Getty Visuals
Cyber attackers are investing longer inside business methods just after hacking them, a new report has revealed.
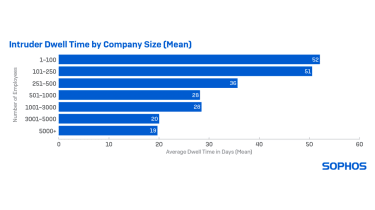
Rogue actors who do not use ransomware are shelling out the most time inside compact corporations with the common dwell time noticed to be 51 days in organisations with much less than 250 employees. Attackers targeting larger (3,000 – 5,000 workforce) organisations devote on normal just 20 days inside.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
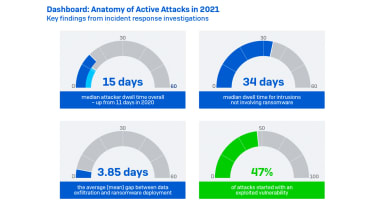
The figures for ransomware criminals are a great deal reduced, with the ordinary dwell time inside of a business falling to just 15 days.
UK cyber security firm Sophos explained these figures, taken from knowledge in 2021, total to a 36% boost in attacker dwell time compared to the earlier 12 months.
Sophos
More time dwell times could be indicative of the growing attractiveness of preliminary access brokers (IABs) in the cyber security landscape, the firm explained.
IABs are on-line companies that are often marketed on the deep web advertising remote obtain to organizations to possible hackers and charging them in accordance to the time spent inside of the procedure.
Extended dwell moments not only enable attackers to start much more attacks but also open up up victims to attacks from multiple risk actors, Sophos explained.
The company’s forensic analyses discovered situations of IABs, cryptominers, and a number of ransomware operators focusing on enterprises concurrently.
Sophos claimed this escalating pattern of hackers just spending for accessibility fairly than developing their exploits, for example, demonstrates the increasing ‘professionalism’ of cyber attackers and is fuelling a thriving ransomware-as-a-services (RaaS) marketplace.
“The world of cybercrime has turn out to be very varied and specialised. IABs have formulated a cottage cybercrime sector by breaching a concentrate on, undertaking exploratory reconnaissance or installing a backdoor, and then selling the switch-crucial obtain to ransomware gangs for their individual attacks,” said John Shier, senior security advisor at Sophos.
“In this more and more dynamic, speciality-based mostly cyberthreat landscape, it can be tricky for organisations to continue to keep up with the ever-shifting applications and strategies attackers use. It is essential that defenders comprehend what to seem for at each and every phase of the attack chain, so they can detect and neutralise attacks as quick as doable.”
Sophos
In addition to the pervasive reliance on IABs, Sophos’ analysis of cyber attacks uncovered that the second of the most influential threats was the ongoing exploitation of the ProxyLogon and ProxyShell vulnerabilities in Microsoft Exchange servers.
Microsoft reported this 7 days that it had to hold off the improvement of the following model of Microsoft Trade by 4 a long time thanks to assigning so quite a few specialists to boost the security of the mail and calendaring assistance in the wake of mass exploitation final 12 months.
Sophos reported the bugs led to a important selection of incidents it observed throughout 2021 and that there are probable to be several related breaches of which enterprises are continue to unaware.
The implantation of web shells and backdoors is probably to go unnoticed and the accessibility they provide could later be bought to keen bidders in the IAB marketplace, it reported.
Other broader findings in the company’s Lively Adversary Playbook report exposed that knowledge exfiltration was considerably extra common in ransomware incidents than in former several years, with the average time taken for actors to pull info from victims dropping from 4.28 to 1.84 days.
The pattern speaks to the rising pattern in ransomware of double extortion – a strategy which sees the victim’s devices corrupted, as properly as information stolen with the danger of facts leakage if the ransom is not paid.
Some elements of this posting are sourced from:
www.itpro.co.uk


 Attackers Use Public Exploits to Throttle Atlassian Confluence Flaw
Attackers Use Public Exploits to Throttle Atlassian Confluence Flaw