VMware has rolled out patches to deal with a critical security vulnerability in vCenter Server that could be leveraged by an adversary to execute arbitrary code on the server.
Tracked as CVE-2021-21985 (CVSS rating 9.8), the issue stems from a lack of enter validation in the Virtual SAN (vSAN) Overall health Test plug-in, which is enabled by default in the vCenter Server. “A malicious actor with network access to port 443 might exploit this issue to execute instructions with unrestricted privileges on the fundamental operating procedure that hosts vCenter Server,” VMware mentioned in its advisory.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
VMware vCenter Server is a server management utility which is used to manage virtual machines, ESXi hosts, and other dependent parts from a single centralized location. The flaw affects vCenter Server versions 6.5, 6.7, and 7. and Cloud Foundation variations 3.x and 4.x. VMware credited Ricter Z of 360 Noah Lab for reporting the vulnerability.
The patch launch also rectifies an authentication issue in the vSphere Shopper that has an effect on Virtual SAN Well being Verify, Website Recovery, vSphere Lifecycle Supervisor, and VMware Cloud Director Availability plug-ins (CVE-2021-21986, CVSS score: 6.5), therefore allowing an attacker to have out steps permitted by the plug-ins without any authentication.
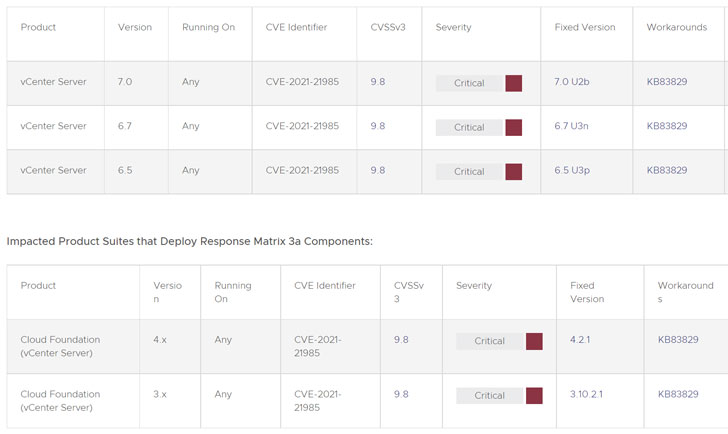
Whilst VMware is strongly recommending customers to implement the “crisis transform,” the company has released a workaround to established the plug-ins as incompatible. “Disablement of these plug-ins will final result in a loss of administration and checking capabilities presented by the plug-ins,” the business mentioned.
“Organizations who have positioned their vCenter Servers on networks that are right obtainable from the Internet […] ought to audit their devices for compromise,” VMware additional. “They should also consider methods to apply more perimeter security controls (firewalls, ACLs, etc.) on the management interfaces of their infrastructure.”
CVE-2021-21985 is the second critical vulnerability that VMware has rectified in the vCenter Server. Earlier this February, it solved a remote code execution vulnerability in a vCenter Server plug-in (CVE-2021-21972) that could be abused to run commands with unrestricted privileges on the fundamental running program hosting the server.
The fixes for the vCenter flaws also come following the enterprise patched a different critical remote code execution bug in VMware vRealize Business for Cloud (CVE-2021-21984, CVSS score: 9.8) due to an unauthorized endpoint that could be exploited by a destructive actor with network access to run arbitrary code on the equipment.
Formerly, VMware experienced rolled out updates to remediate numerous flaws in VMware Carbon Black Cloud Workload and vRealize Operations Manager methods.
Discovered this article interesting? Follow THN on Facebook, Twitter and LinkedIn to go through far more exceptional content we write-up.
Some components of this short article are sourced from:
thehackernews.com


 Security pros rely on peer groups and open communication for help with stress
Security pros rely on peer groups and open communication for help with stress