: Study How to Outsmart Attackers!
Explore how Deception can detect sophisticated threats, prevent lateral motion, and greatly enhance your Zero Believe in tactic. Be part of our insightful webinar!
Conserve My Seat!
“This resolve is not foolproof however as it is really nonetheless attainable to operate Superset with a default Top secret_Crucial if it really is mounted through a docker-compose file or a helm template,” Sunkavally explained.
“The docker-compose file incorporates a new default Magic formula_Crucial of Exam_NON_DEV_Key that we suspect some end users will unwittingly run Superset with. Some configurations also established admin/admin as the default credential for the admin consumer.”
Horizon3.ai has also made obtainable a Python script that can be employed to establish if Superset instances are prone to the flaw.
“It’s typically accepted that users really don’t examine documentation and programs ought to be developed to force people along a path exactly where they have no preference but to be safe by default,” Sunkavally concluded. “The ideal tactic is to take the alternative absent from people and call for them to take deliberate steps to be purposefully insecure.”
Found this article exciting? Observe us on Twitter and LinkedIn to study additional special written content we put up.
Some elements of this posting are sourced from:
thehackernews.com


 Quad Countries Prepare For Info Sharing on Critical Infrastructure
Quad Countries Prepare For Info Sharing on Critical Infrastructure