An ongoing Magecart marketing campaign has captivated the attention of cybersecurity scientists for leveraging reasonable-on the lookout fake payment screens to capture delicate info entered by unsuspecting people.
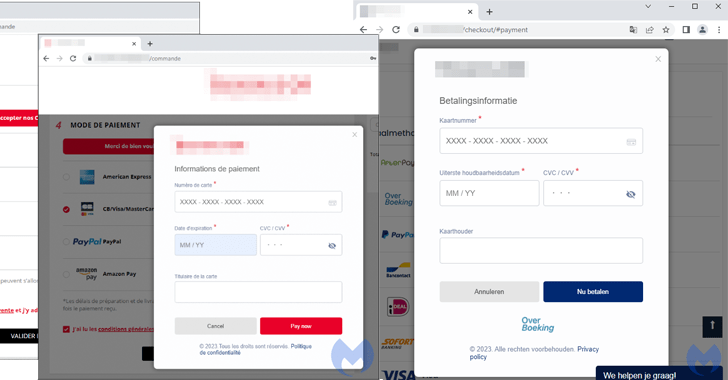
“The threat actor utilised first logos from the compromised store and customized a web component known as a modal to perfectly hijack the checkout web page,” Jérôme Segura, director of threat intelligence at Malwarebytes, claimed. “The amazing issue listed here is that the skimmer appears to be like additional reliable than the first payment page.”
The phrase Magecart is a catch-all that refers to several cybercrime teams which use on the net skimming procedures to steal private information from web sites – most normally, client particulars and payment data on e-commerce internet websites.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The title originates from the groups’ preliminary concentrating on of the Magento system. In accordance to data shared by Sansec, the to start with Magecart-like attacks have been noticed as early as 2010. As of 2022, much more than 70,000 merchants are approximated to have been compromised with a web skimmer.
These electronic skimming attacks, also referred to as formjacking, customarily leverage various sorts of JavaScript trickery to siphon sensitive information from website users.
The most current iteration, as observed by Malwarebytes on an unnamed Parisian journey accent store running on the PrestaShop CMS, included the injection of a skimmer identified as Kritec to intercept the checkout procedure and exhibit a pretend payment dialog to victims.
Kritec, beforehand thorough by Akamai and Malwarebytes in February 2023, has been observed to impersonate authentic 3rd-party sellers like Google Tag Manager as an evasion technique.
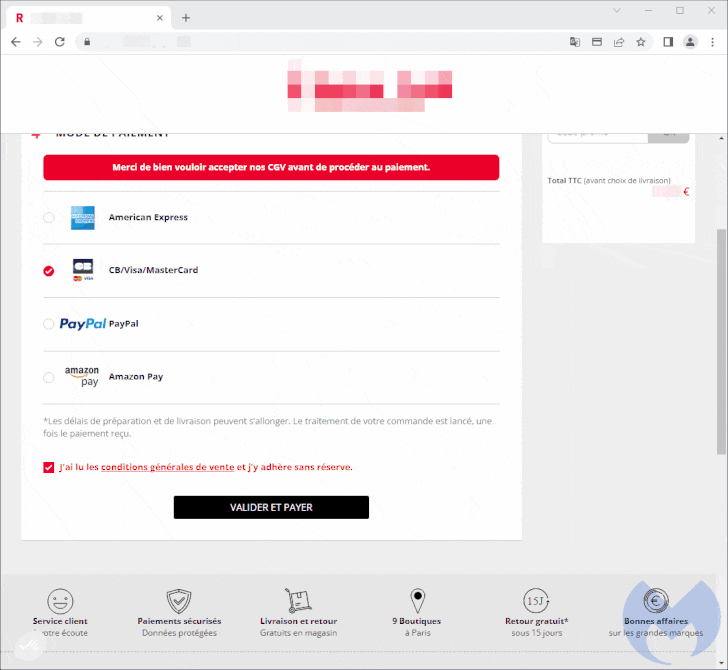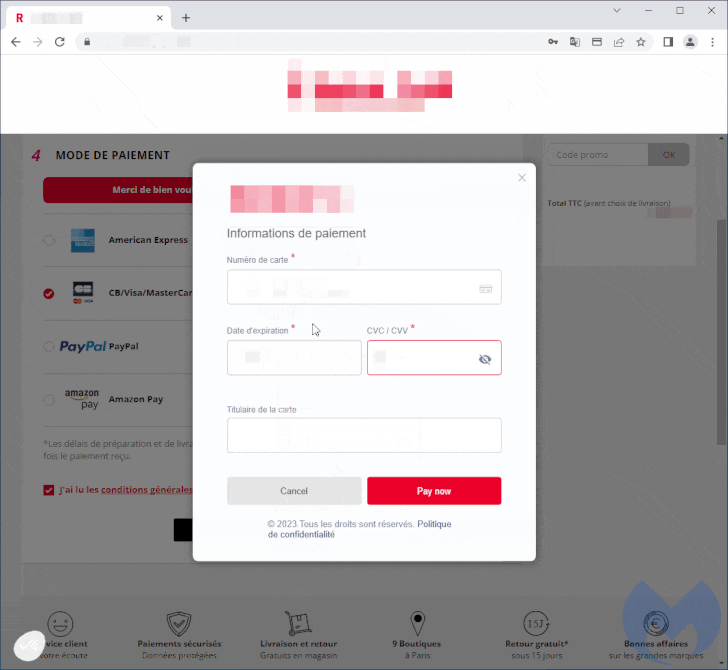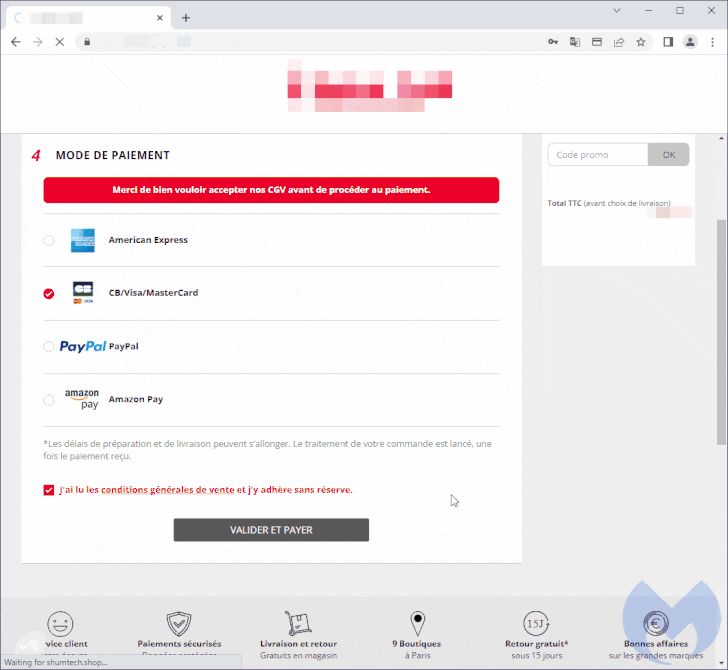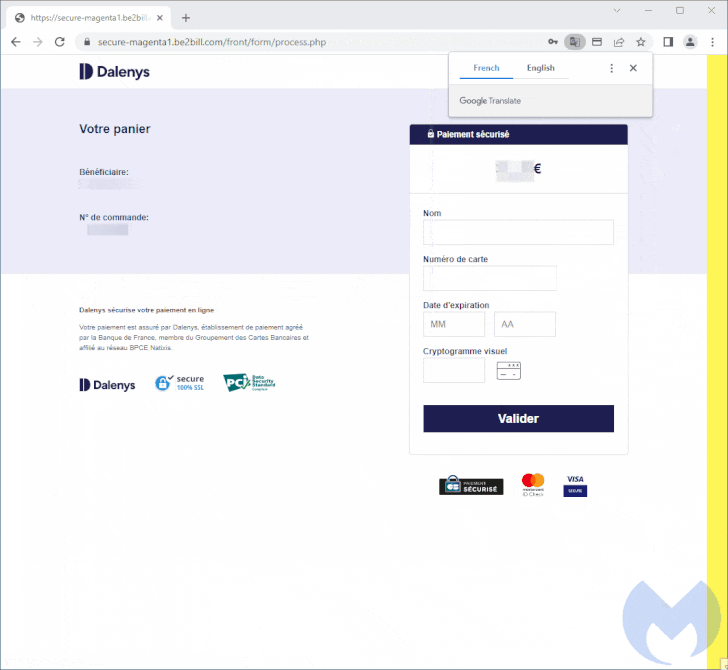
The cybersecurity agency stated the skimmer is each advanced and closely obfuscated, with the destructive modal loaded upon selecting a credit score card as the payment alternative from the compromised internet site.
When the payment card information are harvested, a phony error message about payment cancellation is briefly displayed to the victim just before redirecting to the true payment web page, at which level the payment will go as a result of.
“The skimmer will drop a cookie which will provide as an sign that the current session is now marked as accomplished,” Segura described. “If the consumer was to go again and attempt the payment yet again, the destructive modal would no longer be displayed.”
Upcoming WEBINARLearn to Halt Ransomware with Serious-Time Defense
Sign up for our webinar and learn how to halt ransomware attacks in their tracks with serious-time MFA and support account protection.
Help you save My Seat!
The risk actors driving the operation are mentioned to be employing distinct domains to host the skimmer, which are supplied equivalent names: “[name of store]-loader.js,” suggesting that the attacks are concentrating on distinctive on-line suppliers with tailor made modals.
“Discerning whether an on the internet shop is reliable has develop into incredibly hard and this case is a great instance of a skimmer that would not elevate any suspicion,” Segura reported.
The conclusions occur a tiny more than two months immediately after Malwarebytes unearthed one more web skimmer that collects browser fingerprint details, this kind of as IP addresses and User-Agent strings, alongside with credit score card information, most likely in an attempt to watch invalid customers such as bots and security scientists.
Observed this report intriguing? Follow us on Twitter and LinkedIn to read far more exceptional content we put up.
Some pieces of this report are sourced from:
thehackernews.com

 Google Bans 173,000 Bad Developers in 2022
Google Bans 173,000 Bad Developers in 2022