A earlier undocumented firmware implant deployed to preserve stealthy persistence as section of a qualified espionage campaign has been connected to the Chinese-speaking Winnti innovative persistent risk group (APT41).
Kaspersky, which codenamed the rootkit MoonBounce, characterized the malware as the “most superior UEFI firmware implant found in the wild to day,” adding “the function of the implant is to facilitate the deployment of person-method malware that stages execution of more payloads downloaded from the internet.”
Firmware-primarily based rootkits, the moment a rarity in the menace landscape, are rapidly becoming lucrative tools among the refined actors to enable reach extensive standing foothold in a method which is not only challenging to detect, but also challenging to get rid of.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The to start with firmware-stage rootkit — dubbed LoJax — was found out in the wild in 2018. Considering that then, 3 distinctive situations of UEFI malware have been unearthed so significantly, which include MosaicRegressor, FinFisher, and ESPecter.
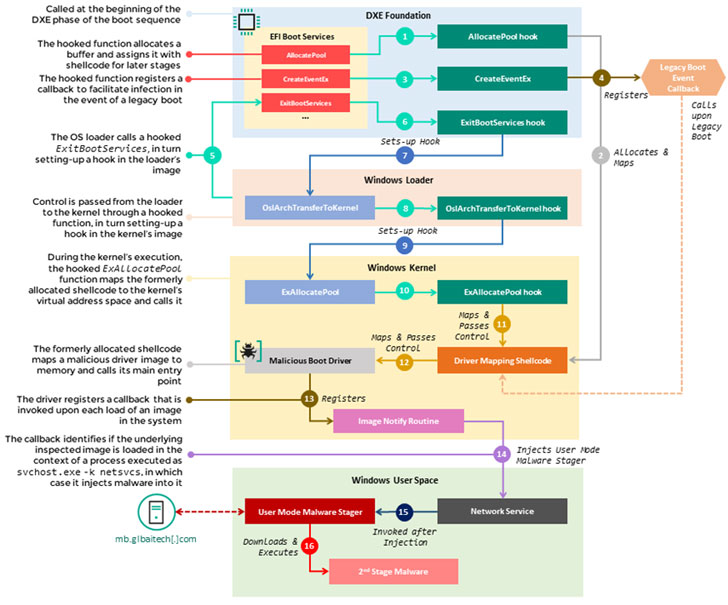
MoonBounce is concerning for a amount of motives. As opposed to FinFisher and ESPecter, which get purpose at the EFI Program Partition (ESP), the freshly identified rootkit — along the likes of LoJax and MosaicRegressor — targets the SPI flash, a non-unstable storage exterior to the hard push.
This sort of highly persistent bootkit malware is emplaced within SPI flash storage that is soldered to a computer’s motherboard, proficiently creating it extremely hard to get rid of via really hard drive substitution and even resistant to re-set up of the operating program.
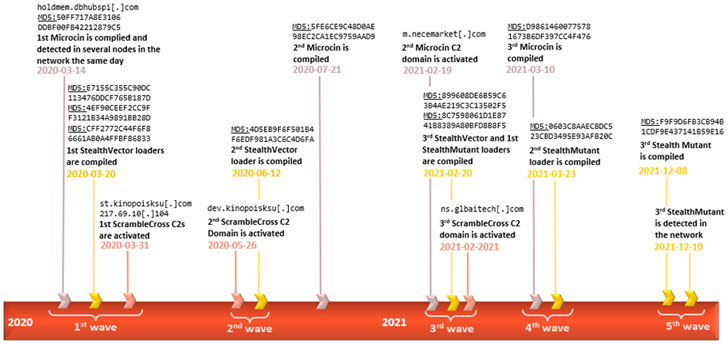
The Russian cybersecurity organization explained it determined the presence of the firmware rootkit in a solitary incident past yr, indicative of the extremely specific character of the attack. That reported, the specific system by which the UEFI firmware was infected remains unclear.
Incorporating to its stealthiness is the actuality that an current firmware component was tampered to change its behaviour — somewhat than incorporating a new driver to the image — with the intention of diverting the execution move of the boot sequence to a destructive “an infection chain” that injects the person-mode malware in the course of technique startup, which then reaches out to a hardcoded distant server to retrieve the future-stage payload.
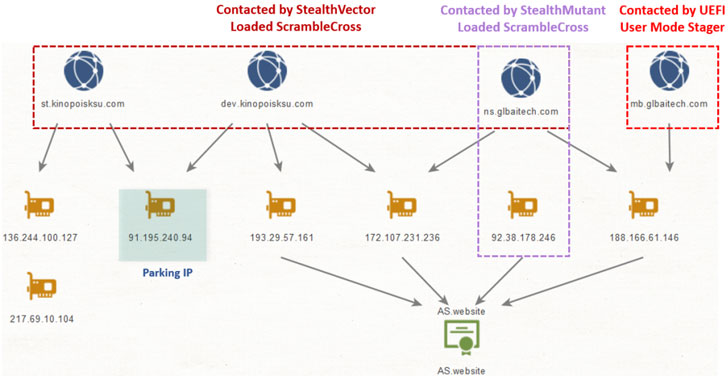
“The an infection chain itself does not depart any traces on the difficult generate, as its factors operate in memory only, therefore facilitating a fileless attack with a little footprint,” the researchers pointed out, introducing that it uncovered other non-UEFI implants in the qualified network communicating with the very same infrastructure that hosted the staging payload.
Chief amongst all those components deployed throughout multiple nodes in the network contain a backdoor tracked as ScrambleCross (aka Crosswalk) and a range of article-exploitation malware implants, suggesting that the attackers carried out lateral movement just after attaining an preliminary access in buy to exfiltrate info from distinct machines.
To counter these types of firmware-level modifications, it truly is advisable to frequently update the UEFI firmware as well as allow protections these kinds of as Boot Guard, Protected boot, and Trust System Modules (TPM).
“MoonBounce marks a specific evolution in this group of threats by presenting a much more complicated attack stream in comparison to its predecessors and a better stage of complex competence by its authors, who reveal a thorough understanding of the finer particulars included in the UEFI boot course of action,” the researchers reported.
Identified this posting appealing? Adhere to THN on Facebook, Twitter and LinkedIn to browse extra special information we put up.
Some areas of this short article are sourced from:
thehackernews.com



 (ISC)2 Appoints its First CISO
(ISC)2 Appoints its First CISO