The Chinese state-sponsored danger actor recognised as Stone Panda has been observed using a new stealthy an infection chain in its attacks aimed at Japanese entities.
Targets include things like media, diplomatic, governmental and general public sector organizations and think-tanks in Japan, in accordance to twin reviews published by Kaspersky.
Stone Panda, also named APT10, Bronze Riverside, Cicada, and Potassium, is a cyber espionage group recognized for its intrusions in opposition to corporations identified as strategically major to China. The menace actor is believed to have been lively given that at minimum 2009.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
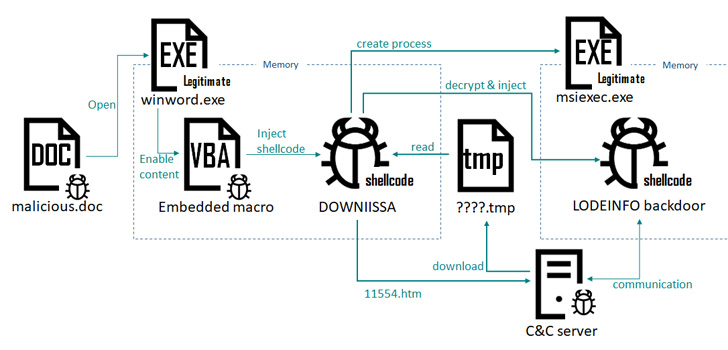
The most current established of attacks, noticed involving March and June 2022, require the use of a bogus Microsoft Term file and a self-extracting archive (SFX) file in RAR structure propagated via spear-phishing emails, major to the execution of a backdoor called LODEINFO.
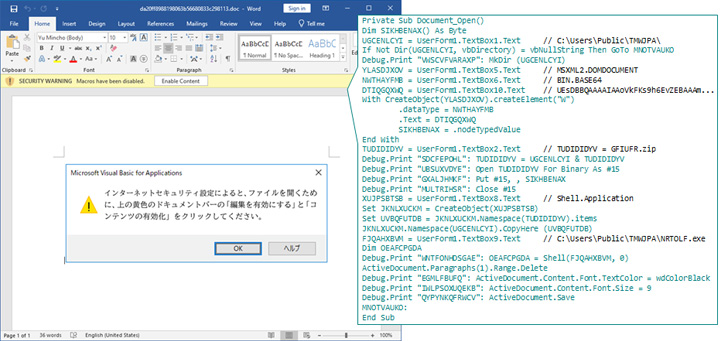
Whilst the maldoc calls for people to enable macros to activate the killchain, the June 2022 marketing campaign was uncovered to fall this process in favor of an SFX file that, when executed, displays a harmless decoy Phrase document to conceal the malicious activities.
The macro, after enabled, drops a ZIP archive that contains two information, one of which (“NRTOLF.exe”) is a legitimate executable from the K7Security Suite application that’s subsequently made use of to load a rogue DLL (“K7SysMn1.dll”) by means of DLL side-loading.
The abuse of the security software aside, Kaspersky stated it also uncovered in June 2022 a different first an infection strategy wherein a password-safeguarded Microsoft Term file acted as a conduit to produce a fileless downloader dubbed DOWNIISSA upon enabling macros.
“The embedded macro generates the DOWNIISSA shellcode and injects it in the existing method (WINWORD.exe),” the Russian cybersecurity enterprise reported.
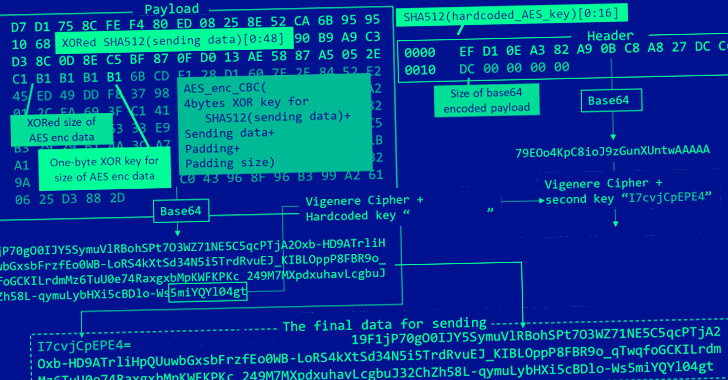
DOWNIISSA is configured to talk with a tough-coded distant server, using it to retrieve an encrypted BLOB payload of LODEINFO, a backdoor able of executing arbitrary shellcode, choose screenshots, and exfiltrate documents back to the server.

The malware, 1st viewed in 2019, has gone through several enhancements, with Kaspersky recognized six distinct versions in March, April, June, and September 2022.
The adjustments contain enhanced evasion approaches to fly beneath the radar, halting execution on machines with the locale “en_US,” revising the list of supported commands, and extending support for Intel 64-bit architecture.
“LODEINFO malware is up-to-date quite frequently and proceeds to actively concentrate on Japanese corporations,” the scientists concluded.
“The up-to-date TTPs and improvements in LODEINFO and connected malware […] point out that the attacker is specifically concentrated on creating detection, investigation and investigation tougher for security researchers.”
Found this posting attention-grabbing? Stick to THN on Facebook, Twitter and LinkedIn to read through more special written content we write-up.
Some elements of this posting are sourced from:
thehackernews.com

 Major security exploits expected to rise before New Year
Major security exploits expected to rise before New Year