A menace actor possible with associations to China has been attributed to a new source chain attack that consists of the use of a trojanized installer for the Comm100 Stay Chat software to distribute a JavaScript backdoor.
Cybersecurity firm CrowdStrike explained the attack produced use of a signed Comm100 desktop agent application for Windows that was downloadable from the company’s site.
The scale of the attack is at this time unknown, but the trojanized file is explained to have been discovered at companies in the industrial, health care, technology, production, insurance coverage, and telecom sectors in North America and Europe.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Comm100 is a Canadian provider of dwell audio/video clip chat and purchaser engagement computer software for enterprises. It promises to have much more than 15,000 buyers throughout 51 nations.

“The installer was signed on September 26, 2022 at 14:54:00 UTC making use of a valid Comm100 Network Company certificate,” the corporation observed, including it remained readily available until finally September 29.
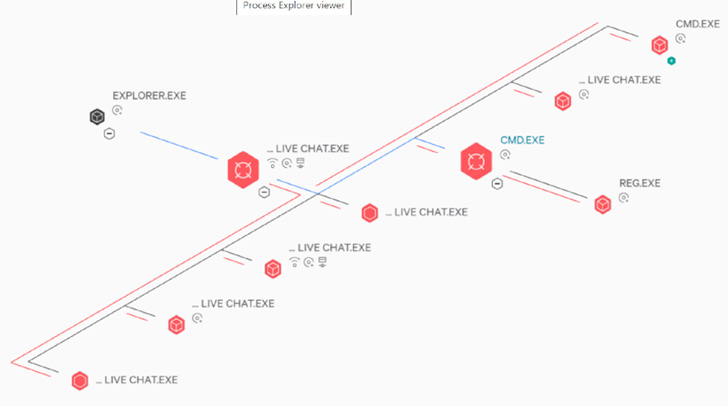
Embedded within the weaponized executable is a JavaScript-centered implant that executes a second-stage JavaScript code hosted on a distant server, which is built to supply the actor with surreptitious distant shell operation.
Also deployed as aspect of the article-exploitation activity is a destructive loader DLL named MidlrtMd.dll that launches an in-memory shellcode to inject an embedded payload into a new Notepad procedure.
Supply chain compromises, like that of SolarWinds and Kaseya, are turning out to be an more and more worthwhile tactic for threat actors to target a extensively-utilized program supplier to acquire a foothold in the networks of downstream consumers.
As of crafting, none of the security sellers flag the installer as malicious. Following responsible disclosure, the issue has considering the fact that been tackled with the release of an current installer (10..9).

CrowdStrike has tied the attack with average self esteem to an actor with a China nexus centered on the presence of Chinese-language feedback in the malware and the concentrating on of on the web gambling entities in East and Southeast Asia, an already recognized spot of interest for China-primarily based intrusion actors.
That explained, the payload sent in this action differs from other malware households previously discovered as operated by the group, suggesting an enlargement to its offensive arsenal.
The identify of the adversary was not disclosed by CrowdStrike, but the TTPs stage in the way of a menace actor named Earth Berberoka (aka GamblingPuppet), which earlier this yr was uncovered employing a phony chat application termed MiMi in its attacks towards the gambling marketplace.
Found this report intriguing? Adhere to THN on Fb, Twitter and LinkedIn to examine extra distinctive material we write-up.
Some components of this post are sourced from:
thehackernews.com


 Researchers Link Cheerscrypt Linux-Based Ransomware to Chinese Hackers
Researchers Link Cheerscrypt Linux-Based Ransomware to Chinese Hackers