Cisco on Friday rolled out fixes for a medium-severity vulnerability impacting IOS XR Software package that it reported has been exploited in true-environment attacks.
Tracked as CVE-2022-20821 (CVSS score: 6.5), the issue relates to an open up port vulnerability that could be abused by an unauthenticated, remote attacker to hook up to a Redis occasion and achieve code execution.
“A productive exploit could allow the attacker to publish to the Redis in-memory database, generate arbitrary files to the container filesystem, and retrieve info about the Redis databases,” Cisco explained in an advisory.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

“Specified the configuration of the sandboxed container that the Redis instance operates in, a remote attacker would be unable to execute distant code or abuse the integrity of the Cisco IOS XR Application host system.”
The flaw, which it explained was identified through the resolution of a technical aid center (TAC) circumstance, impacts Cisco 8000 Collection routers working IOS XR Software program that has the wellness check RPM mounted and energetic.
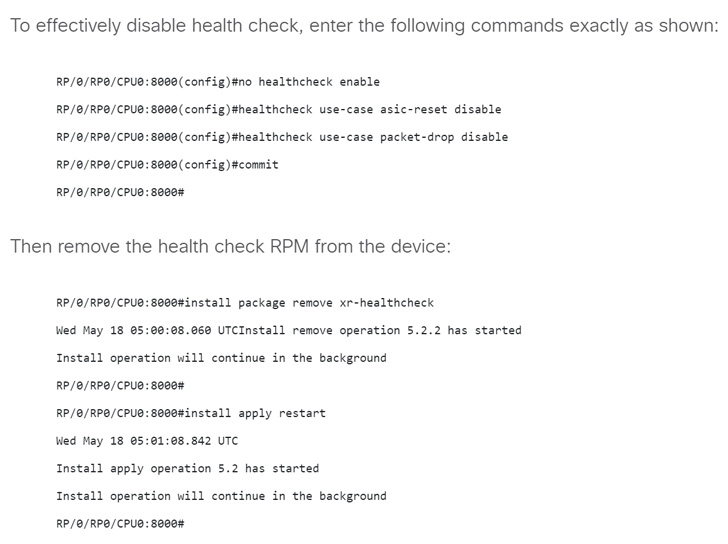
The networking gear maker also cautioned that it truly is informed of the tried exploitation of the zero-day bug previously this thirty day period. “Cisco strongly recommends that clients utilize suitable workarounds or enhance to a fastened software package release to remediate this vulnerability,” it included.
Located this post appealing? Abide by THN on Fb, Twitter and LinkedIn to study a lot more exclusive information we post.
Some parts of this article are sourced from:
thehackernews.com


 Pro-Russian Hackers Hit Critical Government Websites in Italy
Pro-Russian Hackers Hit Critical Government Websites in Italy