A China-primarily based state-of-the-art persistent menace (APT) recognised as Mustang Panda has been joined to an ongoing cyberespionage marketing campaign making use of a beforehand undocumented variant of the PlugX remote entry trojan on contaminated machines.
Slovak cybersecurity company ESET dubbed the new model Hodur, owing to its resemblance to one more PlugX (aka Korplug) variant identified as THOR that came to light-weight in July 2021.
“Most victims are located in East and Southeast Asia, but a couple are in Europe (Greece, Cyprus, Russia) and Africa (South Africa, South Sudan),” ESET malware researcher Alexandre Côté Cyr said in a report shared with The Hacker News.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Recognized victims consist of research entities, internet provider vendors (ISPs), and European diplomatic missions mostly positioned in East and Southeast Asia.”
Mustang Panda, also known as TA416, HoneyMyte, RedDelta, or PKPLUG, is a cyber espionage team which is mostly recognised for concentrating on non-governmental companies with a unique target on Mongolia.
The newest campaign, which dates back again to at minimum August 2021, can make use of a compromise chain featuring an ever-evolving stack of decoy files pertaining to the ongoing gatherings in Europe and the war in Ukraine.
“Other phishing lures mention up to date COVID-19 travel limits, an approved regional assist map for Greece, and a Regulation of the European Parliament and of the Council,” ESET claimed. “The ultimate lure is a authentic document accessible on the European Council’s site. This reveals that the APT team powering this campaign is following current affairs and is in a position to effectively and swiftly react to them.”
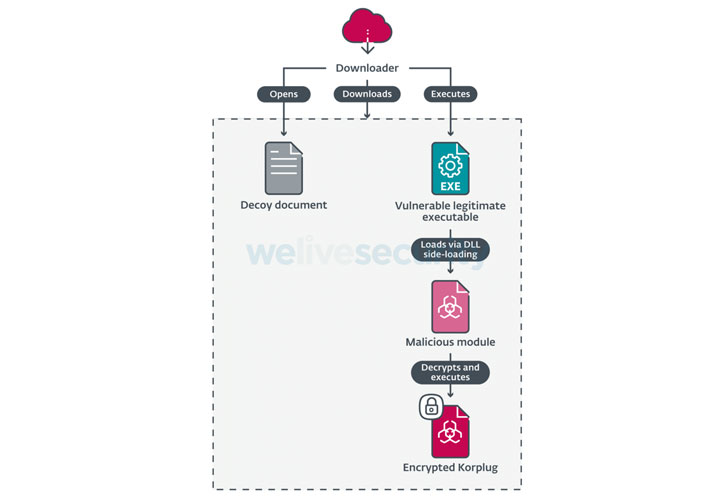
No matter of the phishing lure used, the infections culminate in the deployment of the Hodur backdoor on the compromised Windows host.
“The variant employed in this campaign bears quite a few similarities to the THOR variant, which is why we have named it Hodur,” stated. “The similarities include things like the use of the SoftwareCLASSESms-pu registry crucial, the similar format for [command-and-control] servers in the configuration, and use of the Static window class.”
Hodur, for its part, is outfitted to take care of a wide variety of instructions, enabling the implant to get considerable technique info, study and publish arbitrary files, execute instructions, and launch a distant cmd.exe session.
The findings from ESET line up with general public disclosures from Google’s Menace Analysis Team (TAG) and Proofpoint, both equally of which specific a Mustang Panda marketing campaign to distribute an up to date PlugX variant previously this month.
“The decoys utilized in this marketing campaign show once extra how immediately Mustang Panda is capable to respond to environment events,” Côté Cyr said. “This group also demonstrates an capacity to iteratively enhance its resources, such as its signature use of trident downloaders to deploy Korplug.”
Identified this write-up interesting? Observe THN on Fb, Twitter and LinkedIn to go through extra distinctive content we submit.
Some pieces of this report are sourced from:
thehackernews.com




 Medical Service Leaks 12,000 Sensitive Patient Images
Medical Service Leaks 12,000 Sensitive Patient Images