The threat actors at the rear of the Windows banking malware acknowledged as Casbaneiro has been attributed as behind a novel Android trojan referred to as BrasDex that has been observed focusing on Brazilian users as aspect of an ongoing multi-platform campaign.
BrasDex attributes a “advanced keylogging method designed to abuse Accessibility Providers to extract qualifications exclusively from a set of Brazilian qualified applications, as nicely as a extremely able Automatic Transfer Method (ATS) motor,” ThreatFabric claimed in a report posted last week.
The Dutch security company said that the command-and-handle (C2) infrastructure made use of in conjunction with BrasDex is also remaining utilized to management Casbaneiro, which is recognized to strike banks and cryptocurrency solutions in Brazil and Mexico.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The hybrid Android and Windows malware marketing campaign is approximated to have resulted in countless numbers of bacterial infections to day.

BrasDex, which masquerades as a banking app for Banco Santander, is also emblematic of a new craze that involves abusing Android’s Accessibility APIs to log keystrokes entered by the victims, shifting absent from the classic strategy of overlay attacks to steal qualifications and other personal knowledge.
It really is also engineered to seize account harmony details, subsequently working with it to take about infected equipment and initiate fraudulent transactions in a programmatic way.
A further notable element of BrasDex is its singular concentrate on the PIX payments system, which makes it possible for banking clients in Brazil to make income transfers only applying their email addresses or phone quantities.
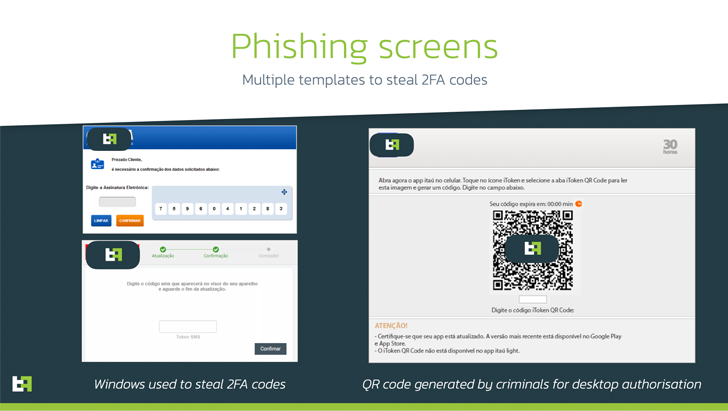
The ATS process in BrasDex is explicitly created to abuse PIX technology to make fraudulent transfers.
This is not the 1st time the fast payment ecosystem has been targeted by negative actors. In September 2021, Test Level thorough two Android malware family members named PixStealer and MalRhino that tricked customers into transferring their complete account balances to an actor-managed just one.
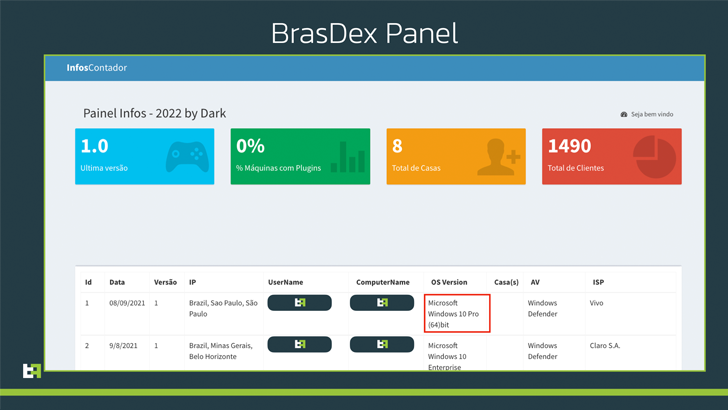
ThreatFabric’s investigation into BrasDex also authorized it to achieve accessibility to the C2 panel utilised by the criminal operators to hold keep track of of the infected products and retrieve info logs exfiltrated from the Android phones.
The C2 panel, as it comes about, is also being utilized to continue to keep tabs on a various malware marketing campaign which compromises Windows equipment to deploy Casbaneiro, a Delphi-dependent economical trojan.
This attack chain employs bundle delivery-themed phishing lures purporting to be from Correios, a state-owned postal support, to dupe recipients into executing the malware following a multi-staged course of action.
Casbaneiro’s capabilities operate the standard backdoor gamut that allows it to seize manage of banking accounts, acquire screenshots, accomplish keylogging, hijack clipboard knowledge, and even purpose as a clipper malware to hijack crypto transactions.
“Becoming impartial and entire-fledged malware family members, BrasDex and Casbaneiro sort a extremely risky pair, allowing the actor driving them to goal each Android and Windows people on a substantial scale,” ThreatFabric said.
“The BrasDex situation exhibits the requirement of fraud detection and prevention mechanisms in put on clients devices: Fraudulent payments designed automatically with the help of ATS engines seem legit to financial institution backends and fraud scoring engines, as they are produced by means of the identical machine that is commonly used by shoppers.”
Discovered this post exciting? Adhere to us on Twitter and LinkedIn to read additional exclusive information we submit.
Some sections of this short article are sourced from:
thehackernews.com


 Russian Hackers Targeted Petroleum Refinery in NATO Country During Ukraine War
Russian Hackers Targeted Petroleum Refinery in NATO Country During Ukraine War