A China-connected authorities-sponsored risk actor has been noticed focusing on Russian speakers with an up to date model of a distant obtain trojan referred to as PlugX.
Secureworks attributed the attempted intrusions to a risk actor it tracks as Bronze President, and by the broader cybersecurity local community less than the monikers Mustang Panda, TA416, HoneyMyte, RedDelta, and PKPLUG.
“The war in Ukraine has prompted quite a few international locations to deploy their cyber capabilities to acquire perception about world-wide functions, political machinations, and motivations,” the cybersecurity business reported in a report shared with The Hacker Information. “This wish for situational recognition often extends to accumulating intelligence from allies and ‘friends.'”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Bronze President, energetic considering the fact that at the very least July 2018, has a heritage of conducting espionage operations by leveraging personalized and publicly offered instruments to compromise, sustain prolonged-expression access, and acquire facts from targets of curiosity.

Chief amongst its equipment is PlugX, a Windows backdoor that enables risk actors to execute a assortment of instructions on infected systems and which has been utilized by many Chinese state-sponsored actors around the yrs.
The most current findings from Secureworks propose an expansion of the same campaign beforehand thorough by Proofpoint and ESET last thirty day period, which has concerned the use of a new variant of PlugX codenamed Hodur, so labeled owing to its overlaps with a further edition referred to as THOR that emerged on the scene in July 2021.
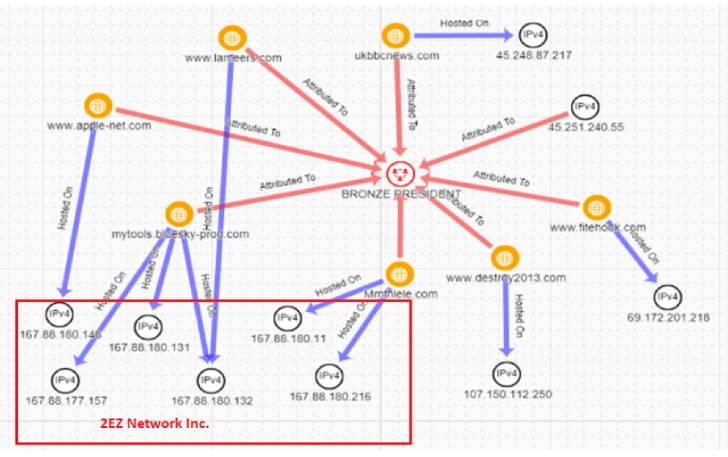
The attack chain commences with a malicious executable named “Blagoveshchensk – Blagoveshchensk Border Detachment.exe” that masquerades as a seemingly genuine doc with a PDF icon, which, when opened, prospects to the deployment of an encrypted PlugX payload from a distant server.
“Blagoveshchensk is a Russian metropolis near to the China border and is house to the 56th Blagoveshchenskiy Crimson Banner Border Guard Detachment,” the researchers said. “This connection indicates that the filename was picked to focus on officials or military personnel acquainted with the location.”
The actuality that Russian officials could have been the focus on of the March 2022 marketing campaign signifies that the menace actor is evolving its practices in response to the political scenario in Europe and the war in Ukraine.

“Concentrating on Russian-talking users and European entities indicates that the threat actors have received updated tasking that demonstrates the transforming intelligence collection specifications of the [People’s Republic of China],” the researchers reported.
The conclusions appear months following another China-based mostly nation-condition team recognized as Nomad Panda (aka RedFoxtrot) was joined with medium confidence to attacks in opposition to protection and telecom sectors in South Asia by leveraging nevertheless an additional model of PlugX dubbed Talisman.
“PlugX has been involved with different Chinese actors in the latest decades,” Trellix pointed out previous thirty day period. “This simple fact raises the concern if the malware’s code foundation is shared amongst distinctive Chinese point out-backed teams.”
“On the other hand, the alleged leak of the PlugX v1 builder, as described by Airbus in 2015, signifies that not all occurrences of PlugX are automatically tied to Chinese actors,” the cybersecurity company included.
Discovered this write-up attention-grabbing? Stick to THN on Fb, Twitter and LinkedIn to go through much more special material we submit.
Some components of this article are sourced from:
thehackernews.com

 Millions of Java Apps Remain Vulnerable to Log4Shell
Millions of Java Apps Remain Vulnerable to Log4Shell![[ebook] your first 90 days as mssp: 10 steps to](https://thecybersecurity.news/data/2022/04/eBook-Your-First-90-Days-as-MSSP-10-Steps-to-80x80.png)