The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday extra the not too long ago disclosed Atlassian security flaw to its Recognised Exploited Vulnerabilities Catalog, based mostly on proof of active exploitation.
The vulnerability, tracked as CVE-2022-26138, fears the use of difficult-coded qualifications when the Thoughts For Confluence application is enabled in Confluence Server and Details Middle occasions.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“A remote unauthenticated attacker can use these qualifications to log into Confluence and obtain all content available to people in the confluence-people group,” CISA notes in its advisory.
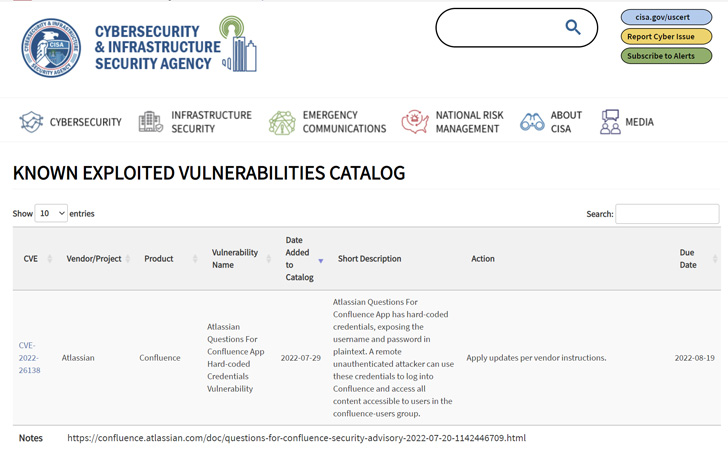
Depending on the web page constraints and the information a business has in Confluence, profitable exploitation of the shortcoming could lead to the disclosure of sensitive info.
While the bug was addressed by the Atlassian software package firm very last week in versions 2.7.38 and 3..5, it has because arrive below active exploitation, cybersecurity business Rapid7 disclosed this week.

“Exploitation endeavours at this place do not look to be very widespread, even though we hope that to alter,” Erick Galinkin, principal AI researcher at Immediate7, informed The Hacker News.
“The superior information is that the vulnerability is in the Questions for Confluence app and not in Confluence itself, which lowers the attack area considerably.”
With the flaw now included to the catalog, Federal Civilian Govt Department (FCEB) in the U.S. are mandated to apply patches by August 19, 2022, to reduce their publicity to cyberattacks.
“At this level, the vulnerability has been public for a fairly limited quantity of time,” Galinkin noted. “Coupled with the absence of meaningful write-up-exploitation exercise, we will not however have any menace actors attributed to the attacks.”
Uncovered this report intriguing? Observe THN on Fb, Twitter and LinkedIn to study additional exceptional articles we submit.
Some areas of this posting are sourced from:
thehackernews.com


 Congress Warns of US Court Records System Breach
Congress Warns of US Court Records System Breach