An state-of-the-art persistent risk (APT) team of Chinese origin codenamed DiceyF has been linked to a string of attacks aimed at online casinos in Southeast Asia for years.
Russian cybersecurity organization Kaspersky explained the activity aligns with a further set of intrusions attributed to Earth Berberoka (aka GamblingPuppet) and DRBControl, citing tactical and concentrating on similarities as properly as the abuse of protected messaging customers.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Perhaps we have a mix of espionage and [intellectual property] theft, but the real motivations continue to be a thriller,” researchers Kurt Baumgartner and Georgy Kucherin mentioned in a technological produce-up printed this week.
The starting point of the investigation was in November 2021 when Kaspersky claimed it detected a number of PlugX loaders and other payloads that have been deployed by means of an worker checking assistance and a security package deployment assistance.
The original an infection strategy – the distribution of the framework by way of security answer offers – afforded the danger actor “to execute cyberespionage things to do with some degree of stealth,” the firm said.
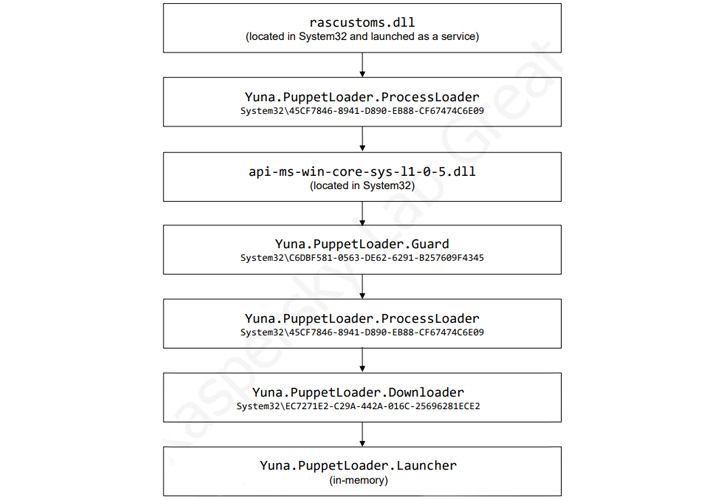
Subsequently, the exact security offer deployment provider is explained to have been used to deliver what’s identified as the GamePlayerFramework, a C# variant of a C++-based malware regarded as PuppetLoader.
“This ‘framework’ consists of downloaders, launchers, and a set of plugins that present remote obtain and steal keystrokes and clipboard info,” the scientists stated.
Indications are that the DiceyF action is a comply with-on marketing campaign to Earth Berberoka with a retooled malware toolset, even as the framework is managed by two independent branches dubbed Tifa and Yuna, which come with unique modules of various amounts of sophistication.
Although the Tifa branch includes a downloader and a core part, Yuna is extra complicated in phrases of performance, incorporating a downloader, a set of plugins, and at minimum 12 PuppetLoader modules. That said, equally branches are thought to be actively and incrementally updated.
Irrespective of the variant utilized, the GamePlayerFramework, as soon as released, connects to a command-and-regulate (C2) and transmits info about the compromised host and the clipboard contents, just after which the C2 responds with one of 15 commands that enable the malware to seize management of the device.

This also features launching a plugin on the target system that can either be downloaded from the C2 server when the framework is instantiated or retrieved applying the “InstallPlugin” command sent by the server.
These plugins, in change, make it attainable to steal cookies from Google Chrome and Mozilla Firefox browsers, capture keystroke and clipboard information, set up digital desktop periods, and even remotely connect to the equipment in excess of SSH.
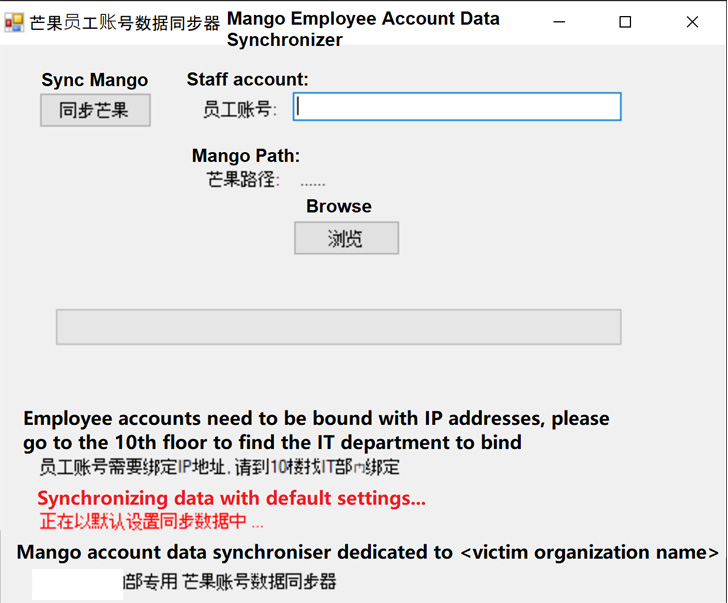
Kaspersky also pointed to the use of a malicious application that mimics a different software program known as Mango Personnel Account Information Synchronizer, a messenger app employed at the targeted entities, to drop the GamePlayerFramework in the network.
“There are many interesting qualities of DiceyF campaigns and TTPs,” the researchers reported. “The group modifies their codebase more than time, and develops features in the code all over their intrusions.”
“To make sure that victims did not become suspicious of the disguised implants, attackers received information and facts about specific businesses (these kinds of as the flooring the place the organization’s IT office is located) and incorporated it within graphic windows displayed to victims.”
Uncovered this short article intriguing? Adhere to THN on Facebook, Twitter and LinkedIn to study much more special articles we post.
Some areas of this post are sourced from:
thehackernews.com


 A Quick Guide for Small Cybersecurity Teams Looking to Invest in Cyber Insurance
A Quick Guide for Small Cybersecurity Teams Looking to Invest in Cyber Insurance