Adobe on Sunday rolled out patches to incorporate a critical security vulnerability impacting its Commerce and Magento Open Supply merchandise that it said is currently being actively exploited in the wild.
Tracked as CVE-2022-24086, the shortcoming has a CVSS score of 9.8 out of 10 on the vulnerability scoring method and has been characterised as an “incorrect enter validation” issue that could be weaponized to realize arbitrary code execution.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
It can be also a pre-authenticated flaw, this means it could be exploited without the need of necessitating any qualifications. But the California-headquartered organization also pointed out that the vulnerability is only exploitable by an attacker with administrative privileges.
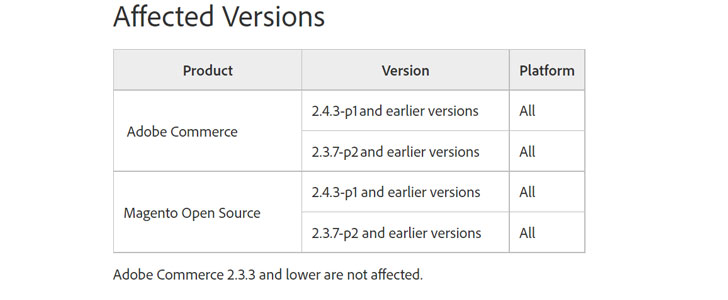
The flaw influences Adobe Commerce and Magento Open Source 2.4.3-p1 and before versions as properly as 2.3.7-p2 and before variations. Adobe Commerce 2.3.3 and reduce are not susceptible.
“Adobe is knowledgeable that CVE-2022-24086 has been exploited in the wild in pretty restricted attacks concentrating on Adobe Commerce retailers,” the company noted in an advisory revealed February 13, 2022.
The conclusions come as e-commerce malware and vulnerability detection corporation Sansec disclosed last week about a Magecart attack that compromised 500 web-sites managing the Magento 1 platform with a credit rating card skimmer made to siphon sensitive payment information and facts.
Identified this post exciting? Adhere to THN on Fb, Twitter and LinkedIn to read a lot more special content material we submit.
Some elements of this article are sourced from:
thehackernews.com




 Critical MQTT-Related Bugs Open Industrial Networks to RCE Via Moxa
Critical MQTT-Related Bugs Open Industrial Networks to RCE Via Moxa