As a lot of as 29 distinct router designs from DrayTek have been discovered as influenced by a new critical, unauthenticated, distant code execution vulnerability that, if correctly exploited, could guide to total compromise of the device and unauthorized accessibility to the broader network.
“The attack can be done without having person conversation if the management interface of the gadget has been configured to be internet struggling with,” Trellix researcher Philippe Laulheret reported. “A a single-simply click attack can also be carried out from in just the LAN in the default system configuration.”
Submitted beneath CVE-2022-32548, the vulnerability has obtained the most severity ranking of 10. on the CVSS scoring procedure, owing to its means to absolutely permit an adversary to seize handle of the routers.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

At its main, the shortcoming is the end result of a buffer overflow flaw in the web management interface (“/cgi-bin/wlogin.cgi”), which can be weaponized by a destructive actor by providing specially crafted input.
“The consequence of this attack is a takeover of the so-named ‘DrayOS’ that implements the router functionalities,” Laulheret said. “On devices that have an fundamental Linux running technique (this sort of as the Vigor 3910) it is then possible to pivot to the fundamental working program and build a trusted foothold on the device and area network.”
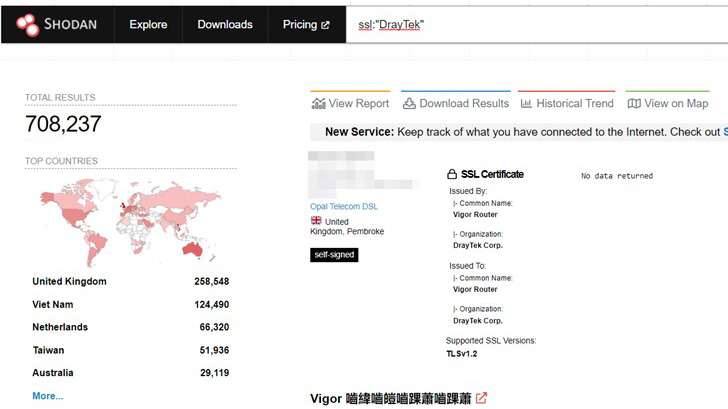
Over 200,000 units from the Taiwanese company are claimed to have the vulnerable company currently exposed on the internet and would involve no person conversation to be exploited.
The breach of a network appliance this sort of as Vigor 3910 could not only depart a network open to malicious actions this sort of as credential and intellectual assets theft, botnet exercise, or a ransomware attack, but also cause a denial-of-provider (DoS) problem.

The disclosure comes a minimal in excess of a thirty day period after it emerged that routers from ASUS, Cisco, DrayTek, and NETGEAR are under assault from a new malware termed ZuoRAT focusing on North American and European networks.
Though there are no indicators of exploitation of the vulnerability in the wild so considerably, it’s advised to apply the firmware patches as before long as feasible to secure against probable threats.
“Edge devices, such as the Vigor 3910 router, live on the boundary involving inside and external networks,” Laulheret pointed out. “As this sort of they are a primary concentrate on for cybercriminals and danger actors alike. Remotely breaching edge equipment can direct to a comprehensive compromise of the businesses’ inside network.”
Discovered this write-up intriguing? Abide by THN on Fb, Twitter and LinkedIn to read more unique information we submit.
Some parts of this posting are sourced from:
thehackernews.com


 New Woody RAT Malware Being Used to Target Russian Organizations
New Woody RAT Malware Being Used to Target Russian Organizations