The cyber espionage group recognised as Bahamut has been attributed as behind a highly qualified marketing campaign that infects users of Android devices with destructive applications intended to extract sensitive info.
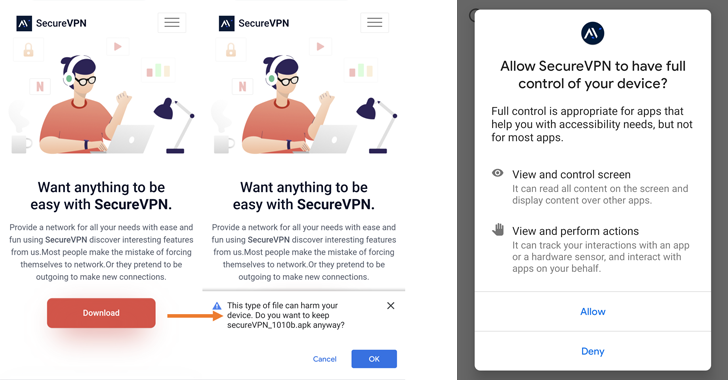
The action, which has been lively considering that January 2022, entails distributing rogue VPN applications by means of a bogus SecureVPN web page established up for this function, Slovak cybersecurity company ESET stated in a new report shared with The Hacker Information.
At least 8 unique variants of the adware apps have been found out to day, with them becoming trojanized versions of respectable VPN applications like SoftVPN and OpenVPN.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The tampered apps and their updates are pushed to people as a result of the fraudulent web-site. It is really also suspected that the targets are diligently picked, since launching the app necessitates the victim to enter an activation key to permit the features.
This indicates the use of an undetermined distribution vector, while previous proof displays that it could choose the sort of spear-phishing e-mails, SMS messages, or direct messages on social media apps.
The activation key system is also made to talk with an actor-managed server, effectively avoiding the malware from staying unintentionally triggered right immediately after start on a non-qualified user unit.
Bahamut was unmasked in 2017 by Bellingcat as a hack-for-employ the service of operation concentrating on authorities officers, human legal rights groups, and other superior-profile entities in South Asia and the Center East with malicious Android and iOS apps to spy on its victims.
“Most likely the most unique component of Bahamut’s tradecraft that BlackBerry uncovered is the group’s use of initial, painstakingly crafted sites, programs and personas,” BlackBerry noted in October 2020.
Before this calendar year, Cyble comprehensive two sets of phishing attacks orchestrated by the group to force counterfeit Android apps masquerading as chat apps.
The hottest wave follows a similar trajectory, tricking customers into setting up seemingly innocuous VPN applications that can exfiltrate a vast swathe of details, like data files, contact lists, SMSes, phone call recordings, areas, and messages from WhatsApp, Fb Messenger, Signal, Viber, Telegram, and WeChat.
“The details exfiltration is performed by means of the keylogging functionality of the malware, which misuses accessibility products and services,” ESET researcher Lukáš Štefanko explained.
In a indicator that the marketing campaign is perfectly maintained, the threat actor at first packaged the destructive code within the SoftVPN software, ahead of shifting to OpenVPN, a shift described by the point that the true SoftVPN app stopped functioning and it was no for a longer period probable to create a VPN connection.
“The cellular campaign operated by the Bahamut APT team is still energetic it works by using the identical process of distributing its Android spy ware applications by using internet websites that impersonate or masquerade as reputable solutions, as has been found in the previous,” Štefanko added.
Found this write-up appealing? Abide by THN on Fb, Twitter and LinkedIn to read a lot more special content material we publish.
Some areas of this post are sourced from:
thehackernews.com

 UK Cops Lead Action Against Fraud Site that Made £100m+
UK Cops Lead Action Against Fraud Site that Made £100m+