A Chinese state-sponsored hacking outfit has resurfaced with a new campaign concentrating on federal government, health care, technology, and manufacturing entities based mostly in Taiwan, Thailand, the Philippines, and Fiji soon after much more than six months of no action.
Development Micro attributed the intrusion established to a cyber espionage team it tracks beneath the title Earth Longzhi, which is a subgroup inside APT41 (aka HOODOO or Winnti) and shares overlaps with many other clusters regarded as Earth Baku, SparklingGoblin, and GroupCC.
Earth Longzhi was first documented by the cybersecurity firm in November 2022, detailing its attacks towards several corporations found in East and Southeast Asia as very well as Ukraine.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
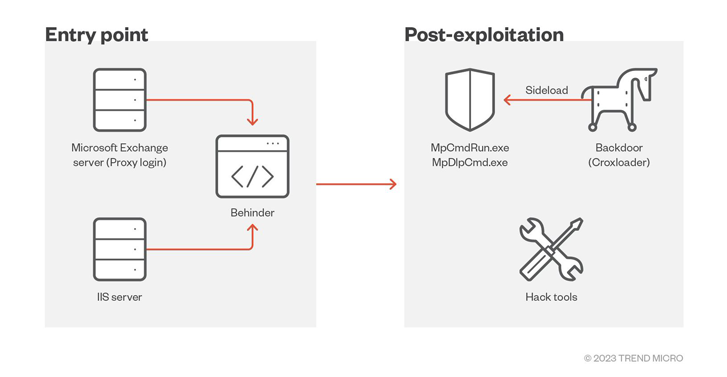
Attack chains mounted by the risk actor leverage vulnerable community-dealing with purposes as entry details to deploy the BEHINDER web shell, and then leverage that access to fall further payloads, including a new variant of a Cobalt Strike loader called CroxLoader.

“This latest campaign […] abuses a Windows Defender executable to complete DLL sideloading while also exploiting a vulnerable driver, zamguard.sys, to disable security goods mounted on the hosts through a carry your have vulnerable driver (BYOVD) attack,” Pattern Micro reported.
It can be by no means the initially time Earth Longzhi has leveraged the BYOVD technique, what with former campaigns using the susceptible RTCore64.sys driver to restrict the execution of security solutions.
The malware, dubbed SPHijacker, also employs a second approach referred to as “stack rumbling” to realize the same goal, which entails intentionally producing the specific applications to crash upon launch.
“This procedure is a sort of [denial-of-service] attack that abuses undocumented MinimumStackCommitInBytes values in the [Image File Execution Options] registry key,” Development Micro explained.
“The benefit of MinimumStackCommitInBytes linked with a precise process in the IFEO registry key will be used to determine the minimum amount sizing of stack to dedicate in initializing the key thread. If the stack measurement is much too huge, it will result in a stack overflow exception and terminate the present-day course of action.”
The twin techniques are much from the only procedures that can be made use of to impair security items. Deep Intuition, previous month, in-depth a new code injection method christened Soiled Self-importance that exploits the distant forking mechanism in Windows to blindside endpoint detection devices.
What is a lot more, the driver payload is mounted as a kernel-degree company working with Microsoft Remote Process Contact (RPC) as opposed to Windows APIs to evade detection.
Approaching WEBINARLearn to Quit Ransomware with Actual-Time Safety
Join our webinar and study how to stop ransomware attacks in their tracks with serious-time MFA and support account protection.
Help save My Seat!
Also noticed in the attacks is the use of a DLL-based dropper named Roxwrapper to produce yet another Cobalt Strike loader labeled BigpipeLoader as perfectly as a privilege escalation software (dwm.exe) that abuses the Windows Endeavor Scheduler to start a specified payload with Method privileges.
The specified payload, dllhost.exe, is a downloader that is able of retrieving subsequent-phase malware from an actor-controlled server.
It really is really worth pointing out in this article that dwm.exe is dependent on an open resource evidence-of-notion (PoC) available on GitHub, suggesting that the threat actor is drawing inspiration from present courses to hone its malware arsenal.
Trend Micro further reported it discovered decoy files written in Vietnamese and Indonesian, indicating possible attempts to focus on consumers in the two nations around the world in the upcoming.
“Earth Longzhi stays energetic and continues to enhance its practices, techniques, and procedures (TTPs),” security scientists Ted Lee and Hara Hiroaki famous. “Businesses should really continue to be vigilant from the continuous progress of new stealthy strategies by cybercriminals.”
Identified this report attention-grabbing? Follow us on Twitter and LinkedIn to read through more unique written content we submit.
Some pieces of this report are sourced from:
thehackernews.com

 Download the eBook: What Does it Take to be a Full-Fledged Virtual CISO?
Download the eBook: What Does it Take to be a Full-Fledged Virtual CISO?