An innovative persistent danger (APT) group running with aims aligned with the Chinese govt has been connected to an arranged provide chain attack on Taiwan’s fiscal sector.
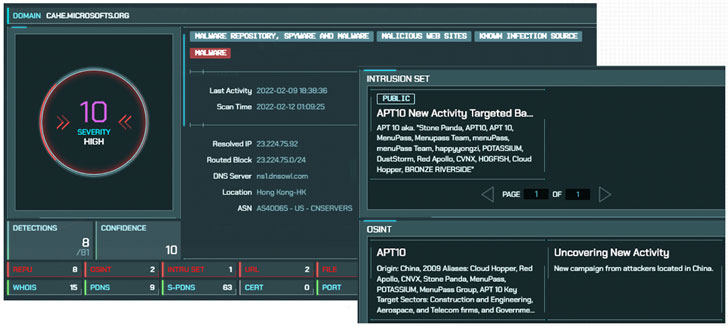
The attacks are stated to have very first commenced at the conclusion of November 2021, with the intrusions attributed to a risk actor tracked as APT10, also recognised as Stone Panda, the MenuPass team, and Bronze Riverside, and known to be active considering that at least 2009.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The next wave of attacks hit a peak involving February 10 and 13, 2022, in accordance to a new report printed by Taiwanese cybersecurity company CyCraft, which explained the wide-ranging supply chain compromise exclusively focused the program units of fiscal establishments, ensuing in “irregular circumstances of placing orders.”
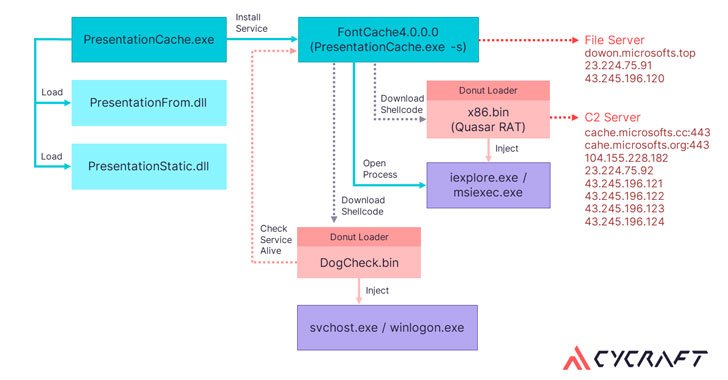
The infiltration activity, codenamed “Procedure Cache Panda,” exploited a vulnerability in the web management interface of the unnamed securities software program that has a market share of above 80% in Taiwan, making use of it to deploy a web shell that acts as a conduit for implanting the Quasar RAT on the compromised method with the objective of thieving sensitive information.
Quasar RAT is a publicly available open-resource distant access trojan (RAT) written in .NET. Its characteristics include capturing screenshots, recording webcam, editing registry, keylogging, and stealing passwords. In addition, the attacks leveraged a Chinese cloud file sharing services called wenshushu.cn to down load auxiliary resources.
The disclosure will come as Taiwan’s Parliament, the Government Yuan, unveiled draft amendments to national security legal guidelines aimed at combating Chinese economic and industrial espionage attempts. To that conclude, unapproved use of critical national systems and trade secrets outdoors of the region could have up to a 12-yr jail sentence.
Furthermore, men and women and businesses that have been entrusted or backed by the Taiwanese federal government to carry out functions involving critical national systems are anticipated to protected prior govt approval for any journeys to China, failing which could incur monetary fines of up to NT$10 million (~US$359,000).
Identified this write-up exciting? Follow THN on Fb, Twitter and LinkedIn to go through much more distinctive information we write-up.
Some parts of this report are sourced from:
thehackernews.com



 Hackers Backdoor Unpatched Microsoft SQL Database Servers with Cobalt Strike
Hackers Backdoor Unpatched Microsoft SQL Database Servers with Cobalt Strike