Corporations centered in the U.S. have been at the obtaining close of an “intense” Qakbot malware marketing campaign that leads to Black Basta ransomware bacterial infections on compromised networks.
“In this most recent marketing campaign, the Black Basta ransomware gang is applying QakBot malware to create an first place of entry and move laterally inside an organization’s network,” Cybereason researchers Joakim Kandefelt and Danielle Frankel explained in a report shared with The Hacker Information.
Black Basta, which emerged in April 2022, follows the attempted-and-tested solution of double extortion to steal delicate information from focused businesses and use it as leverage to extort cryptocurrency payments by threatening to launch the stolen details.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This is not the initially time the ransomware crew has been noticed applying Qakbot (aka QBot, QuackBot, or Pinkslipbot). Previous thirty day period, Trend Micro disclosed comparable attacks that entailed the use of Qakbot to deliver the Brute Ratel C4 framework, which, in change, was leveraged to fall Cobalt Strike.
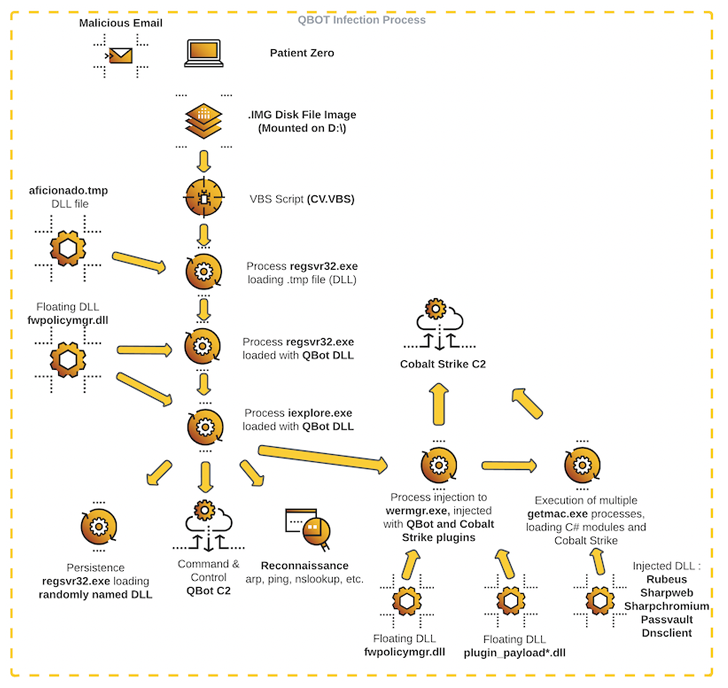
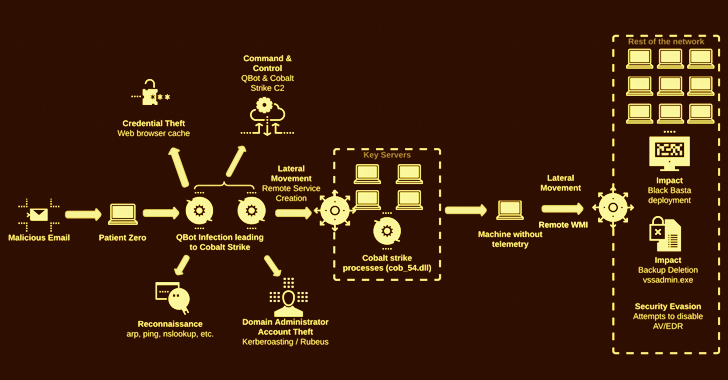
The intrusion exercise noticed by Cybereason cuts out Brute Ratel C4 from the equation, as an alternative using Qakbot to right distribute Cobalt Strike on quite a few devices in the contaminated natural environment.
The attack chain commences with a spear-phishing email bearing a malicious disk impression file that, when opened, kickstarts the execution of Qbot, which, for its component, connects to a distant server to retrieve the Cobalt Strike payload.
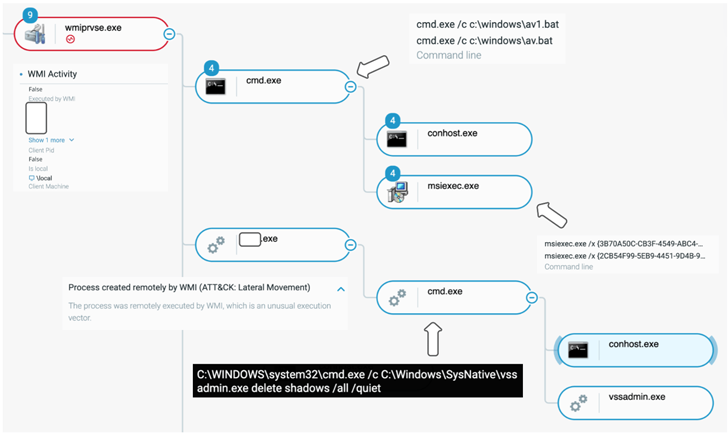
At this stage, credential harvesting and lateral movement actions are carried out to place the purple crew framework on quite a few servers, prior to breaching as a lot of endpoints as feasible making use of the gathered passwords and launching the Black Basta ransomware.
“The danger actor acquired domain administrator privileges in significantly less than two hrs and moved to ransomware deployment in fewer than 12 hrs,” the researchers observed, incorporating in excess of 10 unique shoppers were being impacted by the refreshing established of attacks in the earlier two weeks.
In two occasions noticed by the Israeli cybersecurity corporation, the intrusions not only deployed the ransomware but also locked the victims out of their networks by disabling the DNS services in a bid to make a restoration far more demanding.
Black Basta stays a very lively ransomware actor. According to data gathered by Malwarebytes, Black Basta effectively qualified 25 firms in October 2022 by itself, placing it driving LockBit, Karakurt, and BlackCat.
Observed this article intriguing? Observe THN on Facebook, Twitter and LinkedIn to browse much more unique written content we submit.
Some components of this article are sourced from:
thehackernews.com

 Panaseer Launches Guidance on Security Controls Ahead of EU’s New Legislation
Panaseer Launches Guidance on Security Controls Ahead of EU’s New Legislation