The risk actors powering the Black Basta ransomware spouse and children have been observed applying the Qakbot trojan to deploy the Brute Ratel C4 framework as a second-phase payload in modern attacks.
The advancement marks the very first time the nascent adversary simulation software package is becoming delivered by using a Qakbot an infection, cybersecurity company Development Micro said in a technical assessment launched final 7 days.
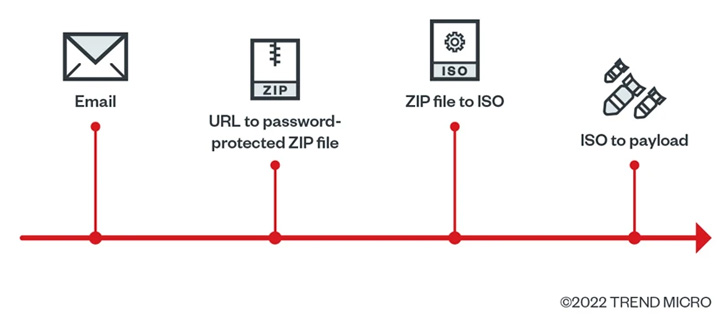
The intrusion, achieved employing a phishing email containing a weaponized connection pointing to a ZIP archive, further entailed the use of Cobalt Strike for lateral movement.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
While these legit utilities are developed for conducting penetration tests activities, their potential to present distant access has manufactured them a worthwhile device in the palms of attackers on the lookout to stealthily probe the compromised atmosphere with no attracting focus for prolonged durations of time.
This has been compounded by the truth that a cracked model of Brute Ratel C4 started circulating final month throughout the cybercriminal underground, prompting its developer to update the licensing algorithm to make it more challenging to crack.

Qakbot, also called QBot and QuackBot, is an information and facts stealer and banking trojan which is recognised to be lively because 2007. But its modular design and its skill to act as a downloader has turned it into an desirable prospect for dropping further malware.
In accordance to Craze Micro, the ZIP file in the email consists of an ISO file, which, in switch, involves a LNK file that fetches the Qakbot payload, illustrating makes an attempt on aspect of danger actors to adapt to other ways in the aftermath of Microsoft’s final decision to block macros by default for files downloaded from the web.
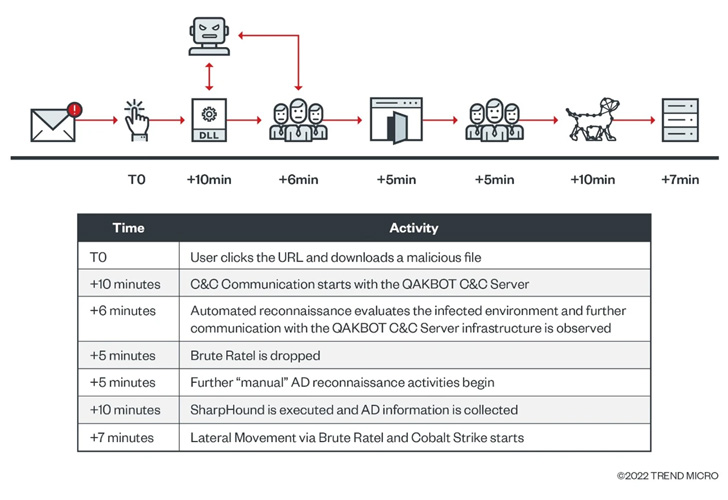
The Qakbot infection is succeeded by the retrieval of Brute Ratel and Cobalt Strike, but not before doing automated reconnaissance via created-in command line applications these kinds of as arp, ipconfig, nslookup, netstat, and whoami.
The attack, nevertheless, was stopped prior to any malicious action could be taken by the danger actor, whilst it truly is suspected that the conclude intention may possibly have been area-huge ransomware deployment.
In a further Qakbot execution chain noticed by the cybersecurity firm, the ZIP file is sent via an significantly preferred process identified as HTML smuggling, resulting in the execution of Brute Ratel C4 as the next-stage.
“The Qakbot-to-Brute Ratel-to-Cobalt Strike kill chain is affiliated with the group driving the Black Basta Ransomware,” the researchers explained. “This is based mostly on overlapping TTPs and infrastructure observed in Black Basta attacks.”
The findings coincide with a resurgence of Qakbot attacks in current months by indicates of a range of tactics like HTML file attachments, DLL side-loading, and email thread hijacking, the previous of which entailed harvesting e-mails in bulk from productive ProxyLogon attacks aimed at Microsoft Trade servers.
IcedID Actors Diversify Shipping and delivery Approaches
Qakbot is significantly from the only obtain-as-a-company malware that’s staying increasingly dispersed via ISO and other file formats to get all-around macro constraints, for Emotet, IcedID, and Bumblebee strategies have all adopted comparable trajectories.

Palo Alto Networks Device 42, in late September 2022, claimed it learned a malicious polyglot Microsoft Compiled HTML Assistance (CHM) file currently being utilized to produce the IcedID (aka BokBot) malware.
Other outstanding shipping procedures and an infection pathways have included the use of password-safeguarded ZIP files containing an ISO file, mirroring that of Qakbot, with the payload propagated via a pay-per-installer company known as PrivateLoader, in accordance to Crew Cymru.
And, to leading it all, Emotet seems to be readying for a fresh established of attacks just after a quick a few-thirty day period hiatus to rework its “systeminfo” module to “enhance focusing on of unique victims and distinguish monitoring bots from real end users,” ESET disclosed in a series of tweets.
“We have not witnessed new spam waves from Emotet given that July,” Jean-Ian Boutin, director of risk investigate at ESET, instructed The Hacker Information. “It is not clear why that is.”
“They did choose some breaks in the past, but under no circumstances for that prolonged. Perhaps this new module usually means that they are screening modules and will be energetic yet again in the in the vicinity of foreseeable future, but this of training course is speculation.”
Identified this post intriguing? Stick to THN on Facebook, Twitter and LinkedIn to examine extra exceptional written content we article.
Some components of this report are sourced from:
thehackernews.com


 Microsoft warns of ‘Prestige’ ransomware targeting business in Ukraine, Poland
Microsoft warns of ‘Prestige’ ransomware targeting business in Ukraine, Poland