A Chinese-aligned cyberespionage group has been noticed striking the telecommunication sector in Central Asia with versions of malware these kinds of as ShadowPad and PlugX.
Cybersecurity company SentinelOne tied the intrusions to an actor it tracks under the title “Moshen Dragon,” with tactical overlaps in between the collective and yet another threat group referred to as Nomad Panda (aka RedFoxtrot).
“PlugX and ShadowPad have a very well-founded history of use amid Chinese-talking risk actors primarily for espionage activity,” SentinelOne’s Joey Chen stated. “Those people tools have flexible, modular features and are compiled by way of shellcode to very easily bypass conventional endpoint defense merchandise.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
ShadowPad, labeled a “masterpiece of privately bought malware in Chinese espionage,” emerged as a successor to PlugX in 2015, even as variants of the latter have continuously popped up as section of unique campaigns linked with Chinese threat actors.
Whilst regarded to be deployed by the government-sponsored hacking group dubbed Bronze Atlas (aka APT41, Barium, or Winnti) given that at least 2017, an at any time-escalating variety of other China-joined risk actors have joined the fray.
Before this yr, Secureworks attributed unique ShadowPad exercise clusters to Chinese nation-state teams that function in alignment with the Chinese Ministry of Point out Security (MSS) civilian intelligence company and the People’s Liberation Army (PLA).
The most up-to-date results from SentinelOne dovetails with a past report from Trellix in late March that disclosed a RedFoxtrot attack marketing campaign concentrating on telecom and protection sectors in South Asia with a new variant of PlugX malware named Talisman.

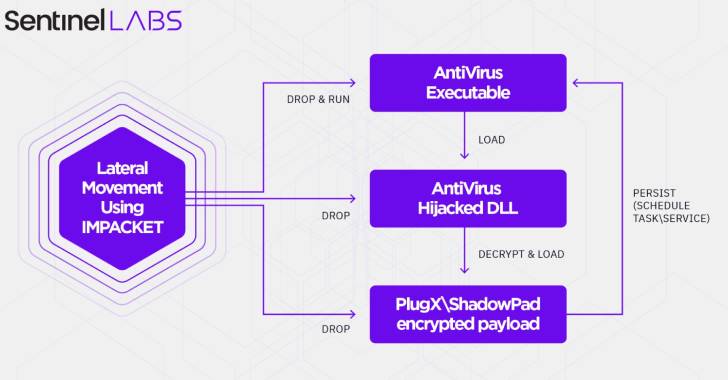
Moshen Dragon’s TTPs entail the abuse of authentic antivirus computer software belonging to BitDefender, Kaspersky, McAfee, Symantec, and Pattern Micro to sideload ShadowPad and Talisman on compromised devices by indicates of a approach termed DLL lookup purchase hijacking.
In the subsequent step, the hijacked DLL is applied to decrypt and load the closing ShadowPad or PlugX payload that resides in the exact same folder as that of the antivirus executable. Persistence is reached by either developing a scheduled process or a provider.
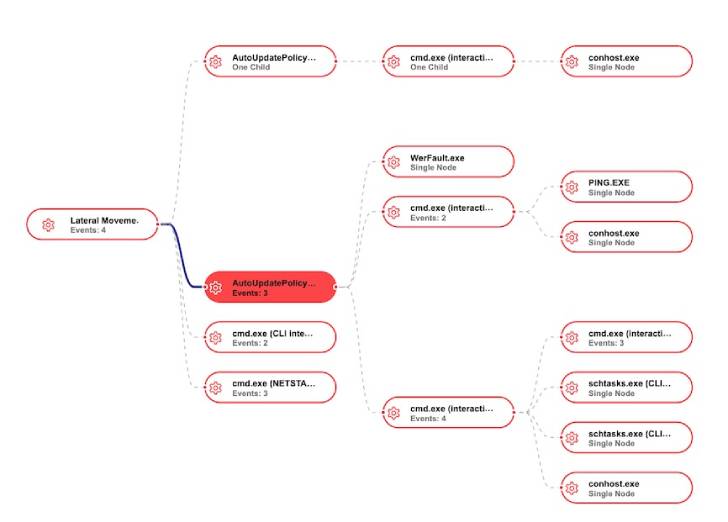
The hijacking of security goods notwithstanding, other strategies adopted by the group include things like the use of known hacking tools and crimson staff scripts to aid credential theft, lateral movement and info exfiltration. The first access vector continues to be unclear as nonetheless.
“As soon as the attackers have set up a foothold in an business, they move forward with lateral movement by leveraging Impacket inside of the network, placing a passive backdoor into the victim surroundings, harvesting as several qualifications as feasible to insure unlimited access, and concentrating on details exfiltration,” Chen stated.
Observed this posting fascinating? Stick to THN on Facebook, Twitter and LinkedIn to study additional unique information we submit.
Some components of this short article are sourced from:
thehackernews.com

 Unpatched DNS Related Vulnerability Affects a Wide Range of IoT Devices
Unpatched DNS Related Vulnerability Affects a Wide Range of IoT Devices