Scientists have disclosed particulars about a now-patched critical flaw in the Go digital device that powers the Aptos blockchain network.
The vulnerability “can induce Aptos nodes to crash and bring about denial of service,” Singapore-primarily based Numen Cyber Labs reported in a technological generate-up published earlier this month.
Aptos is a new entrant to the blockchain area, which released its mainnet on Oct 17, 2022. It has its roots in the Diem stablecoin payment process proposed by Meta (née Fb), which also released a small-lived electronic wallet termed Novi.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The network is crafted employing a system-agnostic programming language known as Move, a Rust-based program that’s designed to carry out and execute smart contracts in a safe runtime environment, also acknowledged as the Shift Virtual Machine (aka MoveVM).
The vulnerability discovered by Numen Cyber Labs is rooted in the Shift language’s verification module (“stack_utilization_verifier.rs”), a component that validates the bytecode recommendations prior to its execution in MoveVM.

Precisely, it relates to an integer overflow vulnerability in the stack-primarily based Web3 programming language that could outcome in undefined habits and therefore crashes.
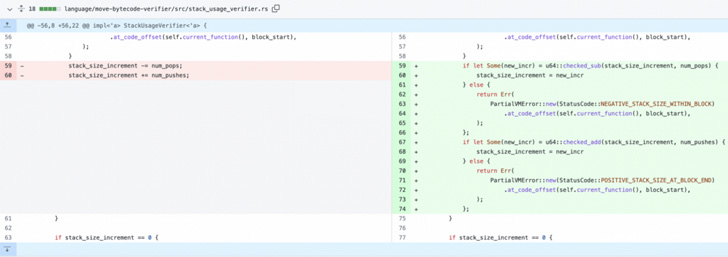
“Due to the fact this vulnerability takes place in the Go execution module, for nodes on the chain, if the bytecode code is executed, it will bring about a [Denial-of-Service] attack,” the cybersecurity organization described.
“In significant cases, the Aptos network can be entirely stopped, which will trigger incalculable problems, and have a severe impact on the stability of the node.”
Located this report appealing? Observe THN on Facebook, Twitter and LinkedIn to examine a lot more special articles we submit.
Some components of this short article are sourced from:
thehackernews.com


 New Phishing Campaign Targets Saudi Government Service Portal
New Phishing Campaign Targets Saudi Government Service Portal