Apple on Monday rolled out security updates for iOS, macOS, tvOS, watchOS, and Safari web browser to deal with a number of vulnerabilities, including an actively exploited zero-working day flaw in macOS Large Sur and extend patches for two formerly disclosed zero-working day flaws.
Tracked as CVE-2021-30713, the zero-working day problems a permissions issue in Apple’s Transparency, Consent, and Management (TCC) framework in macOS that maintains a database of each user’s consents. The iPhone maker acknowledged that the issue could have been exploited in the wild but stopped small of sharing particulars.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The organization famous that it rectified the problem with improved validation.
Nonetheless, in a separate report, mobile gadget management company Jamf explained the bypass flaw was being actively exploited by XCSSET, a malware that’s been out in the wild considering that August 2020 and recognized to propagate by using modified Xcode IDE jobs hosted on GitHub repositories and plant malicious offers into reputable applications installed on the target technique.
“The exploit in issue could make it possible for an attacker to obtain Whole Disk Accessibility, Display screen Recording, or other permissions without necessitating the user’s specific consent — which is the default behavior,” Jamf researchers Stuart Ashenbrenner, Jaron Bradley, and Ferdous Saljooki reported in a produce-up.
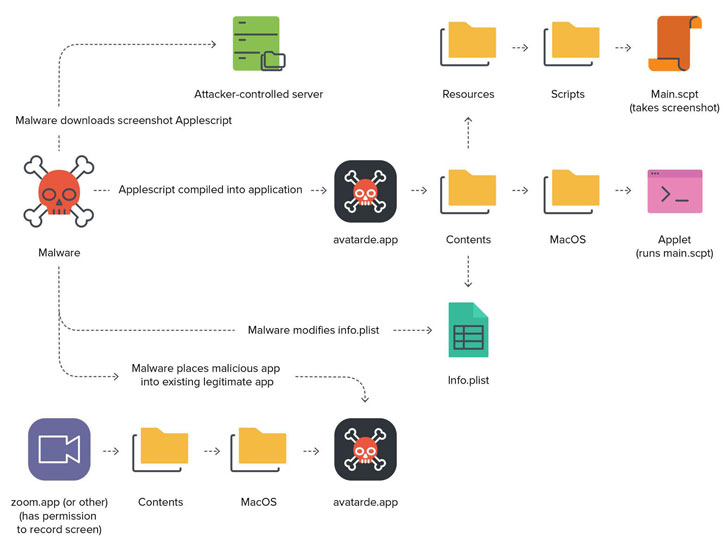
Taking the variety of a AppleScript module, the zero-day flaw authorized the hackers to exploit the units XCSSET was installed to leverage the permissions that have currently been delivered to the trojanized software to amass and exfiltrate delicate information and facts.
Especially, the malware checked for screen capture permissions from a listing of set up programs, this kind of as Zoom, Discord, WhatsApp, Slack, TeamViewer, Upwork, Skype, and Parallels Desktop, to inject the malware (“avatarde.app”) into the app’s folder, thereby inheriting the necessary permissions essential to carry out its nefarious responsibilities.
“By leveraging an installed application with the appropriate permissions set, the attacker can piggyback off that donor application when developing a destructive application to execute on target gadgets, devoid of prompting for consumer acceptance,” the researchers mentioned.
XCSSET was also the issue of nearer scrutiny past month right after a new variant of the malware was detected concentrating on Macs jogging on Apple’s new M1 chips to steal wallet facts from cryptocurrency applications. Just one of its main features is to siphon Safari browser cookies as effectively as install a developer model of the Safari application to load JavaScript backdoors from its command-and-control server.
Also set as part of Monday’s updates are two other actively exploited flaws in its WebKit browser motor impacting Safari, Apple Tv 4K, and Apple Television Hd products, virtually a few weeks soon after Apple tackled the similar issues in iOS, macOS, and watchOS earlier this month.
- CVE-2021-30663 – An integer overflow issue in WebKit, which could be exploited to accomplish arbitrary code execution when processing maliciously crafted web written content.
- CVE-2021-30665 – A memory corruption issue in WebKit that could guide to arbitrary code execution when processing maliciously crafted web material.
Customers of Apple equipment are proposed to update to the most current versions to mitigate the risk affiliated with the flaws.
Uncovered this short article exciting? Abide by THN on Fb, Twitter and LinkedIn to study a lot more exclusive information we article.
Some pieces of this article are sourced from:
thehackernews.com


 As market for cyber insurance booms, watchdog calls for better data
As market for cyber insurance booms, watchdog calls for better data