An espionage-concentrated danger actor recognised for concentrating on China, Pakistan, and Saudi Arabia has expanded to set its sights on Bangladeshi government businesses as aspect of an ongoing marketing campaign that commenced in August 2021.
Cybersecurity organization Cisco Talos attributed the exercise with moderate self-assurance to a hacking team dubbed the Bitter APT based mostly on overlaps in the command-and-handle (C2) infrastructure with that of prior campaigns mounted by the identical actor.
“Bangladesh fits the profile we have defined for this danger actor, earlier focusing on Southeast Asian nations together with China, Pakistan, and Saudi Arabia,” Vitor Ventura, direct security researcher at Cisco Talos, informed The Hacker Information.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“And now, in this hottest marketing campaign, they have widened their access to Bangladesh. Any new place in southeast Asia currently being specific by Bitter APT should not be of shock.”
Bitter (aka APT-C-08 or T-APT-17) is suspected to be a South Asian hacking team enthusiastic mostly by intelligence gathering, an operation which is facilitated by usually means of malware such as BitterRAT, ArtraDownloader, and AndroRAT. Distinguished targets involve the strength, engineering, and federal government sectors.
The earliest attacks ended up distributing the cell model of BitterRAT day back to September 2014, with the actor obtaining a historical past of leveraging zero-working day flaws — CVE-2021-1732 and CVE-2021-28310 — to its benefit and execute its adversarial targets.
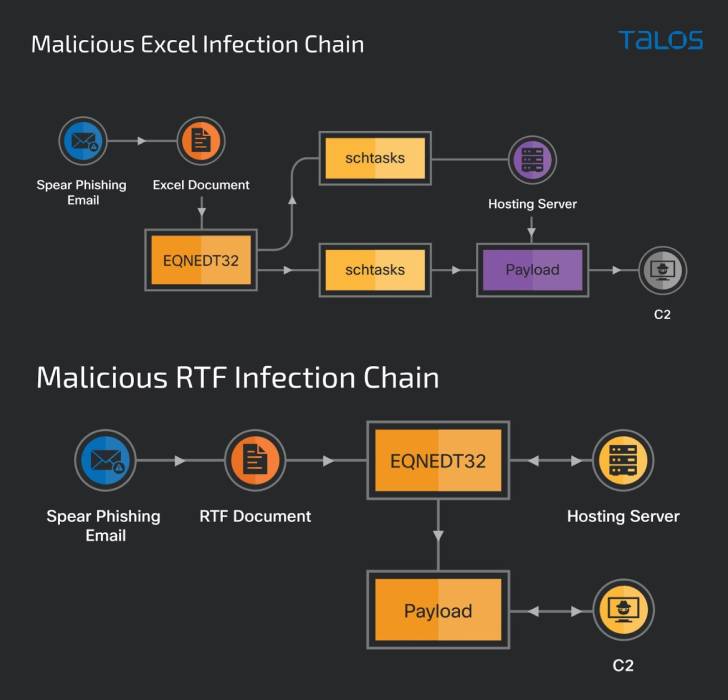
The most recent marketing campaign, concentrating on an elite entity of the Bangladesh govt, entails sending spear-phishing email messages to large-rating officers of the Speedy Action Battalion Device of the Bangladesh law enforcement (RAB).
As is ordinarily noticed in other social engineering attacks of this type, the missives are developed to entice the recipients into opening a weaponized RTF document or a Microsoft Excel spreadsheet that exploits beforehand regarded flaws in the software to deploy a new trojan dubbed “ZxxZ.”
ZxxZ, named so right after a separator utilized by the malware when sending information and facts back to the C2 server, is a 32-little bit Windows executable compiled in Visible C++.
“The trojan masquerades as a Windows Security update service and will allow the
malicious actor to conduct distant code execution, allowing for the attacker to complete any other functions by putting in other equipment,” the scientists spelled out.
When the malicious RTF doc exploits a memory corruption vulnerability in Microsoft Office’s Equation Editor (CVE-2017-11882), the Excel file abuses two remote code execution flaws, CVE-2018-0798 and CVE-2018-0802, to activate the an infection sequence.
“Actors normally change their applications to steer clear of detection or attribution, this is section of the lifecycle of a danger actor showing its capability and willpower,” Ventura claimed.
Located this report attention-grabbing? Abide by THN on Facebook, Twitter and LinkedIn to examine a lot more special written content we write-up.
Some components of this post are sourced from:
thehackernews.com


 Intel Memory Bug Poses Risk for Hundreds of Products
Intel Memory Bug Poses Risk for Hundreds of Products