SonicWall has unveiled security updates to comprise a critical flaw throughout many firewall appliances that could be weaponized by an unauthenticated, remote attacker to execute arbitrary code and trigger a denial-of-support (DoS) ailment.
Tracked as CVE-2022-22274 (CVSS rating: 9.4), the issue has been described as a stack-dependent buffer overflow in the web administration interface of SonicOS that could be induced by sending a specifically crafted HTTP ask for, major to distant code execution or DoS.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
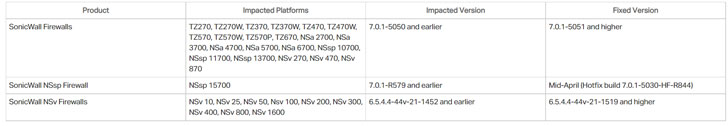
The flaw impacts 31 distinct SonicWall Firewall products managing versions 7..1-5050 and before, 7..1-R579 and earlier, and 6.5.4.4-44v-21-1452 and previously. ZiTong Wang of Hatlab has been credited with reporting the issue.
The network security corporation mentioned it’s not knowledgeable of any instance of energetic exploitation in the wild leveraging the weak spot, and that no evidence-of-strategy (PoC) or destructive use of the vulnerability has been publicly described to date.
That stated, people of the afflicted appliances are encouraged to utilize the patches as quickly as doable to mitigate opportunity threats. Until the fixes can be set in put, SonicWall is also recommending customers to restrict SonicOS administration entry to trustworthy resource IP addresses.
The advisory arrives as cybersecurity company Sophos cautioned that a critical authentication bypass vulnerability in its firewall product (CVE-2022-1040, CVSS rating: 9.8) has been exploited in lively attacks in opposition to pick organizations in South Asia.
Discovered this short article interesting? Observe THN on Facebook, Twitter and LinkedIn to read through a lot more distinctive material we publish.
Some components of this post are sourced from:
thehackernews.com




 Log4JShell Used to Swarm VMware Servers with Miners, Backdoors
Log4JShell Used to Swarm VMware Servers with Miners, Backdoors