The operators behind BRATA have at the time all over again extra much more capabilities to the Android cellular malware in an try to make their attacks from monetary applications more stealthy.
“In fact, the modus operandi now matches into an Highly developed Persistent Danger (APT) exercise sample,” Italian cybersecurity organization Cleafy stated in a report past week. “This phrase is employed to describe an attack marketing campaign in which criminals establish a extended-expression existence on a focused network to steal delicate info.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

An acronym for “Brazilian Remote Accessibility Device Android,” BRATA was to start with detected in the wild in Brazil in late 2018, just before generating its 1st appearance in Europe last April, even though masquerading as antivirus application and other typical productiveness tools to trick people into downloading them.
The modify in the attack pattern, which scaled new highs in early April 2022, requires tailoring the malware to strike a unique monetary institution at a time, switching to a various lender only after the victim commences applying countermeasures against the menace.
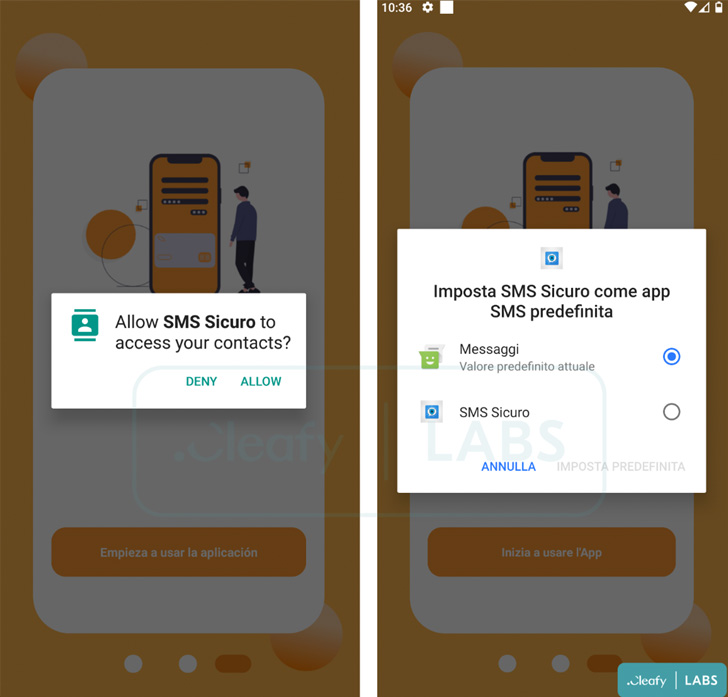
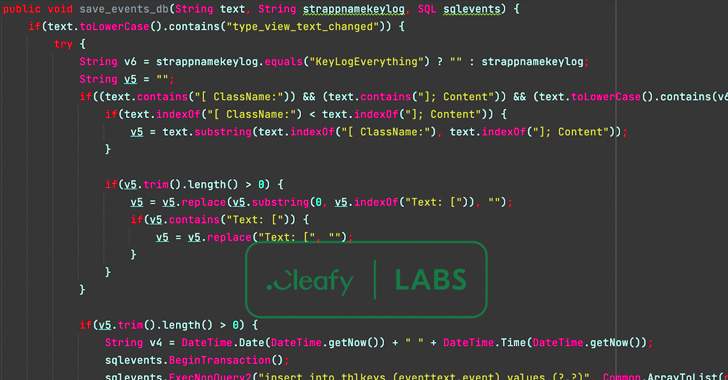
Also integrated in the rogue apps are new capabilities that allow it to impersonate the login site of the economical institution to harvest credentials, access SMS messages, and sideload a second-phase payload (“unrar.jar”) from a remote server to log events on the compromised system.
“The mix of the phishing web site with the likelihood to get and examine the victim’s sms could be utilized to conduct a comprehensive Account Takeover (ATO) attack,” the scientists said.
In addition, Cleafy said it located a independent Android app package deal sample (“SMSAppSicura.apk”) that made use of the exact same command-and-management (C2) infrastructure as BRATA to siphon SMS messages, indicating that the risk actors are screening out different strategies to broaden their arrive at.

The SMS stealer application is stated to be particularly singling out consumers in the U.K., Italy, and Spain, its objective becoming capable to intercept and exfiltrate all incoming messages related to a person-time passwords despatched by banks.
“The initial campaigns of malware had been distributed through phony antivirus or other typical apps, when all through the campaigns the malware is using the convert of an APT attack in opposition to the customer of a particular Italian financial institution,” the researchers stated.
“They generally aim on offering malicious apps specific to a distinct lender for a pair of months, and then shifting to another goal.”
Found this report intriguing? Observe THN on Facebook, Twitter and LinkedIn to examine a lot more special material we article.
Some elements of this report are sourced from:
thehackernews.com


 Over a Dozen Flaws Found in Siemens’ Industrial Network Management System
Over a Dozen Flaws Found in Siemens’ Industrial Network Management System