The threat actor known as Asylum Ambuscade has been observed straddling cybercrime and cyber espionage operations considering the fact that at least early 2020.
“It is a crimeware group that targets lender shoppers and cryptocurrency traders in numerous regions, together with North The us and Europe,” ESET explained in an assessment printed Thursday. “Asylum Ambuscade also does espionage towards federal government entities in Europe and Central Asia.”
Asylum Ambuscade was 1st documented by Proofpoint in March 2022 as a country-condition-sponsored phishing campaign that targeted European governmental entities in an attempt to get intelligence on refugee and source motion in the region.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The aim of the attackers, for each the Slovak cybersecurity firm, is to siphon confidential info and web email credentials from official governing administration email portals.

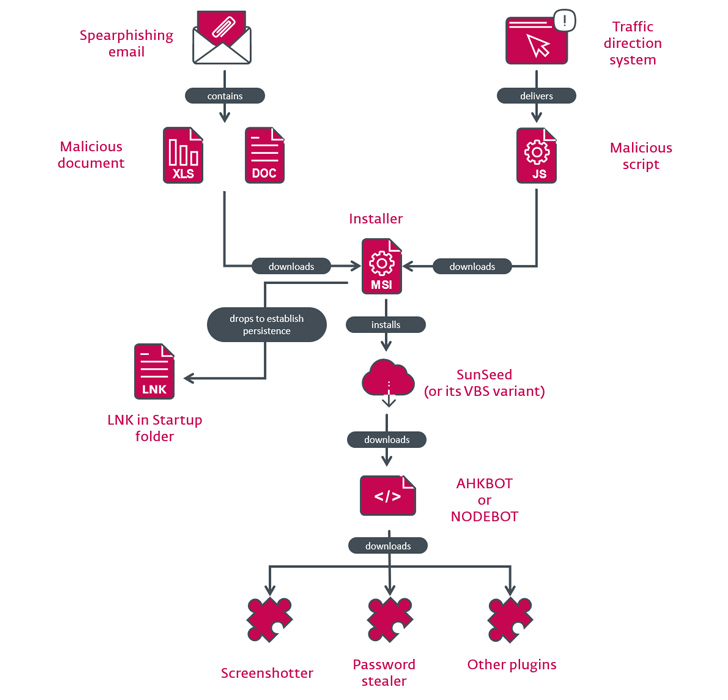
The attacks start off with a spear-phishing email bearing a destructive Excel spreadsheet attachment that, when opened, both exploits VBA code or the Follina vulnerability (CVE-2022-30190) to obtain an MSI package from a remote server.
The installer, for its part, deploys a downloader created in Lua named SunSeed (or its Visible Fundamental Script equivalent) that, in flip, retrieves an AutoHotkey-based malware identified as AHK Bot from a distant server.
What is noteworthy about Asylum Ambuscade is its cybercrime spree that has claimed over 4,500 victims across the environment considering the fact that January 2022, with a bulk of them situated in North The united states, Asia, Africa, Europe, and South The us.
“The concentrating on is incredibly vast and mainly incorporates men and women, cryptocurrency traders, and modest and medium corporations (SMBs) in several verticals,” ESET researcher Matthieu Faou said.
Whilst a single component of the attacks is built to steal cryptocurrency, the focusing on of SMBs is probably an attempt to monetize the access by promoting it to other cybercriminal groups for illicit earnings.
The compromise chain follows a very similar sample barring the first intrusion vector, which involves the use of a rogue Google Advertisement or a site visitors path process (TDS) to redirect potential victims to a bogus web page providing a malware-laced JavaScript file.
Future WEBINAR🔐 Mastering API Security: Comprehending Your Legitimate Attack Surface
Find out the untapped vulnerabilities in your API ecosystem and acquire proactive ways towards ironclad security. Be a part of our insightful webinar!
Join the Session.wn-button,.wn-label,.wn-label:followingshow:inline-block.test_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px reliable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-major-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-proper-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimensions:13pxmargin:20px 0font-body weight:600letter-spacing:.6pxcolor:#596cec.wn-label:afterwidth:50pxheight:6pxcontent:”border-top:2px stable #d9deffmargin: 8px.wn-titlefont-measurement:21pxpadding:10px 0font-weight:900text-align:leftline-height:33px.wn-descriptiontextual content-align:leftfont-measurement:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-shade:#4469f5font-dimensions:15pxcolor:#fff!importantborder:0line-peak:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-bodyweight:500letter-spacing:.2px
The attacks have also produced use of a Node.js model of AHK Bot codenamed NODEBOT that’s then applied to download plugins liable for having screenshots, plundering passwords, collecting procedure facts, and putting in supplemental trojans and stealers.
Supplied the just about similar attack chains across cybercrime and espionage endeavours, it is suspected that “Asylum Ambuscade is a cybercrime group that is executing some cyber espionage on the side.”
The overlaps also prolong to one more action cluster dubbed Screentime that is recognized to concentrate on firms in the U.S. and Germany with bespoke malware intended to steal private info. Proofpoint is monitoring the menace actor beneath the title TA866.
“It is fairly unusual to catch a cybercrime team jogging focused cyberespionage operations,” Faou claimed, creating it rather of a rarity in the danger landscape.
Found this article exciting? Stick to us on Twitter and LinkedIn to browse extra special content material we submit.
Some parts of this posting are sourced from:
thehackernews.com


 Barracuda Urges Swift Replacement of Vulnerable ESG Appliances
Barracuda Urges Swift Replacement of Vulnerable ESG Appliances