Apple has revised the security advisories it launched very last month to include things like three new vulnerabilities impacting iOS, iPadOS, and macOS.
The initially flaw is a race condition in the Crash Reporter component (CVE-2023-23520) that could enable a destructive actor to examine arbitrary documents as root. The iPhone maker reported it tackled the issue with more validation.
The two other vulnerabilities, credited to Trellix researcher Austin Emmitt, reside in the Basis framework (CVE-2023-23530 and CVE-2023-23531) and could be weaponized to reach code execution.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“An application might be capable to execute arbitrary code out of its sandbox or with specific elevated privileges,” Apple stated, adding it patched the issues with “improved memory handling.”
The medium to superior-severity vulnerabilities have been patched in iOS 16.3, iPadOS 16.3, and macOS Ventura 13.2 that were being delivered on January 23, 2023.
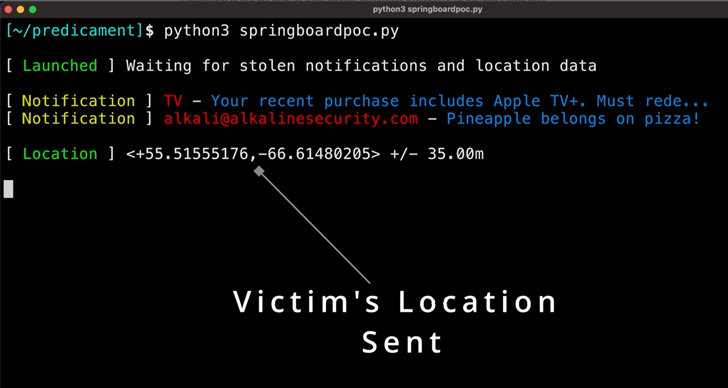
Trellix, in its personal report on Tuesday, categorized the two flaws as a “new class of bugs that make it possible for bypassing code signing to execute arbitrary code in the context of many system applications, major to escalation of privileges and sandbox escape on the two macOS and iOS.”
The bugs also bypass mitigations Apple set in put to address zero-click exploits like FORCEDENTRY that was leveraged by Israeli mercenary adware seller NSO Group to deploy Pegasus on targets’ gadgets.
As a end result, a menace actor could exploit these vulnerabilities to crack out of the sandbox and execute malicious code with elevated permissions, probably granting accessibility to calendar, tackle e book, messages, place data, connect with historical past, camera, microphone, and images.
Even a lot more troublingly, the security problems could be abused to install arbitrary applications or even wipe the machine. That claimed, exploitation of the flaws calls for an attacker to have by now acquired an preliminary foothold into it.
“The vulnerabilities previously mentioned signify a substantial breach of the security product of macOS and iOS which depends on individual applications owning high-quality-grained entry to the subset of means they need and querying greater privileged services to get just about anything else,” Emmitt reported.
Discovered this article intriguing? Stick to us on Twitter and LinkedIn to read much more distinctive content we write-up.
Some elements of this write-up are sourced from:
thehackernews.com


 Gartner: Nearly half of cyber leaders to leave roles over mounting stress
Gartner: Nearly half of cyber leaders to leave roles over mounting stress