The China-aligned Mustang Panda actor has been observed utilizing a hitherto unseen customized backdoor identified as MQsTTang as part of an ongoing social engineering campaign that commenced in January 2023.
“Compared with most of the group’s malware, MQsTTang doesn’t appear to be to be based mostly on current households or publicly out there projects,” ESET researcher Alexandre Côté Cyr explained in a new report.
Attack chains orchestrated by the team have stepped up focusing on of European entities in the wake of Russia’s total-scale invasion of Ukraine past 12 months. The victimology of the existing action is unclear, but the Slovak cybersecurity business reported the decoy filenames are in line with the group’s previous campaigns that goal European political businesses.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
That mentioned, ESET also observed attacks versus unfamiliar entities in Bulgaria and Australia, as well as a governmental establishment in Taiwan, indicating aim on Europe and Asia.
Mustang Panda has a background of utilizing a distant accessibility trojan dubbed PlugX for achieving its targets, although current intrusions have viewed the group increasing its malware arsenal to incorporate tailor made applications like TONEINS, TONESHELL, and PUBLOAD.
In December 2022, Avast disclosed another set of attacks aimed at govt companies and political NGOs in Myanmar that led to the exfiltration of delicate knowledge, such as email dumps, documents, courtroom hearings, interrogation reports, and conference transcripts, working with a PlugX variant called Hodur and a Google Push uploader utility.
What is actually far more, an FTP server connected to the menace actor has been discovered to host a range of beforehand undocumented tools employed to distribute malware to contaminated gadgets, which include a Go-dependent trojan referred to as JSX and a sophisticated backdoor referred to as HT3.
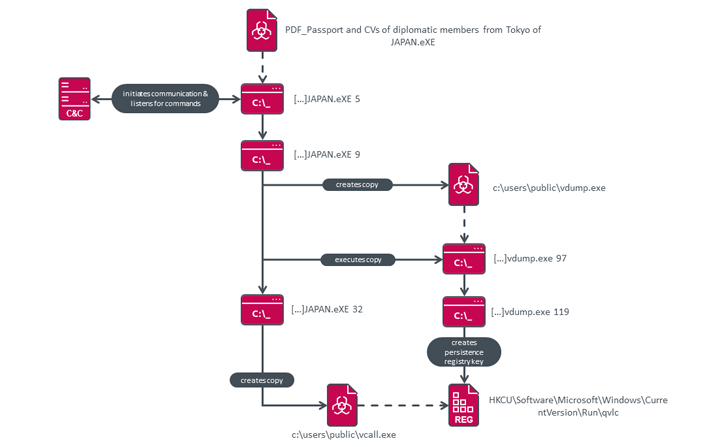
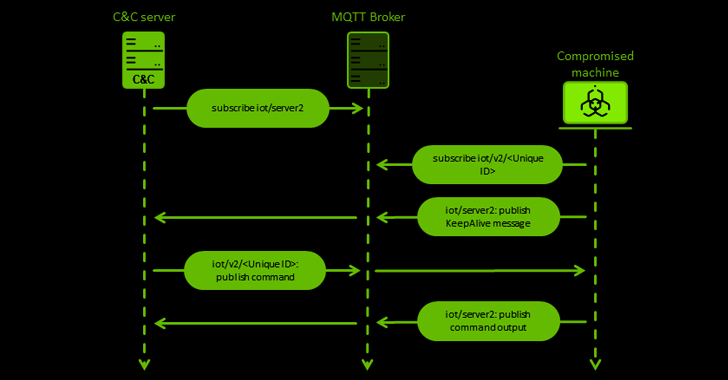
The growth of MQsTTang factors to a continuation of that pattern, even if it is really a “barebones” solitary-stage backdoor sans any obfuscation tactics that permit for executing arbitrary instructions been given from a remote server.
v
Even so, an uncommon component of the implant is the use of an IoT messaging protocol known as MQTT for command-and-command (C2) communications, which is attained applying an open resource library called QMQTT, an MQTT client for the Qt cross-system application framework.
The first intrusion vector for the attacks is spear-phishing, with MQTT distributed via RAR archives made up of a solitary executable that options filenames with diplomatic themes (e.g., “PDF_Passport and CVs of diplomatic associates from Tokyo of JAPAN.eXE”).
“This new MQsTTang backdoor presents a kind of remote shell devoid of any of the bells and whistles linked with the group’s other malware households,” Côté Cyr reported. “Nonetheless, it displays that Mustang Panda is discovering new technology stacks for its instruments.”
Discovered this write-up interesting? Follow us on Twitter and LinkedIn to go through more exceptional articles we submit.
Some pieces of this post are sourced from:
thehackernews.com

 Experts Warn of “SMS Pumping” Fraud Epidemic
Experts Warn of “SMS Pumping” Fraud Epidemic