As numerous as 7 security vulnerabilities have been disclosed in PTC’s Axeda application that could be weaponized to gain unauthorized accessibility to health care and IoT devices.
Collectively known as “Access:7,” the weaknesses – three of which are rated Critical in severity – most likely have an affect on additional than 150 unit designs spanning around 100 various makers, posing a considerable source chain risk.
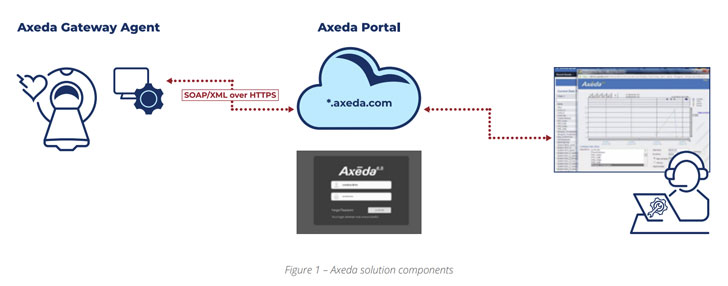
PTC’s Axeda solution incorporates a cloud platform that will allow unit makers to establish connectivity to remotely observe, regulate and company a large vary of linked equipment, sensors, and products by using what is actually named the agent, which is mounted by the OEMs in advance of the devices are marketed to shoppers.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Entry:7 could enable hackers to remotely execute malicious code, entry sensitive information, or alter configuration on health-related and IoT products jogging PTC’s Axeda remote code and management agent,” scientists from Forescout and CyberMDX explained in a joint report revealed today.
Of the 100 impacted device distributors, 55% belong to the healthcare sector, adopted by IoT (24%), IT (8%), monetary services (5%), and manufacturing (4%) industries. No much less than 54% of the prospects with gadgets managing Axeda have been recognized in the healthcare sector.
Apart from clinical imaging and laboratory equipment, susceptible equipment involve anything from ATMs, vending machines, income administration units, and label printers to barcode scanning systems, SCADA systems, asset checking and tracking solutions, IoT gateways, and industrial cutters.
The list of flaws is under –
- CVE-2022-25246 (CVSS score: 9.8) – The use of hard-coded qualifications in the AxedaDesktopServer.exe support that could allow remote takeover of a machine
- CVE-2022-25247 (CVSS rating: 9.8) – A flaw in ERemoteServer.exe that could be leveraged to mail specially crafted commands to obtain Remote code execution (RCE) and entire file program entry
- CVE-2022-25251 (CVSS score: 9.4) – Missing authentication in the Axeda xGate.exe agent that could be used to modify the agent’s configuration
- CVE-2022-25249 (CVSS rating: 7.5) – A listing traversal flaw in the Axeda xGate.exe agent which could enable a distant unauthenticated attacker to attain file procedure read entry on the web server
- CVE-2022-25250 (CVSS rating: 7.5) – A denial-of-company (DoS) flaw in the Axeda xGate.exe agent by injecting an undocumented command
- CVE-2022-25252 (CVSS rating: 7.5) – A buffer overflow vulnerability in the Axeda xBase39.dll part that could final result in a denial-of-provider (DoS)
- CVE-2022-25248 (CVSS rating: 5.3) – An data disclosure flaw in the ERemoteServer.exe company that exposes the are living party text log to unauthenticated parties
Productive exploitation of the flaws could equip attackers with capabilities to remotely execute destructive code to acquire complete handle of equipment, access delicate data, modify configurations, and shut down distinct providers in the impacted units.
The flaws, which have an affect on all versions of the Axeda Agent prior to 6.9.3, were being described to PTC on August 10, 2021 as aspect of a coordinated disclosure process that involved the U.S. Cybersecurity and Infrastructure Security Company (CISA), Health Information Sharing and Assessment Center (H-ISAC), and the Foods and Drug Administration (Food and drug administration).
To mitigate the flaws and reduce feasible exploitation, users are advised to enhance to Axeda agent version 6.9.1 develop 1046, 6.9.2 create 1049, or 6.9.3 develop 1051.
This is not the initially time critical security vulnerabilities mostly concentrating on healthcare methods have come to light-weight. In December 2020, CyberMDX disclosed “MDhex-Ray,” a intense flaw in GE Healthcare’s CT, X-Ray, and MRI imaging solutions that could result in the publicity of shielded well being facts.
“Accessibility:7 affects a answer bought to system companies that did not build their in-house remote servicing procedure,” the scientists stated. “This tends to make it a provide chain vulnerability and therefore it impacts lots of downstream suppliers and products.”
Identified this posting attention-grabbing? Follow THN on Facebook, Twitter and LinkedIn to go through additional distinctive content we article.
Some components of this posting are sourced from:
thehackernews.com



 Dirty Pipe Exploit Rings Alarm Bells in the Linux Community
Dirty Pipe Exploit Rings Alarm Bells in the Linux Community