A formerly undocumented espionage resource has been deployed in opposition to selected governments and other critical infrastructure targets as section of a lengthy-managing espionage marketing campaign orchestrated by China-connected threat actors considering the fact that at the very least 2013.
Broadcom’s Symantec Threat Hunter workforce characterized the backdoor, named Daxin, as a technologically superior malware, enabling the attackers to have out a range of communications and data-accumulating functions aimed at entities in the telecom, transportation, and production sectors that are of strategic interest to China.
“Daxin malware is a very refined rootkit backdoor with intricate, stealthy command-and-control (C2) operation that enables remote actors to connect with secured equipment not connected directly to the internet,” the U.S. Cybersecurity and Infrastructure Security Agency (CISA) reported in an unbiased advisory.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

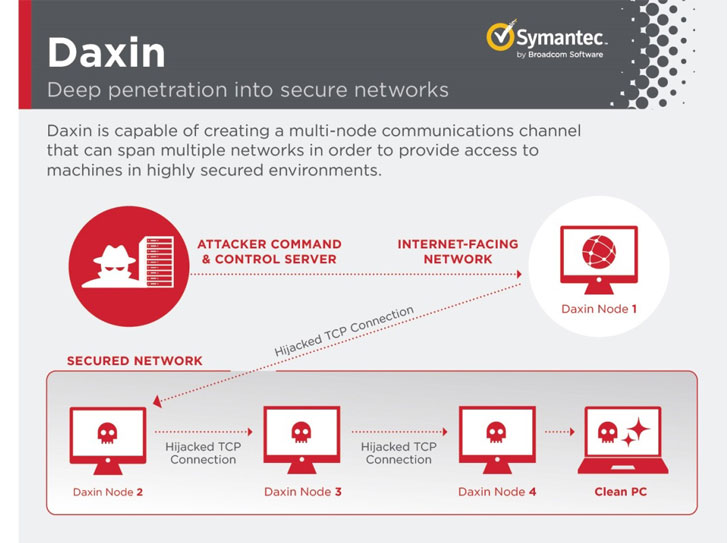
The implant normally takes the type of a Windows kernel driver that implements an elaborate communications system that affords the malware a high diploma of stealth and the capacity to communicate to equipment that are bodily disconnected from the internet.
It achieves this by expressly avoiding launching its own network products and services, as an alternative opting to consider benefit of reputable TCP/IP expert services presently jogging on the infected desktops to blend its communications with typical site visitors on the target’s network and get instructions from a distant peer.
“These functions are reminiscent of Regin,” the researchers pointed out, referring to a different innovative malware and hacking toolkit attributed to the U.S. Countrywide Security Agency (NSA) for authorities spying functions again in 2014.
Among the unconventional factors of Daxin, besides generating no suspicious network website traffic to remain unseen, is its capability to relay commands across a network of infected personal computers in just the attacked group, generating a “multi-node communications channel” that permits recurring obtain to the compromised pcs for extended intervals of time.
When modern intrusions involving the backdoor are mentioned to have transpired in November 2021, Symantec claimed it uncovered code-amount commonalities with an older piece of malware termed Exforel (aka Zala), indicating that Daxin may well have been constructed by an actor with accessibility to the latter’s codebase or that they are the operate of the exact same team.
The strategies have not been attributed to a one adversary, but a timeline of the attacks shows that Daxin was put in on some of the identical systems in which instruments related with other Chinese espionage actors like Slug ended up located. This contains the deployment of each Daxin and Owprox malware on a one personal computer belonging to a tech business in May well 2020.
“Daxin is with no question the most advanced piece of malware […] applied by a China-joined actor,” the scientists explained. “Looking at its abilities and the mother nature of its deployed attacks, Daxin appears to be optimized for use against hardened targets, making it possible for the attackers to burrow deep into a target’s network and exfiltrate knowledge with no elevating suspicions.”
The disclosure arrives a 7 days just after China-based Pangu Lab outed a “major-tier” backdoor named Bvp47 put to use by the U.S. National Security Agency for about a 10 years concentrating on as numerous as 287 businesses in 45 countries positioned mainly in China, Korea, Japan, Germany, Spain, India, and Mexico.
Observed this short article appealing? Comply with THN on Fb, Twitter and LinkedIn to read much more unique content we put up.
Some areas of this post are sourced from:
thehackernews.com



 CISA adds recently disclosed Zimbra bug to its Exploited Vulnerabilities Catalog
CISA adds recently disclosed Zimbra bug to its Exploited Vulnerabilities Catalog