A Chinese-talking highly developed persistent menace (APT) has been connected to a new marketing campaign concentrating on gambling-connected businesses in South East Asia, particularly Taiwan, the Philippines, and Hong Kong.
Cybersecurity agency Avast dubbed the marketing campaign Operation Dragon Castling, describing its malware arsenal as a “strong and modular toolset.” The top motives of the menace actor are not instantly discernible as nonetheless nor has it been linked to a known hacking group.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Whilst various first entry avenues were being used throughout the study course of the campaign, a single of the attack vectors concerned leveraging a earlier unknown remote code execution flaw in the WPS Office suite (CVE-2022-24934) to backdoor its targets. The issue has considering that been addressed by Kingsoft Office, the developers of the business program.
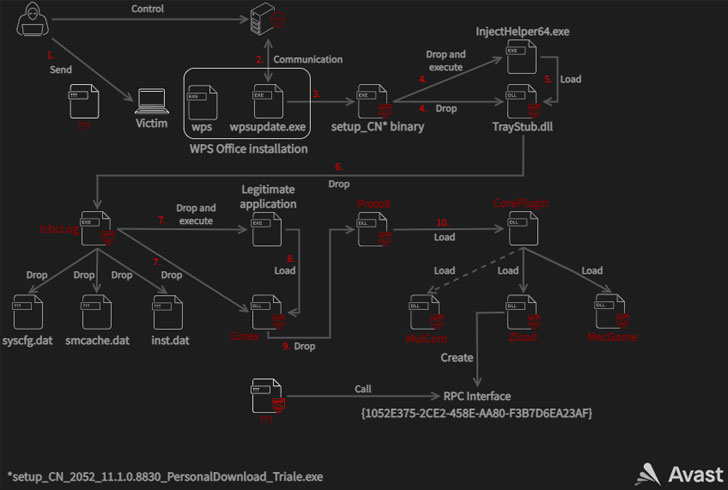
In the case observed by the Czech security business, the vulnerability was used to fall a malicious binary from a pretend update server with the domain update.wps[.]cn that triggers a multi-stage infection chain that sales opportunities to the deployment of intermediate payloads the permits for privilege escalation right before finally dropping the Proto8 module.
“The core module is a solitary DLL that is responsible for environment up the malware’s operating directory, loading configuration documents, updating its code, loading plugins, beaconing to [command-and-control] servers and ready for instructions,” Avast scientists Luigino Camastra, Igor Morgenstern, Jan Holman explained.
Proto8’s plugin-based technique applied to prolong its functionality permits the malware to achieve persistence, bypass consumer account manage (UAC) mechanisms, develop new backdoor accounts, and even execute arbitrary commands on the infected program.
Identified this write-up attention-grabbing? Comply with THN on Facebook, Twitter and LinkedIn to read more distinctive content material we write-up.
Some parts of this posting are sourced from:
thehackernews.com



 Microsoft Help Files Disguise Vidar Malware
Microsoft Help Files Disguise Vidar Malware