Cisco Programs has rolled out security updates for a critical security vulnerability affecting Unified Call Heart Administration Portal (Unified CCMP) and Unified Contact Middle Area Supervisor (Unified CCDM) that could be exploited by a distant attacker to consider handle of an impacted procedure.
Tracked as CVE-2022-20658, the vulnerability has been rated 9.6 in severity on the CVSS scoring system, and worries a privilege escalation flaw arising out of a absence of server-facet validation of user permissions that could be weaponized to make rogue Administrator accounts by publishing a crafted HTTP request.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“With these accounts, the attacker could access and modify telephony and user methods across all the Unified platforms that are involved to the susceptible Cisco Unified CCMP,” Cisco famous in an advisory revealed this week. ” To efficiently exploit this vulnerability, an attacker would want valid Superior Person qualifications.”
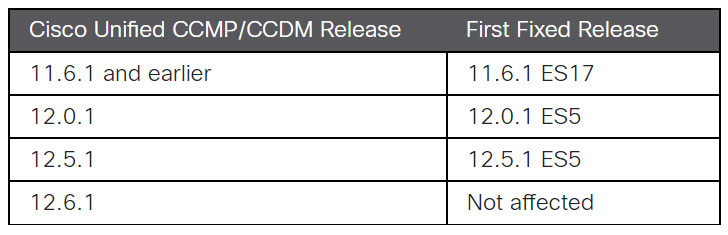
Unified CCMP and Unified CCDM solution variations 12.5.1, 12..1, and 11.6.1 and before jogging with default configuration are impacted, the networking products company claimed, including it located the issue as portion of a Specialized Support Heart (TAC) assistance situation. Edition 12.6.1 of the computer software is not afflicted.
Though there is no evidence that the security flaw has been exploited in real-earth attacks, it is advisable that people up grade to the most up-to-date edition to mitigate the risk connected with the flaws.
Observed this article interesting? Follow THN on Facebook, Twitter and LinkedIn to study far more unique content we post.
Some sections of this article are sourced from:
thehackernews.com


 Microsoft Yanks Buggy Windows Server Updates
Microsoft Yanks Buggy Windows Server Updates