Times soon after the Conti ransomware group broadcasted a pro-Russian message pledging its allegiance to Vladimir Putin’s ongoing invasion of Ukraine, a disgruntled member of the cartel has leaked the syndicate’s internal chats.
The file dump, printed by malware exploration team VX-Underground, is explained to have 13 months of chat logs involving affiliate marketers and directors of the Russia-affiliated ransomware team from January 2021 to February 2022, in a go which is predicted to provide unparalleled insight into the gang’s workings.
“Glory to Ukraine,” the leaker said in their concept.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
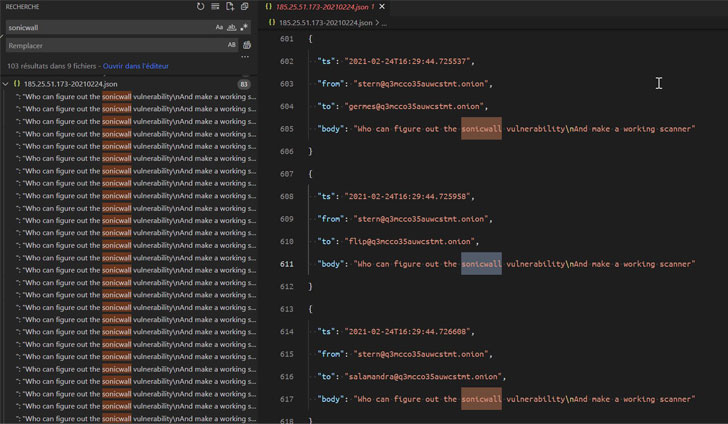
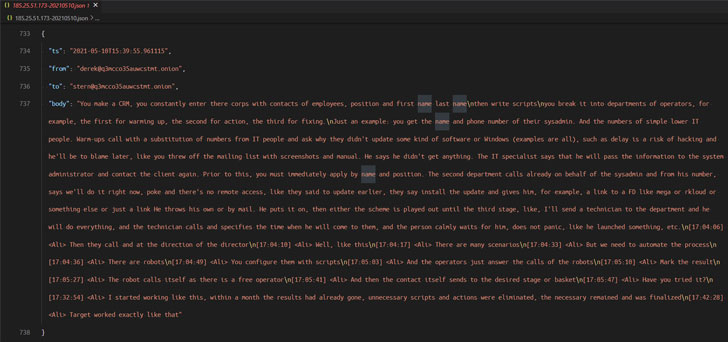
The leaked conversations show that Conti made use of faux front organizations to try to routine product demos with security firms like CarbonBlack and Sophos to get hold of code signing certificates, with the operators performing in scrum sprints to full the software progress duties.

Also, the messages affirm the shutdown of the TrickBot botnet final 7 days as properly as emphasize the Conti group’s near romantic relationship with the TrickBot and Emotet malware gangs, the latter of which was resurrected late very last calendar year by means of TrickBot.
A message despatched by 1 of the users of the team on February 14, 2022 goes: “TrickBot does not operate. The venture was closed.”
On best of that, the leaker is also considered to have produced the source code related with TrickBot’s command dispatcher and details collector modules, not to point out the ransomware group’s inner documentation.
The growth will come as the Russo-Ukrainian conflict has splintered the cybercrime underground into two warring factions, with a growing selection of hacking actors finding sides amongst the two international locations on the digital front.
The Conti workforce, in a web site post on its dark web portal previous 7 days, avowed its “entire guidance” to the Russian invasion, and threatened to retaliate in opposition to critical infrastructure if Russia is hit with cyber or armed forces attacks.
It, however, later backtracked, indicating, “we do not ally with any authorities and we condemn the ongoing war,” but reiterated that “We will use our sources in purchase to strike back if the effectively staying and security of peaceful citizens will be at stake owing to American cyber aggression.”
The ContiLeaks saga is section of a broader exertion by hacktivists and security allies, together with Ukraine’s “IT army,” to strike Russian web-sites, providers and infrastructure as a counter to Kremlin’s armed forces strikes. The volunteer hacking group, in messages shared on its Telegram channel, claimed that quite a few Russian websites and point out on the web portals have been felled by a barrage of DDoS attacks.
Independently, a group of Belarusian hackers recognised as the Cyber Partisans stated they staged an attack on the country’s educate network in an work to disrupt Russian troop actions into Ukraine, even though a further group termed AgainstTheWest_ mentioned was “standing versus Russia” and that it breached a range of internet sites and companies.
The Anonymous, for its section, also claimed duty for disrupting the sites of point out news companies RT, TASS, and RIA Novosti, as perfectly as sites of newspapers Kommersant, Izvestiya, and Forbes Russia magazine and the Russian oil big Gazprom.
If anything, the quickly evolving cyber war appears to have set other teams on alert, what with LockBit ransomware operators submitting a neutral message, stating “For us it is just company and we are all apolitical. We are only interested in income for our harmless and valuable operate.”
Found this article appealing? Follow THN on Facebook, Twitter and LinkedIn to study a lot more distinctive content we post.
Some sections of this report are sourced from:
thehackernews.com



 Trickbot Malware Gang Upgrades its AnchorDNS Backdoor to AnchorMail
Trickbot Malware Gang Upgrades its AnchorDNS Backdoor to AnchorMail